Encryption is a hot topic in the news, what with the government threatening to ban it in the interests of national security and the nasty WannaCry ransomware causing widespread chaos.
But there are plenty of non-criminal reasons to encrypt your data, and protecting your files, messages and browsing habits from prying eyes needn’t mean you’ve got something to hide. After all, it’s nobody else’s business what you say and does on your PC, phone and on the web.
In this “A Complete Essential Guide to Encrypting Your Data” Guide we reveal the best free ways to encrypt everything in your digital life, and explain why you might want to do so.
What we are going to Cover in this Data Encryption Guide:-
- How to secure your communications
- How to encrypt files and folders
- prevent anyone from spying on your browsing (and that includes your ISP)
- How to protect all your devices
- How Encryption actually works
- A data encryption standard algorithm
What is encryption?
Encryption is the process of encoding messages and information so they can only be accessed by authorised parties, usually via a key that’s generated using an algorithm. The encrypted data can only be decrypted by another party in possession of the key.
Are there different types of encryption?
The two main types of encryption are symmetric and asymmetric:- symmetric uses the same key for both encryption and decryption; asymmetric uses a combination of a private and a public key.
The private key is kept secret by the owner while the public key is shared for anyone to use to encrypt messages – PGP (Pretty Good Privacy) is one of the most widely used public-key encryption methods. Data encrypted with the public key can only be decrypted with a corresponding private key.
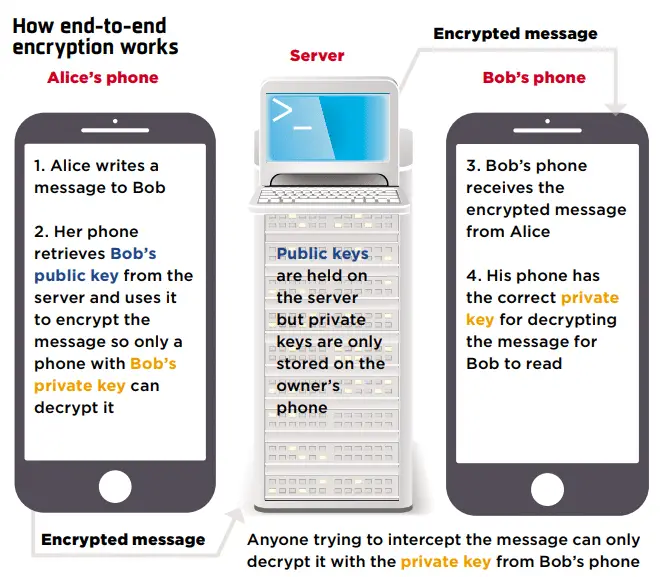
What is end-to-end encryption?
End-to-end encryption – as used by messaging services such as WhatsApp and iMessage, as well as online banks and security companies – is asymmetric.
It is commonly used to prevent third parties from intercepting and reading sensitive and private data because it virtually eliminates the risk of messages and documents falling into the wrong. hands.
Anyone who intercepts the encrypted data without the private key will only see gobbledegook or nothing at all
Are backdoors possible in Encryption?
No. Encryption is binary, so either something is encrypted and therefore secure from everyone, or it’s not. There is no in-between.
WhatsApp’s end-to-end encryption is there for a reason: to prevent cybercriminals, hackers, and snoopers from seeing what users are sending each other. It’s so effective that WhatsApp itself is unable to see the
content of messages.
The only way to break encryption by introducing a ‘backdoor’ would be to ditch the encryption altogether. The only other option is to ban all services that use end-to-end encryption, but this would only drive terrorists and criminals to find alternative tools.
Why don’t more companies use encryption?
That’s a question for those companies to answer. The technology is certainly there. Even Google, which is increasingly forcing websites to use encrypted HTTPS connections or else slip down its search results, only encrypts your Gmail messages on its own servers and not during transit.
Similarly, most Android devices aren’t encrypted by default, whereas all passcode-protected iPhones and iPads are. Indeed, Apple caused controversy last year when it refused to let the FBI gain access to a password-protected iPhone belonging to a gunman.
How do I ensure that my data is encrypted?
Well, that’s the purpose of this essential guide. Most encryption tools are free and very straightforward to use, and we’ve rounded up what we believe are the very best available. It’s surprising
how much content – both on the web and on your PC – remains unencrypted, when it so easily could be, so we hope the advice in this feature helps to put your mind at rest about keeping your data secure and private.
Can I encrypt anything?
Just about, although some websites limit the use of third-party encryption tools. We think you’ll be pleasantly surprised at all the different types of data that can be encrypted nowadays. Naturally, we’re not encouraging you to encrypt other people’s files without their permission, which would also require devious malware-writing skills!
1. File and Folder Encryption
1.1 Encrypt your plain text
Plain text is fine for jotting down notes, but it’s not appropriate for sensitive information such as a list of passwords, or your bank or credit card details.
However, many people use it for just such purposes: indeed, Chrome even includes a feature to export a list of your passwords in plain-text format.
Fortunately, there are numerous programs you can use to secure these confidential details to stop anyone reading them.
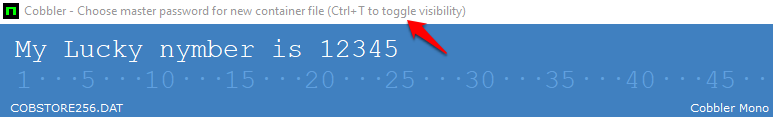
One of our favorites is Cobbler (Download Now), a tiny tool that encrypts your notes and is very easy to use – just run the software, enter
a master password and type in the text you want to protect.
Another program worth looking at is Dalenryder Password Generator (Download Now). This is a security tool that creates and manages passwords and PINs, but also includes a powerful Encryption Tool that can secure text.
As is the case with most encryption, when securing an Office file in this way, be careful not to lose or forget the password because there’s no way of recovering it. Anyone opening the locked file will be prompted to enter the correct password to gain access.
1.3 Create secure PDF files in Office
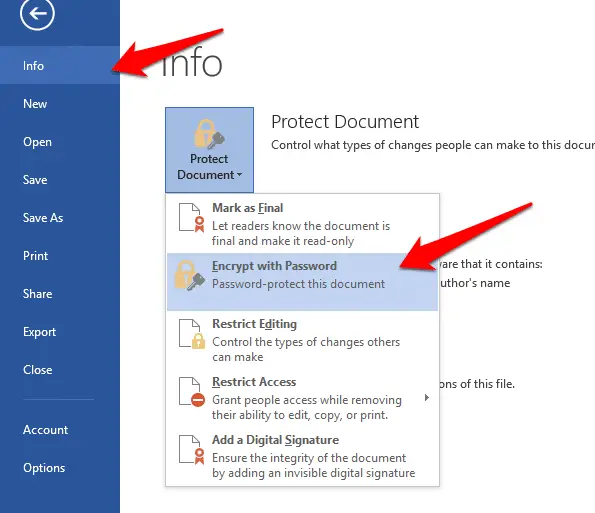
Microsoft Office lets you save documents directly to PDF format: just click File, Save As and select PDF in the ‘Save as type’ box.
To encrypt the file at the same time, so that unauthorized people can’t view its contents, click the Options box underneath.
Under PDF Options, tick the option to ‘Encrypt the document with a password’.
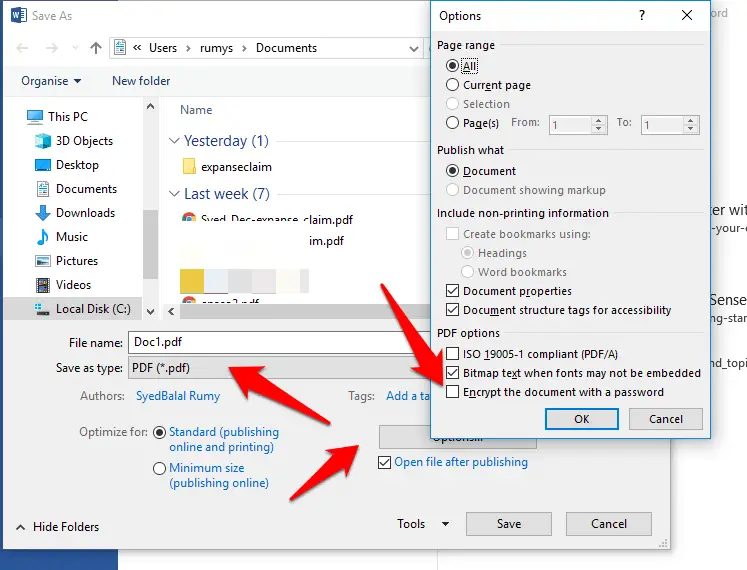
You’ll then be asked to enter a password twice. This needs to be between six and
32 characters in length.
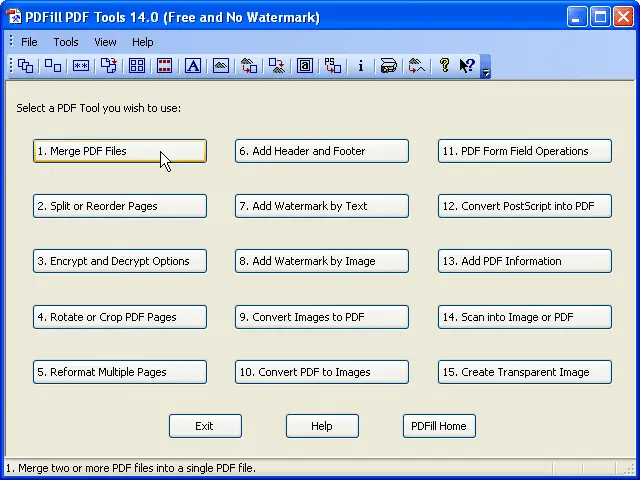
1.4 Encrypt PDF files using PDFill Tools
PDFill Tools (Download Now) offers a selection of useful functions for PDFs, including the ability to encrypt or decrypt your files.
It supports both Adobe Standard 40-bit and Adobe Advanced 128-bit encryption, and password-protects PDF files to prevent them from being printed, copied, changed, filled, extracted, signed or merged.
1.5 Hide and encrypt files and folders
You can keep personal files on your computer safe from prying eyes by using Wise Folder Hider (Download Now).
This free tool can hide files, folders and even connected USB drives so they aren’t visible in Windows Explorer unless you ‘unhide’ them by entering a password in the software.
Upgrading to the Pro edition for £19.32 lets you encrypt your files and folders, as well as simply hiding them, making it almost impossible for snoopers to access your private content.
1.6 Encrypt files stored in the cloud
Most people keep at least some of their important personal data in the cloud using online-storage services such as Dropbox, Google Drive and OneDrive.
If you’re concerned about how safe your files are in these services, you can secure them using the excellent tool Boxcryptor (www.boxcryptor.com).
This is free for personal use and supports more than 20 popular cloud storage providers. It’s available for Windows, MacOS, iOS, Android, BlackBerry and Chrome.
If you want to send a private file to someone over the internet, you should encrypt it beforehand. There are lots of ways to do this, but Secureshare (securesha.re) is one of the easiest.
[caption id="attachment_5009" align="aligncenter" width="542"]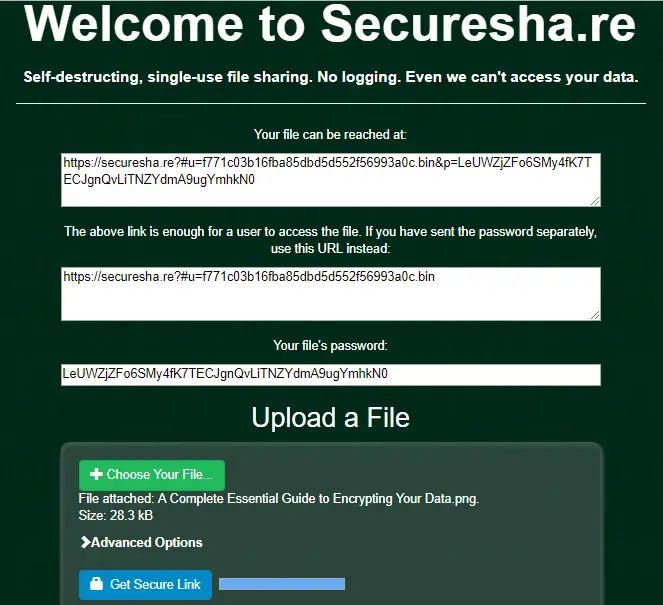 Secureshare lets you encrypt files without
Secureshare lets you encrypt files withoutdownloading any software
This website encrypts the file on your PC using 128-bit AES encryption before
uploading it to the web server and generating a self-destructing URL and password. Send both to your recipient (preferably using separate means, for extra security) and they’ll be able to download and unlock the file. You can select the number of times the file can
be downloaded or how long it’s available for.
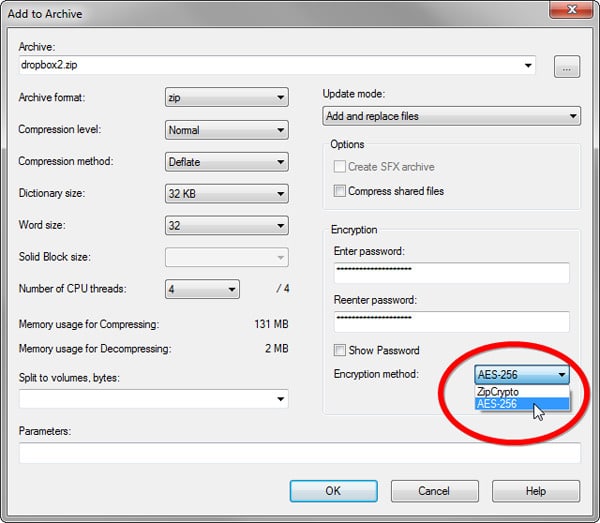
1.8 Encrypt compressed archives
Whether you want to encrypt a few files for emailing or archive a large amount of content for secure safekeeping, 7-Zip (www.7-zip.org) is the perfect tool for the job. Add
some files to the free compression tool and enter a password to lock the archive.
The program can encrypt both 7z and ZIP files using powerful AES-256 or ZipCrypto (ZIP only) methods. The AES option lets you encrypt the file names as well to prevent people guessing their contents.
2. Communication Encryption
2.1 Chat completely securely in WhatsApp
WhatsApp (www.whatsapp.com) uses end-to-end encryption to keep your messages private. WhatsApp’s protection means that, provided you and the person you’re chatting with are using the latest version of the app, all communications are secure and not even WhatsApp itself can see them.
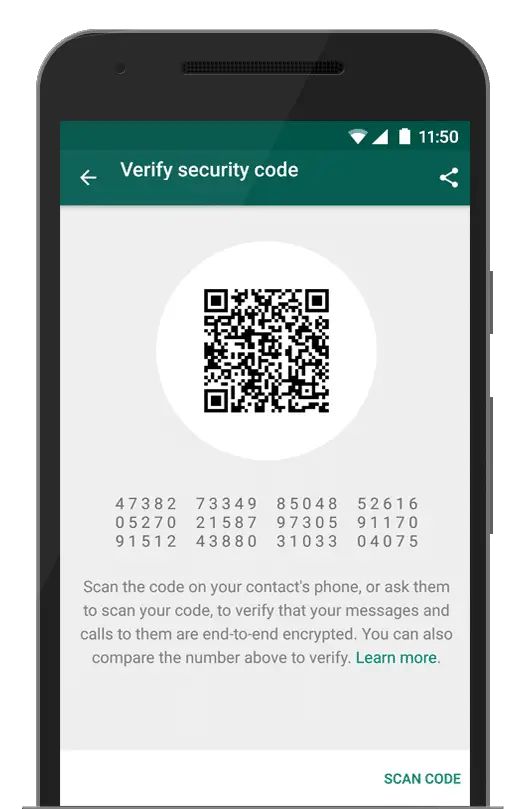
Encryption is turned on in the app by default – there’s no need to enable it manually. However, if you want to check that your messages are secure, tap the three-dot menu in the top-right corner, select ‘View contact’ and under Encryption, you should see a notice stating that all chat and calls are secure.
To verify this, click the note and scan the displayed QR code on your contact’s phone, or vice versa.
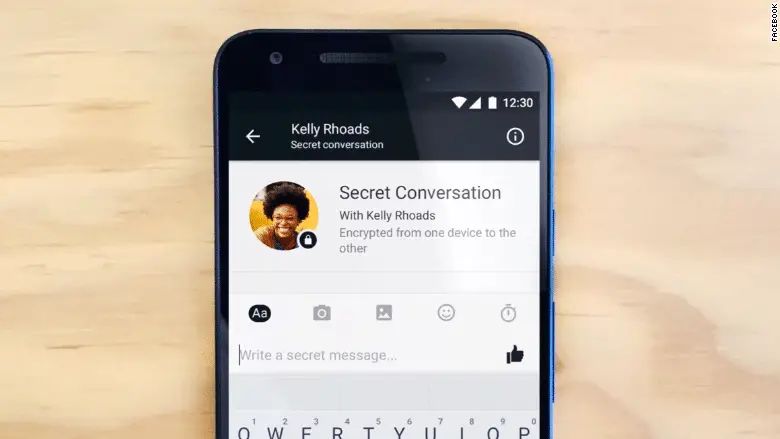
2.2 Have Secret Conversations in Messenger
Secret Conversations is a useful hidden feature in Facebook Messenger for Android and iOS that lets you send end-to-end encrypted messages to your friends.
The option isn’t enabled by default and you have to start a new private conversation – rather than just continue an existing thread – to use it. Also, it doesn’t work in group chats.
To start a secret conversation, tap your profile photo and scroll down to Secret Conversations. Open this option and make sure the feature is turned on
(enable it, if it isn’t). Next, tap the New Message button and select the Secret link in the top-right corner. Choose a friend from your contacts and start writing a message. The recipient has to agree to enter a Secret Conversation with you.
2.3 Text and call securely using Signal
A growing number of chat apps – including the aforementioned WhatsApp and Facebook – use end-to-end encryption to keep your conversations private, but Signal (whispersystems.org) is more secure than most. This free app, which is used and recommended by NSA whistleblower Edward Snowden, doesn’t store information about its users and lets you chat securely to contacts in your existing phone and address book.
Available for both iOS and Android, the app lets you send hack-proof text, and picture and video messages to individuals or groups, and also make secure phone calls. Most recently, the developer added support for end-to-end encrypted video calls.
2.4 Secure your Gmail messages
Although Gmail offers encryption over an HTTPS connection when you’re reading and writing messages, it doesn’t encrypt them while they’re in transit.
You can significantly increase your privacy by installing the CryptUp (cryptup.org) extension for Chrome and Firefox, which secures messages and attachments sent through Gmail in your browser using PGP (Pretty Good Privacy) end-to-end encryption. It
works by adding a Secure Compose button to Gmail so you can quickly send secure messages whenever you need to.
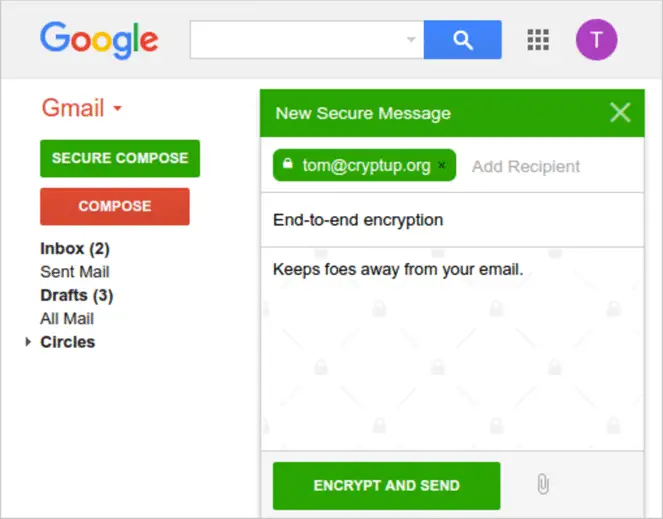
If your recipient doesn’t have CryptUp installed, or any other email encryption for that matter, you can secure your messages or files with a password. CryptUp’s developer is planning to release Android and iOS apps, along with an Outlook add-in, later this year.
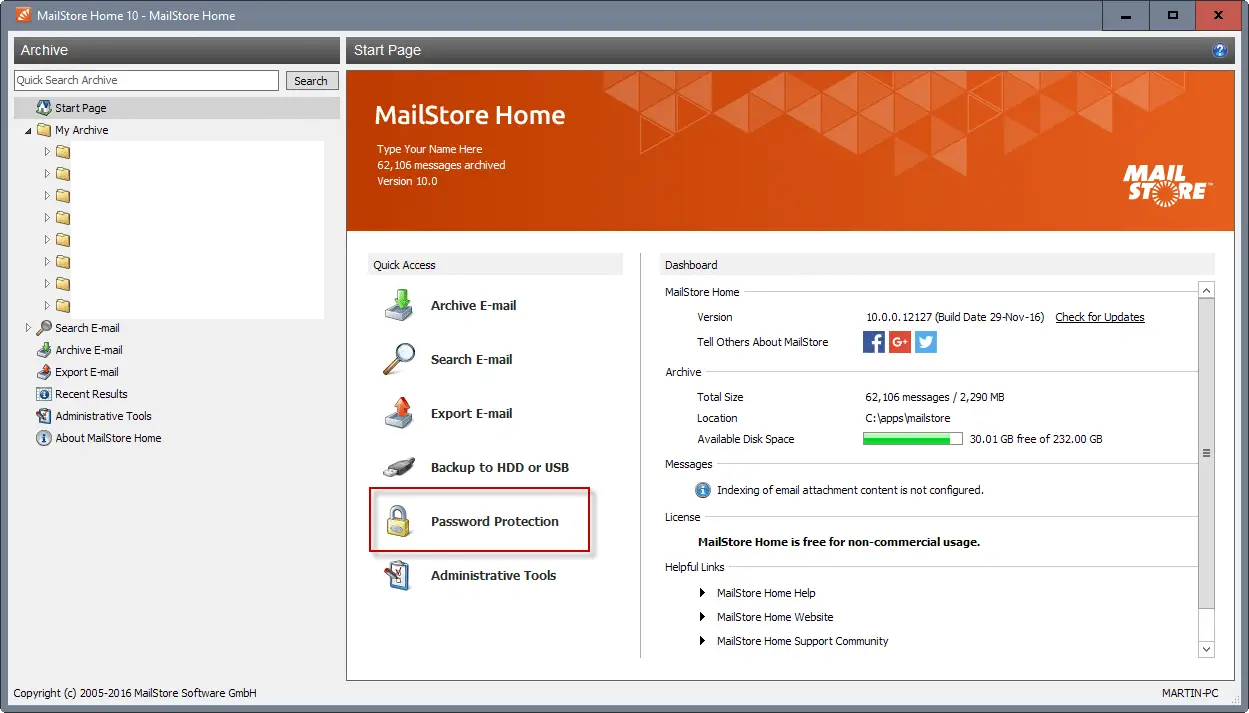
2.5 Encrypt your email backups
MailStore Home backs up all your emails and works with any mail provider including Gmail and Outlook.com. Just select the service(s) to back up and it will get to work. You can password-protect the archives, and the software fully encrypts all databases to make it impossible for anyone other than yourself to view the messages.
3. Browsing Encryption
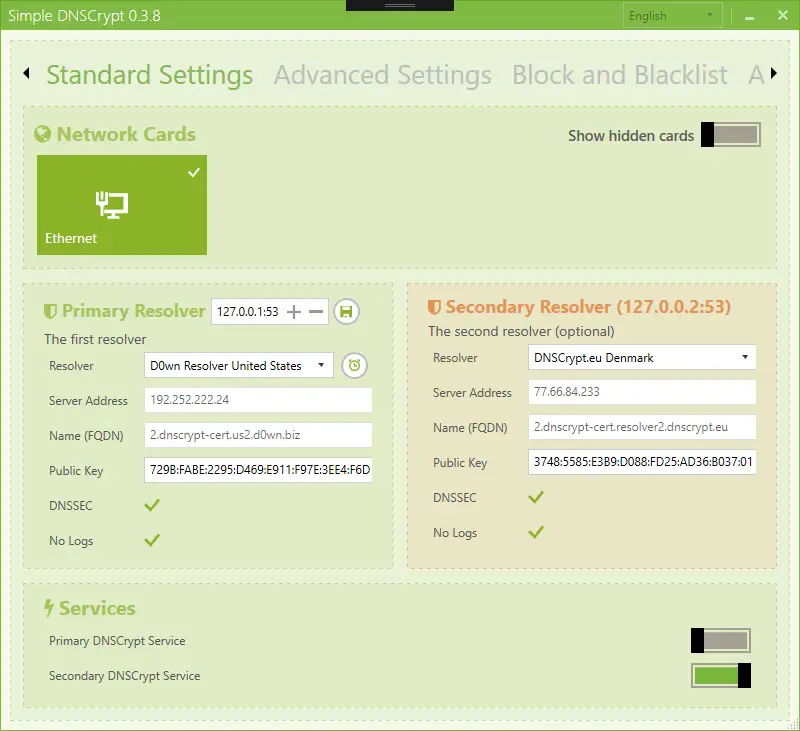
3.1 Encrypt your DNS requests
DNS (Domain Name System) is the service used to translate site names into IP addresses
that web servers and internet routers can understand. When you type a website name into your browser, a DNS server will look up the IP address that’s linked to it.
Unfortunately, attackers can eavesdrop on these requests to see which sites you’re visiting, or spoof DNS services and redirect you to a fake site.
Simple DNSCrypt (simplednscrypt.org) is a useful free tool that encrypts your
DNS requests to make sure nothing is interfered with, and to stop hackers stealing your data.
If you don’t want’s to use Software use Quad9 DNS. Check my article for this Quad9 DNS: Internet Security and Privacy in a Few Easy Steps
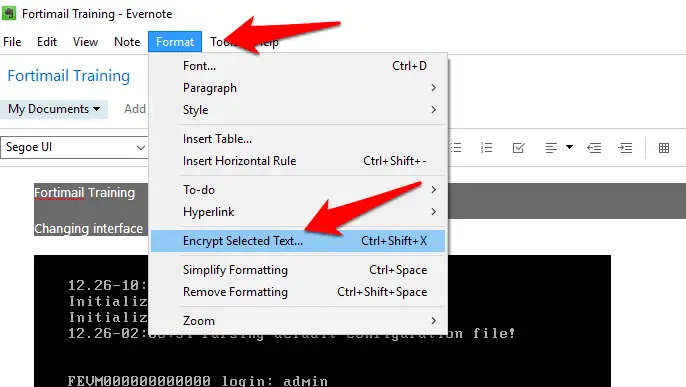
3.2 Encrypt content inside Evernote
If you use Evernote to store information – such as content from the web, personal notes or account details – you can encrypt anything that’s for your eyes only. Just open the note, highlight the part you want to encrypt, right-click it and choose to Encrypt Selected Text.
When prompted, enter a passphrase to lock the section. When you want to view
that text in future, click it and select ‘Show encrypted text’, then enter the passphrase. You can’t encrypt an entire note or notebook.
3.3 Always access secure versions of sites
A growing number of websites now offer the secure HTTPS (Hyper Text Transfer Protocol Secure) version by default and will switch you to it automatically if you try to go to the non-secure HTTP version. This protocol encrypts your data to stop snoopers, including your ISP, from being able to tell which pages you visit on a site.
However, not every website automatically redirects you, which is where HTTPS Everywhere comes in. This essential add-on for Chrome, Firefox and Opera automatically send your browser to the secure version of a site – if it exists.
In other words, if you only type in the basic address, you’ll still end up on the secure site. It’s updated regularly with new rules to cover additional sites and lets you block all unencrypted requests by default. HTTPS Everywhere can also be installed in Firefox for Android.
3.4 Hide your searches with a duck and a bear
Searches performed in Incognito or Private Browsing mode aren’t secret because, although the details of what you’ve searched for aren’t recorded on your PC or mobile device, the search provider (Google or Bing, for example) still keeps a record of them.
The best way to hide your searches is to use a VPN tool such as TunnelBear (www
.tunnelbear.com) to disguise your browsing location.
You need to log out of your Google or Microsoft account before running any searches or use DuckDuckGo (duckduckgo.com) instead, so your searches aren’t stored. One important note: you may have used encrypted.google.com in the past, but don’t make the mistake of thinking your searches there are any more secure.
This is an outdated redirect that was in use before Google switched all searches to the secure HTTPS protocol.
You’re just as safe using the regular Google search these days.
4. Device Encryption
4.1 Add a secure external drive
If you have a lot of personal files that you don’t want falling into the wrong hands, you can store them on a PINauthenticated, tamper-proof USB drive.
The diskAshur Pro 2 range (istorage-uk.com) offers drives in 500GB, 1TB and 2TB capacities, and uses XTS-AES 256-bit hardware encryption. You lock and unlock the drives by typing a PIN on the keypad on the front. The drive automatically locks itself after a period of inactivity and can “self-destruct” if someone tries to break in. The drives
are priced from £209.
The same company also sells secure USB flash drives with a built-in keypad that work in the same way. These cost from £69 for an 8GB drive.
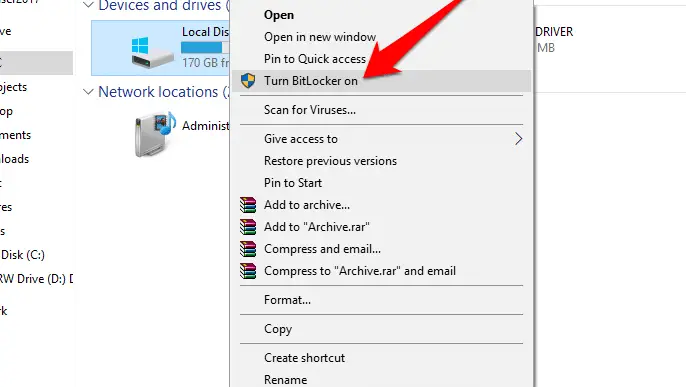
4.2 Secure your hard drive with BitLocker
BitLocker can protect your files and folders from unauthorised access by locking your drives. The feature was first introduced in Windows Vista and has been included in all subsequent updates of Microsoft’s OS, although it’s only available in the Ultimate and Enterprise editions of Windows 7; the Pro and Enterprise editions of Windows 8+; and the Pro, Enterprise, and Education editions of Windows 10.
The tool scrambles the contents of your drive and then unscrambles it when you enter your password – so if your computer gets stolen, your data will still be safe.
To use it, either right-click a drive letter in File Explorer and select ‘Turn BitLocker on’; or type BitLocker into the Search box, launch the Manage BitLocker control panel, and turn the feature on or off for any drive there.
4.3 Secure everything you do your PC
Tails (tails.boum.org) – The Amnesiac Incognito Live System – is a privacy-focused live Linux operating system that you can boot into from a DVD, USB memory stick or SD card. Use it to encrypt your files, emails and instant-messaging chats, and browse the web
anonymously. You can boot into it whenever you need privacy and it’s very easy to set up and use.
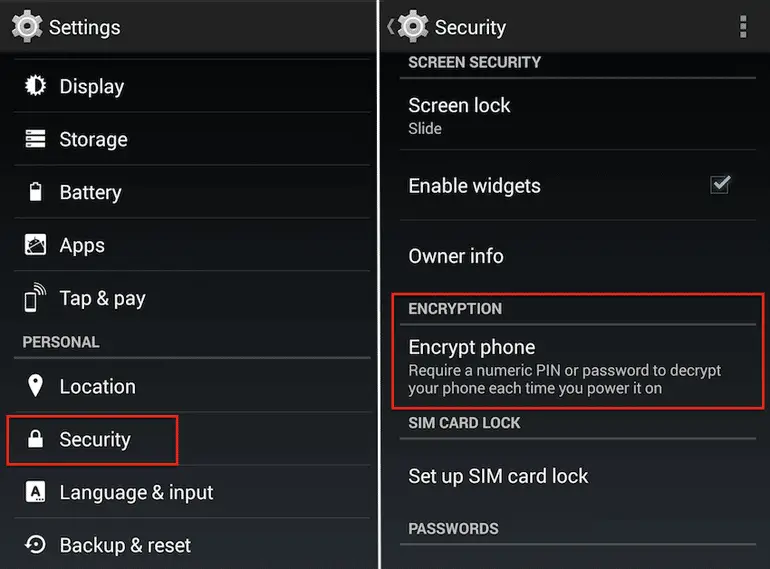
tablet, or just your SD card
You need to plug your phone into a power source because the encryption process can take an hour or more to complete (the device should be at least 80% charged). Make sure you don’t interrupt the encryption process at any point because this can lead to a loss of data.
4.5 Encrypt your iPhone or iPad
Apple devices are automatically encrypted, provided you use a passcode. The trick to making sure your device remains secure is to pick a strong six-digit passcode (rather than the default four digits) or – best of all – an alphanumeric key of any length.
To do this, go to Settings, Touch ID & Passcode and enter your existing PIN. Tap Change Passcode, enter your PIN again and then tap Passcode Options.
4.6 Lock your Samsung phone with Knox
If you have a Samsung device, such as a Galaxy S7 or S8, you can use Knox to remotely lock it or set it to automatically encrypt all of your data. This prevents access to both your internal and SD card storage. Entering your Knox password will decrypt the data. Knox
uses a very strong 256-bit AES cipher algorithm to encrypt data on the device.
WHICH IS THE STRONGEST ENCRYPTION
One of the most confusing aspects of encryption is the array of algorithms – each of different strengths and sizes – used by various tools and services. Here’s a brief guide to the most common encryption standards.
AES
Advanced Encryption Standard (AES) – also known as Rijndael –is the industry standardsymmetric encryption algorithm used by the US government to protect classified information. It’s considered impervious to all attacks. AES offers three different key lengths: its default of 128-bits, along with keys of 192 and 256 bits for heavy-duty encryption purposes.
Camellia
This Japanese-developed symmetric algorithm is used by popular encryption programs such as VeraCrypt and GNU Privacy Guard. Like AES, it creates keys of 128, 192 and 256 bits and has never been broken. Camellia is also used by TLS, the standard technology for creating an encrypted link between websites and your browser.
Twofish
Twofish is a symmetric encryption algorithm that creates key sizes of up to 256 bits. It’s renowned for being fast, flexible and efficient, and is often the encryption algorithm used by password-management tools and secure-payment systems.
RSA
RSA is an asymmetric encryption algorithm that creates keys with at least 128 bits. RSA keys of this length have been broken in a matter of seconds, so security experts now recommend that keys of 1,024 bits or more be used.
Triple DES
The original Data Encryption Standard (DES) algorithm was eventually recognised as being easy to crack. It was replaced by Triple DES, which uses three keys of 56 bits each (168 bits in total) – once considered the industry standard – but this, too, is now being phased out
Hope our Guide “A Complete Essential Guide to Encrypting Your Data” helps you to understand each and every aspects of Data Encryption.
I don’t think after reading this much information, you are not going to share with others. please Share this articles with your friends. if you have any query, feel free to comment.