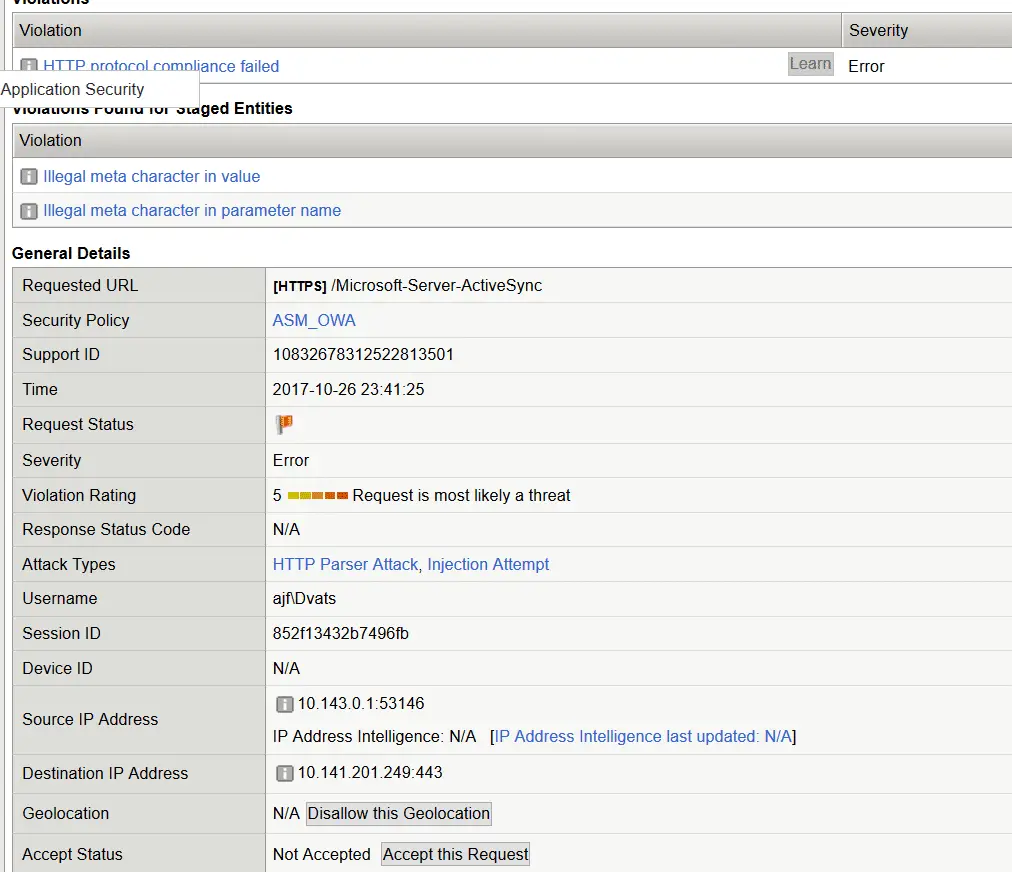
Recently I faced the issue with Microsoft ActiveSync where I created the transparent policy and applied on the Microsft OWA VIP but after applying Transparent ASM policy on OWA VIP, Outlook client stopped working. it’s just showing “trying to connect“.
Then after I opened a case with F5 support then after I get to know both RPC and ActiveSync connections which are currently not supported by the ASM unfortunately.
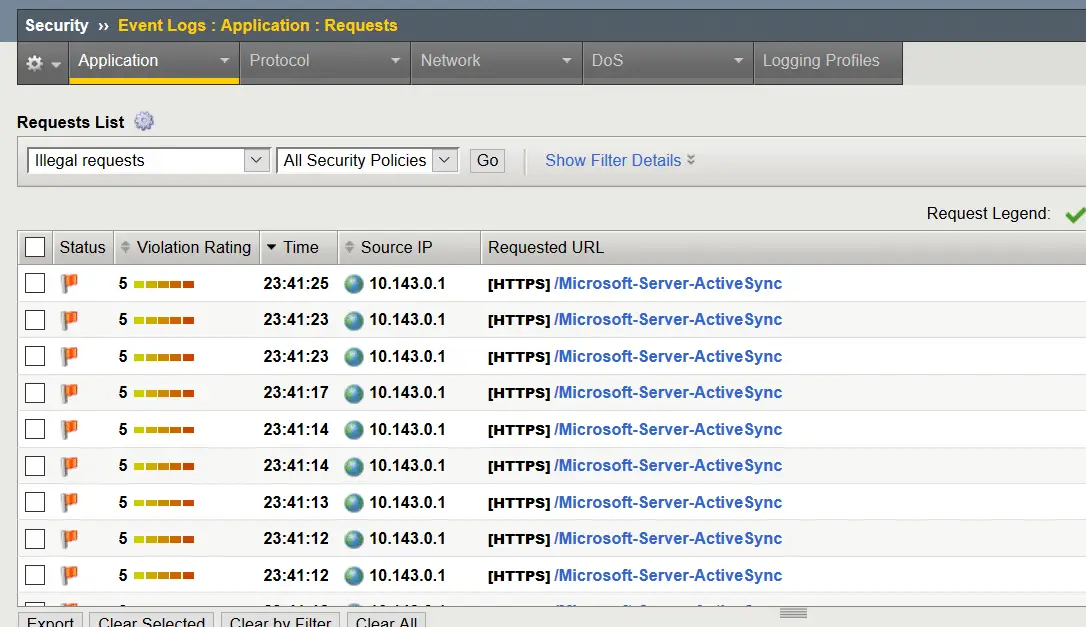
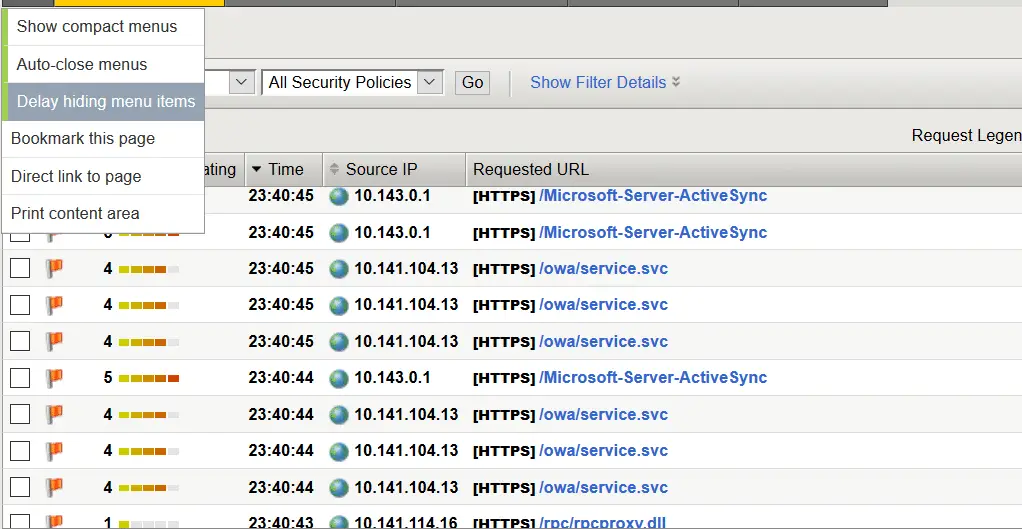
When i checked the Event logs for this policy it’s giving me below violations
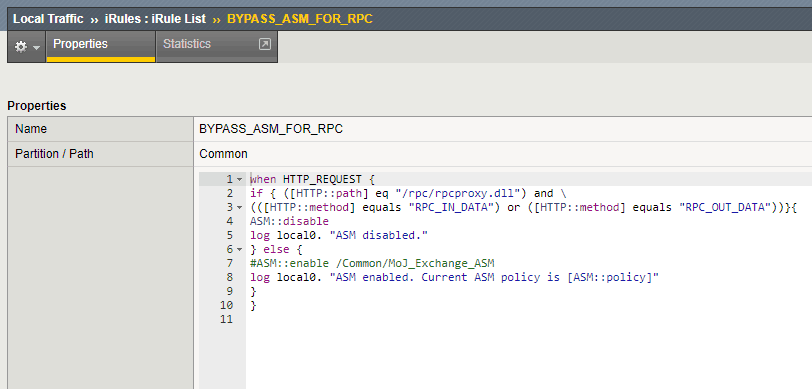
F5 is talking about this also in K40345000 but I didn’t follow the same iRule, Icreated own irul based on the my blocking URL’s here with the help of my Brother and Friend Rohit Singla
F5 Recommend iRule:-
when HTTP_REQUEST {
if { ([HTTP::path] eq “/rpc/rpcproxy.dll”) and \
(([HTTP::method] equals “RPC_IN_DATA”) or ([HTTP::method] equals “RPC_OUT_DATA”))}{
ASM::disable
log local0. “ASM disabled.”
} else {
ASM::enable /Common/MyASMpolicy
log local0. “ASM enabled. Current ASM policy is [ASM::policy]”
}
}
Used iRule by me :-
or
if { ([HTTP::path] eq “/rpc/rpcproxy.dll”) and \
(([HTTP::method] equals “RPC_IN_DATA”) or ([HTTP::method] equals “RPC_OUT_DATA”))}{
ASM::disable
log local0. “ASM disabled.”
} else {
#ASM::enable /Common/MoJ_Exchange_ASM
log local0. “ASM enabled. Current ASM policy is [ASM::policy]”
}
}
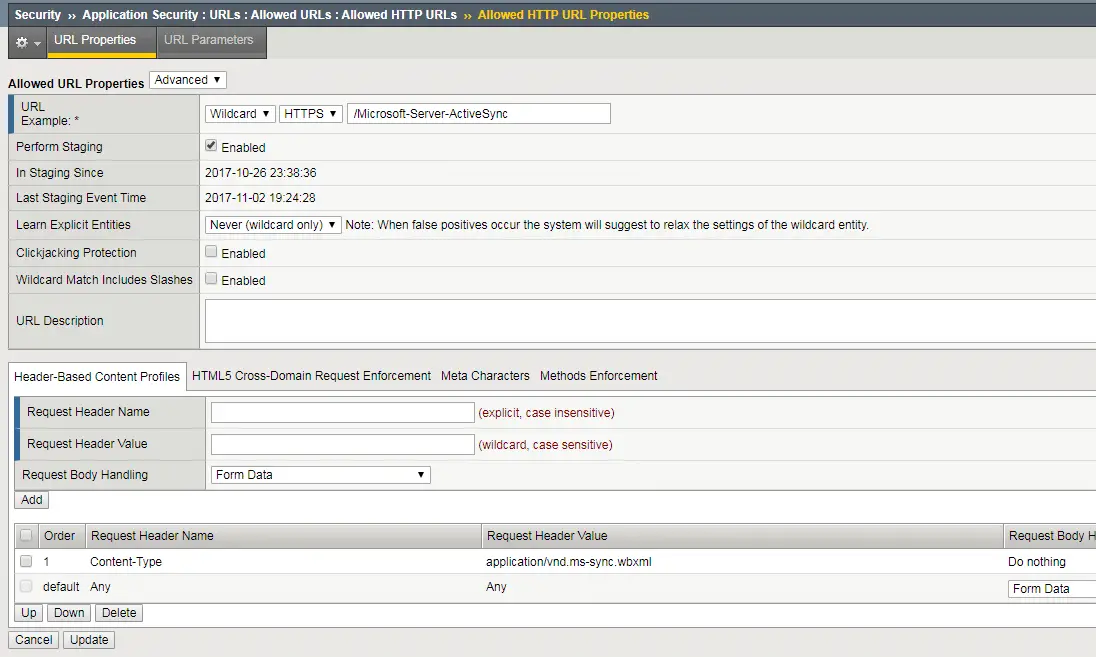
a) Go to : Security > Application Security > URLs > Allowed URLs > /Microsoft-Server-ActiveSync
b) In the Allowed URL Properties, click on the drop-down and select “Advanced”
c) Add a [Header-Based Content Profiles] with the following details :
Request Header Name = Content-Type
Request Header Value = application/vnd.ms-sync.wbxml
Request Body Handling = Do nothing
d) Click “Update” and also apply the changes to the policy