X11 is the X Window System which allows you to run software on a UNIX/Linux server in a Windows-like way such that you can use your mouse to click around in it.
The secure way to do this is to forward your X11 packets through your ssh connection which automatically sets your DISPLAY environment variable for you. Manually setting your DISPLAY environment variable opens your computer up to security risks.
Here is the process to enable x11 forwarding in Kali Linux:-
First open the Linux terminal, By default terminal shortcut key is mapped to Ctrl+Alt+T or either Open with GUI.
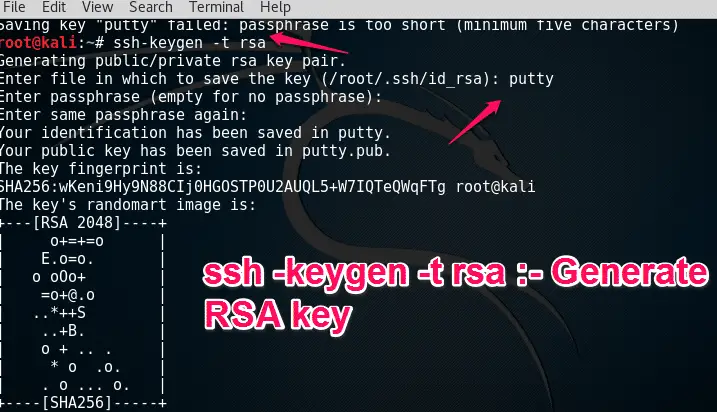
First, we need to generate RSA key using ” ssh -keygen -t rsa ”
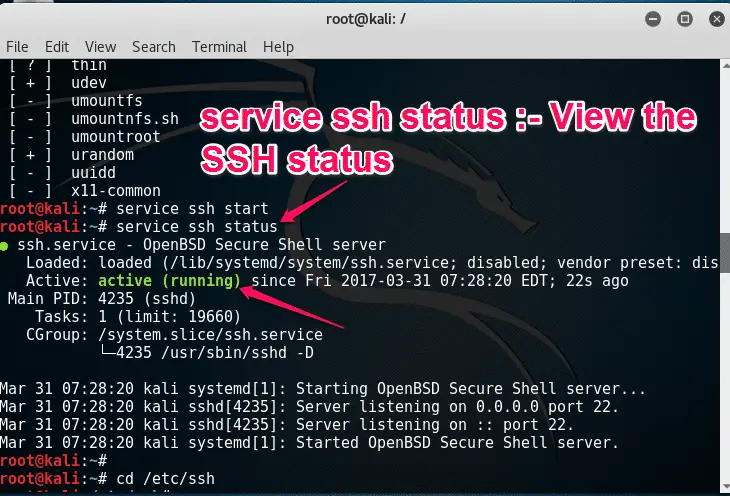
then check the “ service ssh status ” command to view the running status of SSH services, make sure it’s running.
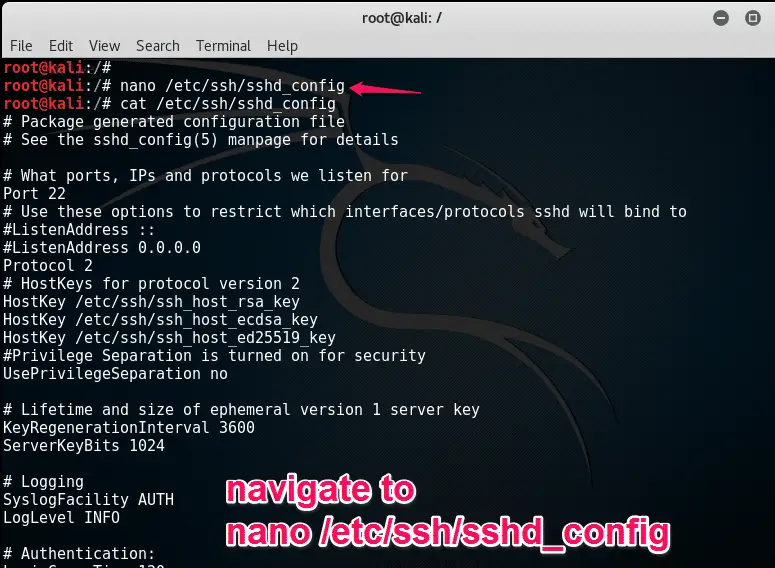
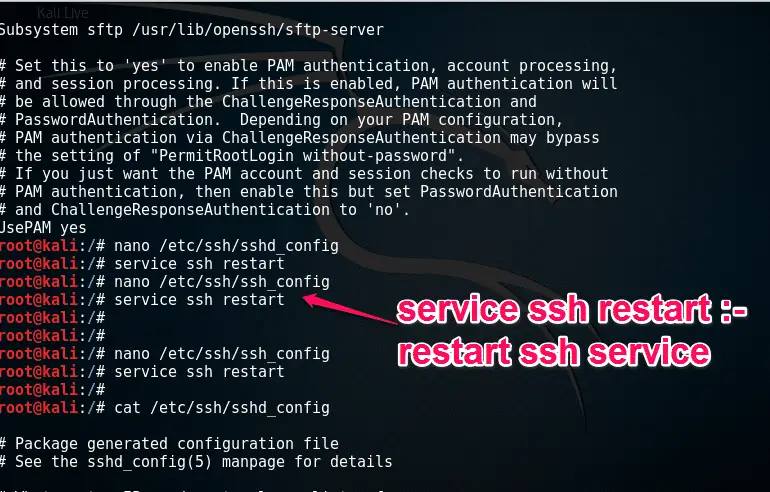
then navigate to “nano /etc/ssh/sshd_config”
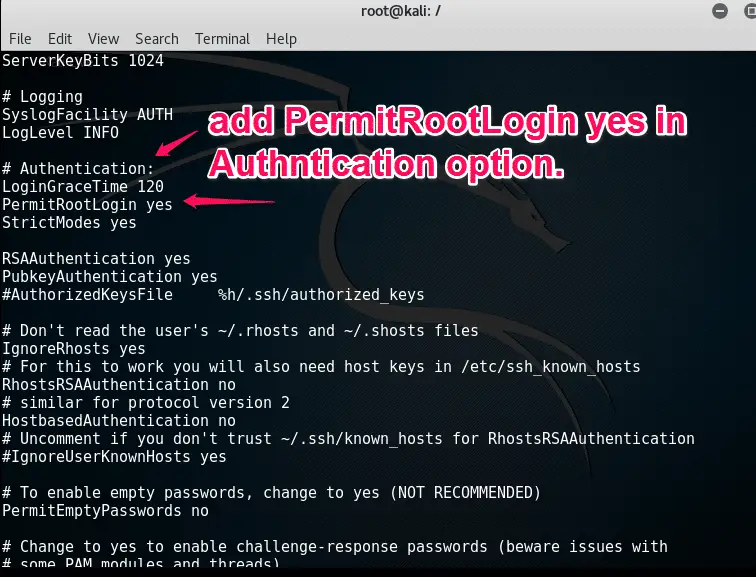
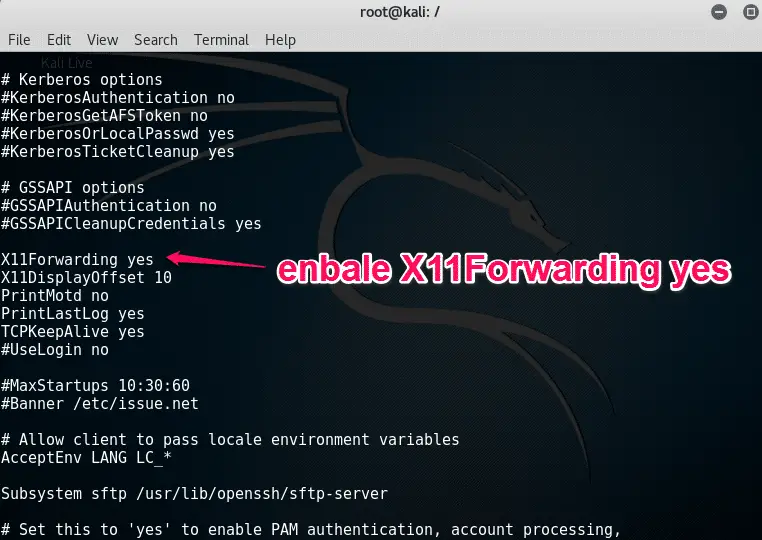
add “PermitRootLogin yes” in Authentication option.
enable X11Forwarding yes
Now you need to restart SSH services with “service ssh restart” command.
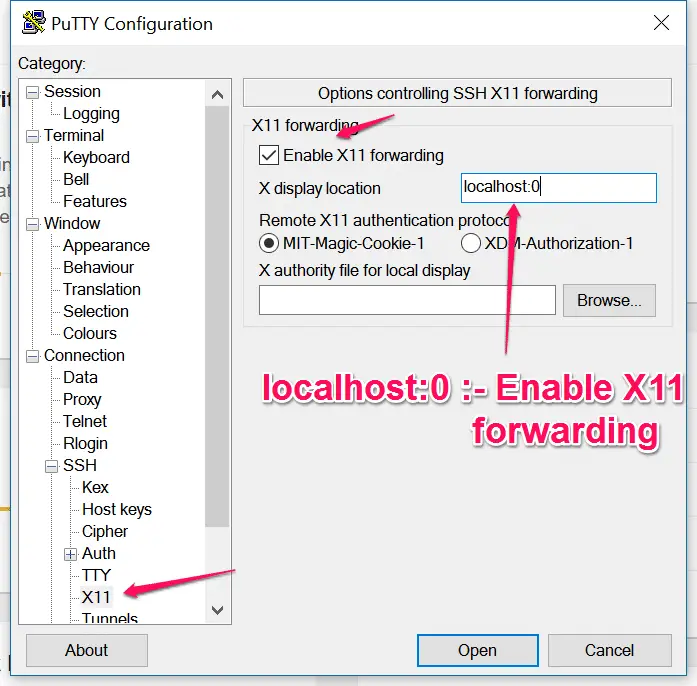
Now download Putty and navigate to X11, under Connection > SSH > Auth
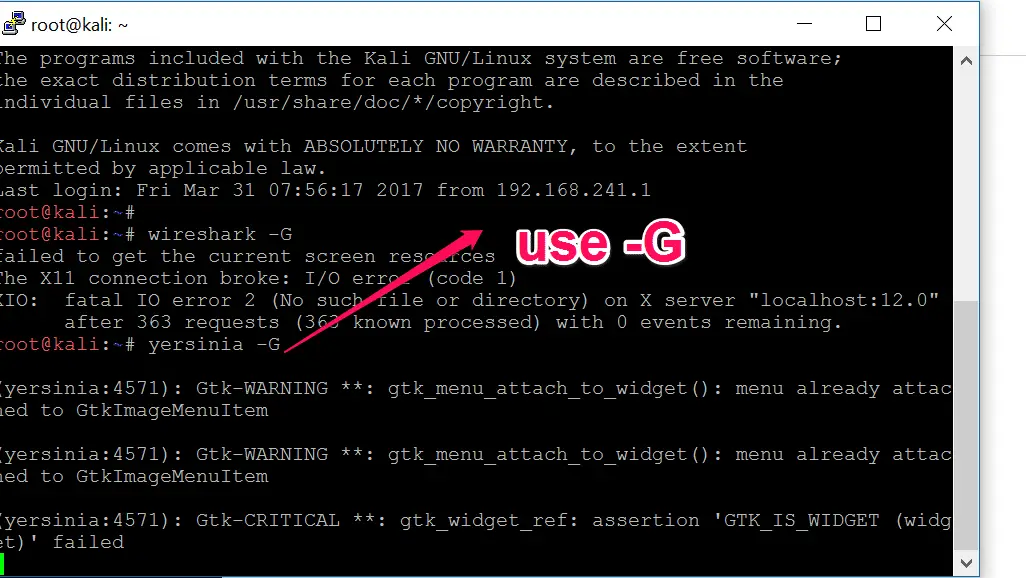
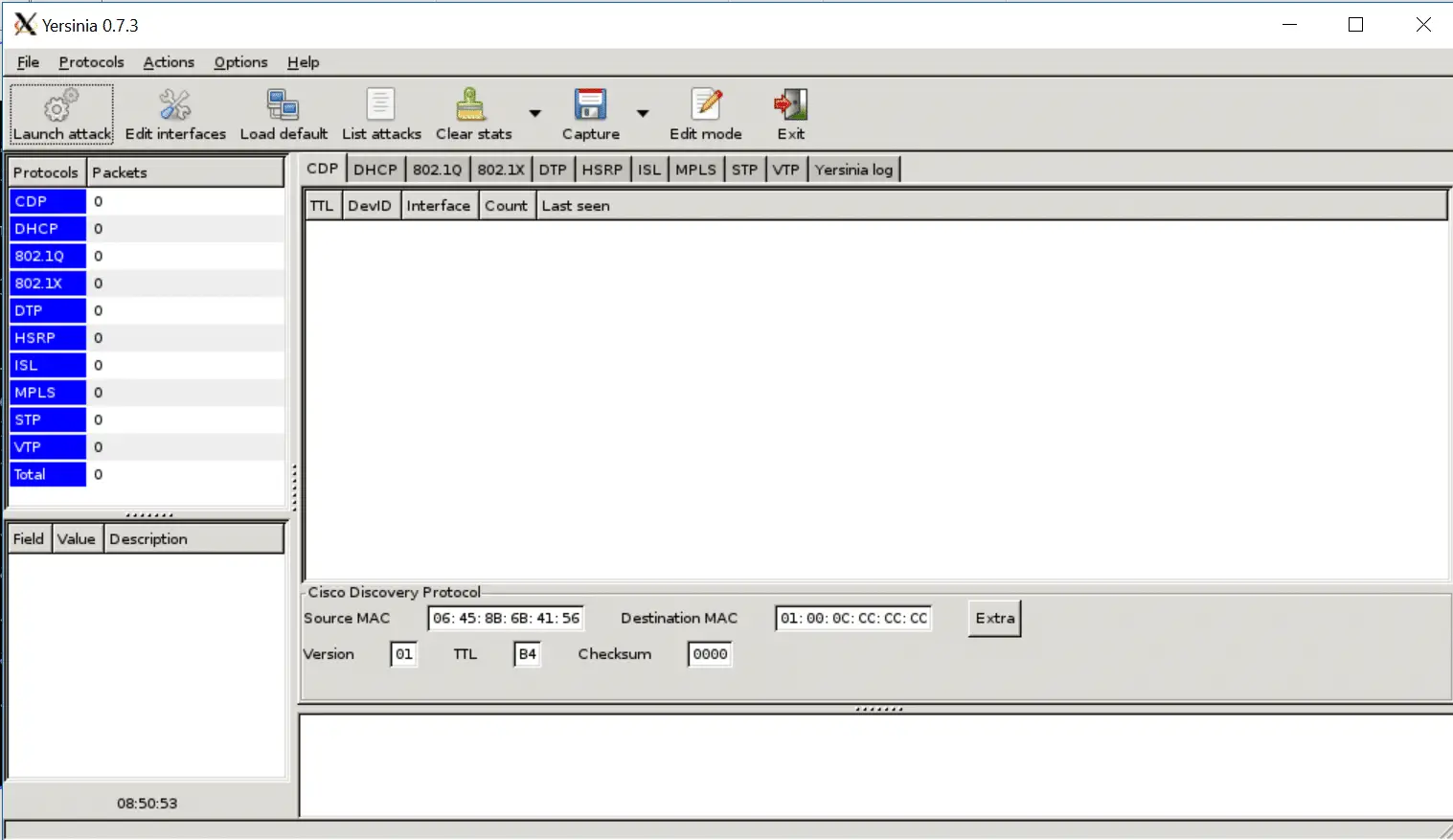
now you need to use -G option with your command, like in my case I want’s to open yersinia then in this I need to use “yersinia -G” without quotes.
Now it will open Yersinia GUI on X11 Forwarding. That’s it.
Note:- I have written a post for people looking for How to set up Kali Linux VirtualBox ?, do read it If you are interested.
How do I Enable X11 Forwarding in Linux?
X11 forwarding is a powerful feature in Linux that allows you to securely run graphical applications on a remote server and display them on your local machine.
This capability is particularly useful when accessing applications with a graphical user interface (GUI) on a remote server, enhancing your productivity and convenience.
To enable X11 forwarding in Linux, you need to follow a few simple steps.
Firstly, ensure that you have the OpenSSH server installed on the remote machine and an SSH client on your local machine.
OpenSSH is a widely-used suite of tools for secure remote login and file transfer using the SSH protocol.
Next, establish an SSH connection to the remote server by executing the command ssh -X user@hostname. The -X flag enables X11 forwarding. Replace “user” with your username and “hostname” with the IP address or hostname of the remote machine.
Once connected, you can test X11 forwarding by running a graphical application, such as xeyes or gedit. If the application opens on your local machine’s display, then X11 forwarding is successfully enabled.
To make X11 forwarding permanent, you can modify the SSH server configuration file (/etc/ssh/sshd_config) on the remote machine. Locate the line #X11Forwarding no and change it to X11Forwarding yes. Save the file and restart the SSH server for the changes to take effect.
By enabling X11 forwarding in Linux, you unlock a world of possibilities for remotely accessing and utilizing GUI applications on servers, providing a seamless and efficient workflow.
Setting up the X11 Display Variable in Linux
Configuring the X11 display variable in Linux is crucial when establishing a connection between a remote server and your local machine for running graphical applications.
This process allows you to harness the power of the X Window System, enabling the display of GUI applications seamlessly.
To begin, open your terminal and enter the command echo $DISPLAY. The output will show the current value of the X11 display variable. By default, it is usually set to :0.0.
To set up the X11 display variable, ensure that you have the necessary software installed, including X11 server and client libraries. These components are essential for the functioning of the X Window System.
Next, establish an SSH connection to the remote server using the -X flag, which enables X11 forwarding. For example, ssh -X user@hostname will initiate the connection. Replace “user” with your username and “hostname” with the IP address or hostname of the remote machine.
Once connected, the X11 display variable will be automatically set, and you can verify it by running echo $DISPLAY again. The output should reflect the display variable value assigned by the remote server.
By correctly setting up the X11 display variable in Linux, you gain the ability to run graphical applications on a remote server while enjoying the seamless display on your local machine, streamlining your workflow and expanding your possibilities.
The SSH Command for X11 Forwarding
What is the SSH command for X11 forwarding? If you seek to harness the graphical capabilities of remote servers, this question is of utmost importance.
X11 forwarding, a feature SSH (Secure Shell) offers, enables the seamless display of graphical applications from a remote server to your local machine.
To initiate X11 forwarding, you need to execute the SSH command with the appropriate flags.
The SSH command for X11 forwarding is ssh -X user@hostname, where “user” represents your username and “hostname” corresponds to the IP address or hostname of the remote machine.
By including the -X flag, you instruct SSH to enable X11 forwarding during the connection establishment.
This flag ensures that the X11 display protocol is forwarded from the remote server to your local machine, allowing you to launch and interact with GUI applications.
Once connected, you can test X11 forwarding by launching graphical applications such as xeyes or gedit directly from the command line. The applications’ windows will appear on your local machine, even though they are executed on the remote server.
The SSH command for X11 forwarding unlocks the potential for a seamless and efficient workflow, allowing you to utilize graphical applications on remote servers while enjoying a local display.
Whether you’re managing remote servers or accessing powerful tools, X11 forwarding empowers you to leverage the full graphical capabilities of your Linux environment.
Initiating X11 from the Command Line
How to start X11 from the command line? If you wish to immerse yourself in the graphical realm of your Linux environment, this guide will provide you with the necessary steps to embark on your journey.
To begin, open a terminal and enter the command startx. This command launches the X Window System, initiating the X server and allowing the display of graphical applications.
Behind the scenes, the startx command triggers a series of processes. It executes the X server, which manages the display and input devices, and the window manager, responsible for the appearance and behavior of the graphical interface.
When you run startx, the X server reads the configuration file located at ~/.xinitrc or ~/.xsession. These files define the initial applications and settings to load upon starting the X session.
You can customize your X session by editing these configuration files to launch specific applications or set environment variables.
By employing the startx command, you initiate the X11 environment from the command line, allowing you to experience the rich graphical capabilities of your Linux system.
Whether you seek to explore the vast array of GUI applications or unleash your creativity through graphic design, starting X11 from the command line serves as your gateway to a visually immersive experience.
Verifying X11 Forwarding Enablement in Linux
How do you check if X11 forwarding is enabled in Linux?
Ensuring that X11 forwarding is properly configured is vital for seamlessly running graphical applications on remote servers. Thankfully, Linux provides a straightforward method to validate this configuration.
To check if X11 forwarding is enabled, open a terminal on your local machine and establish an SSH connection to the remote server using the command ssh -X user@hostname.
Replace “user” with your username and “hostname” with the IP address or hostname of the remote machine.
Once connected, execute the command echo $DISPLAY. If X11 forwarding is enabled, the output will display the value of the X11 display variable.
It typically appears as localhost:10.0 or similar, indicating that the X11 display protocol is being forwarded from the remote server to your local machine.
Alternatively, you can run a graphical application on the remote server, such as xeyes or xclock. If the application’s window appears on your local machine, X11 forwarding is indeed enabled and functioning correctly.
By checking if X11 forwarding is enabled in Linux, you can ensure a seamless experience when working with graphical applications on remote servers.
This validation process allows you to harness the power of remote resources while effortlessly visualizing and interacting with their graphical interfaces.
Configuring SSH Port Forwarding in Linux
How to set up SSH port forwarding in Linux?
Mastering the art of port forwarding allows you to establish secure connections and channel network traffic through SSH, providing a powerful mechanism for accessing remote services.
To initiate SSH port forwarding, you need to employ the -L flag in the SSH command. This flag, followed by the source port, destination host, and destination port, establishes a tunnel between your local machine and the remote server.
For example, the command ssh -L local_port:destination_host:destination_port user@hostname creates a local port forwarding tunnel. Replace “local_port” with the desired port on your local machine, “destination_host” with the IP address or hostname of the target machine, and “destination_port” with the port number on the remote server.
Once the SSH connection is established, any network traffic directed to the local port will be securely forwarded to the remote server’s specified destination.
This process enables you to access services hosted on the remote machine as if running locally.
SSH port forwarding is an invaluable technique for securely accessing remote services and circumventing network restrictions.
Whether you wish to connect to a database server or access a web application on a remote host, mastering SSH port forwarding in Linux empowers you with unparalleled network flexibility and control.
Locating the Installation Directory of X11 on Linux: Unveiling the Path
Where is X11 installed on Linux? The X Window System, commonly referred to as X11, is a fundamental component of graphical environments in Linux. Understanding the installation location of X11 is crucial for various system administration tasks and customizations.
On Linux systems, X11 is typically installed in the /usr directory. More specifically, the X11 server binaries, libraries, and related files can be found in the /usr/bin and /usr/lib directories, respectively.
The main executable of the X server, known as Xorg, is often located in /usr/bin/Xorg. This binary is responsible for managing the display and handling user input.
Additionally, configuration files specific to X11 are often stored in the /etc/X11 directory. This directory contains essential files such as xorg.conf, which allows customization of X11 server settings.
In some cases, you might also find X11-related files in the /opt directory if you have installed X11 from third-party sources or specific distributions.
By familiarizing yourself with the installation directory of X11 on Linux, you gain insight into the underlying components and resources that drive the graphical capabilities of your system.
This knowledge proves invaluable for troubleshooting, customization, and exploring the vast potential of X11 in your Linux environment.