If you are looking for a Network Engineer, Network Administrator or any other IT administrator job. OSI model is one the most common topic for the interviewer to ask you. Today I am going to cover-up most of the interview questions related to OSI model.
(Q) What is OSI Model?
Ans:- Check my article The OSI Model’s Seven Layers Defined and Functions Explained
(Q) What is TCP?
TCP (Transmission Control Protocol) is a set of rules (protocol) used along with the Internet Protocol (IP) to send data in the form of message units between computers over the Internet. While IP takes care of handling the actual delivery of the data, TCP takes care of keeping track of the individual units of data (called packets) that a message is divided into for efficient routing through the Internet.
TCP provides end-to-end reliability between the application process running on one computer system to another computer system by adding services on top of IP.
Basic Features of TCP:-
Some of the basic features of TCP are:-
- Data Transfer
- Reliability
- Connections
- Flow Control
- Precedence and security
- Multiplexing
How it Works:-
There are four distinct elements that uniquely identify a TCP connection. They are:-
- IP address of the Sender
- IP address of the receiver
- TCP port of the sender
- TCP port of the receiver
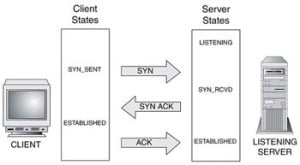
To establish a TCP session, the two computers participating in the session must first go through what is known as the ” three-way handshake“. There are two scenarios where a three-way handshake would take place, namely:-
- Establishing a connection ( an active open )
- Terminating a connection ( an active close)
The steps in the connection establishment are as follows:-
- Client:- sends a message with the SYN flag on
- Server:- Replies to the client with a message that has SYN and ACK flag on.
- Client:- replies on the server’s SYN/ACK message with an ACK message.
TCP Header:-
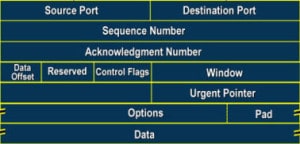
The standard TCP Header is defined in RFC 791 and the TCP packet structure is illustrated as below picture:-
The TCP header is 20 bytes long, or up to 24 bytes with options. You need to understand each field in the TCP segment is:-
Source Port:- The port number of the application on the host sending the data.
Destination port:- The port number of the application requested on the destination host.
Sequence Number:- A number used by TCP that puts the data back in the correct order or re-transmits missing or damaged data, a process called sequencing.
Acknowledgment Number:- The TCP octet that is expected next.
Header length:- The number of 32-bit words in the TCP header. This indicates where the data begins. The TCP header (Even one including options ) is an integral number of 32-bits in length.
Reserved:- Always set to Zero
Code bits:- Control functions used to set up and terminate a session.
Window:- The window size the sender is willing to accept, in octets.
Checksum:-The cyclic redundancy check (CRC), because TCP doesn’t trust the lower layers and checks everything. The CRC checks the header and data fields.
Urgent:- A valid field only if the urgent pointer in the code bits is set. If so, this value indicates the offset from the current sequence number, in octets, where the first segment of non-urgent data begins.
Options:- May be 0 or a multiple of 32-bits if any.
Data:- Handed down to the TCP protocol at the Transport layer, which includes the Upper layer headers.
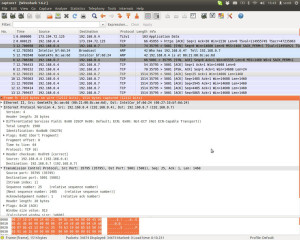
You can easily view all the TCP header information with Wireshark.
Error Recovery:-
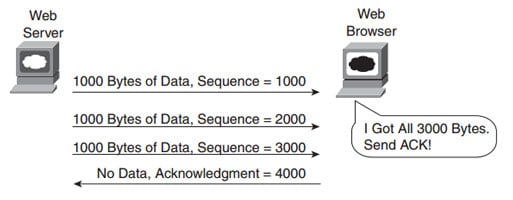
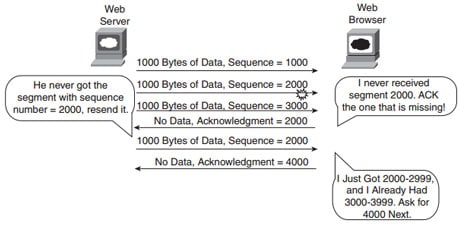
Also known as reliability, TCP provides error recovery during data transfer sessions between two end devices who have established a connection. The sequence and acknowledgment fields in the TCP header are used to track every byte of data transfer and ensure that missing bytes are retransmitted.
In below image, the Acknowledgment field sent by the web client (4000) implies the next byte to be received; this is called forward acknowledgment.
TCP Acknowledgment Without Errors:-
TCP Acknowledgment With Errors:-
Flow Control:-
Flow control is handled by TCP through a process called windowing. The two end devices negotiate the window size when initially establishing the connection; then they dynamically renegotiate window size during the life of the connection, increasing its size until it reaches the maximum window size of 65,535 bytes or until errors occur. The window size is specified in the window field of
the TCP header. After sending the amount of data specified in the window size, the source must receive an acknowledgment before sending the next window size of data.
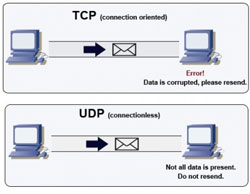
What are differences between TCP and UDP?
What is User Datagram Protocol ( UDP):-
User Datagram Protocol is a protocol that is used at the Transport layer for connectionless, non-guaranteed communications. Unlike TCP, UDP does not setup a connection and does not use acknowledgments. UDP is given the Internet Protocol number of 17 and is defined in RFC 768 .
UDP uses 16-bit port numbers similar TCP. When a UDP packet is sent to a port that is not listening, it will respond with an ICMP port unreachable message to the packet sender.
Common network applications that use UDP include Domain Name System (DNS), Streaming Media Applications, Voice over IP, Trival File Transfer Protocol ( TFTP) and online Games.
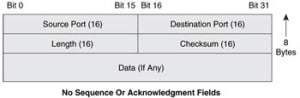
UDP Header Format:-
The UDP header consists of four 16-bit fields ( 4 * 16), which makes a total of 8-bytes in total length. The UDP header comes immediately after the IP header. Th details of individual fields are as follows:-
Source Port:- A 16-bit field whose values can range from 0 to 65,535 specifying the source port.
Destination Port:- A 16-bit field whose values can range from 0 to 65,535 specifying the destination port.
Length:- A 16-bit field whose values can range from 0 to 65,535. it is the length of the UDP header and the UDP data in bytes. The minimum value for this field is 8 bytes.
UDP Checksum:- A 16-bit field whose values can range from 0 to 65,535. The UDP checksum covers the UDP header and the UDP data. With UDP the checksum is optional, while the TCP it is mandatory.
Differences between TCP and UDP:-
| TCP | UDP |
| Sequenced | Unsequenced |
| Reliable | Unreliable |
| Connection-oriented | Connectionless |
| Virtual Circuit | Low Overhead |
| Acknowledgments | No Acknowledgments |
| Windowing flow control | No Windowing of flow control |
Brief Explanation of Differences between TCP and UDP:-
| Attributes | TCP | UDP |
| Acronym for | Transmission Control Protocol | User Datagram Protocol or Universal Datagram Protocol |
| Function | As a message makes its way across the internet from one computer to another. This is connection based. | UDP is also a protocol used in message transport or transfer. This is not connection based which means that one program can send a load of packets to another and that would be the end of the relationship. |
| Usage | TCP is used in case of non-time critical applications. | UDP is used for games or applications that require fast transmission of data. UDP’s stateless nature is also useful for servers that answer small queries from huge numbers of clients. |
| Examples | HTTP, HTTPs, FTP, SMTP Telnet etc… | DNS, DHCP, TFTP, SNMP, RIP, VOIP etc… |
| Ordering of data packets | TCP rearranges data packets in the order specified. | UDP has no inherent order as all packets are independent of each other. If ordering is required, it has to be managed by the application layer. |
| Speed of transfer | The speed for TCP is slower than UDP. | UDP is faster because there is no error-checking for packets. |
| Reliability | There is an absolute guarantee that the data transferred remains intact and arrives in the same order in which it was sent. | There is no guarantee that the messages or packets sent would reach at all. |
| Header Size | TCP header size is 20 bytes | UDP Header size is 8 bytes. |
| Common Header Fields | Source port, Destination port, Check Sum | Source port, Destination port, Check Sum |
| Streaming of data | Data is read as a byte stream, no distinguishing indications are transmitted to signal message (segment) boundaries. | Packets are sent individually and are checked for integrity only if they arrive. Packets have definite boundaries which are honored upon receipt, meaning a read operation at the receiver socket will yield an entire message as it was originally sent. |
| Weight | TCP requires three packets to set up a socket connection before any user data can be sent. TCP handles reliability and congestion control. | UDP is lightweight. There is no ordering of messages, no tracking connections, etc. It is a small transport layer designed on top of IP. |
| Data Flow Control | TCP does Flow Control. TCP requires three packets to set up a socket connection before any user data can be sent. TCP handles reliability and congestion control. | UDP does not have an option for flow control |
| Error Checking | TCP does error checking | UDP does error checking, but no recovery options. |
| Fields | 1. Sequence Number, 2. AcK number, 3. Data offset, 4. Reserved, 5. Control bit, 6. Window, 7. Urgent Pointer 8. Options, 9. Padding, 10. Check Sum, 11. Source port, 12. Destination port | 1. Length, 2. Source port, 3. Destination port, 4. Check Sum |
| Acknowledgement | segments | No Acknowledgment |
Source for brief Explanation:- https://www.diffen.com/difference/TCP_vs_UDP
Popular Protocols that are supporting both TCP and UDP:-
DNS:- DNS uses TCP for Zone exchanges between server and UDP when a client is trying to resolve a hostname to an IP-address.
LDAP:- LDAP always uses TCP – this is true and why not UDP because a secure connection is established between client and server to send the data and this can be done only using TCP, not UDP. UDP is only used when finding a domain controller (Kerberos) for authentication. For example, a domain client finding a domain controller using DNS.
List of TCP and UDP port numbers
(Q) Which layer is responsible for converting data packets from the Data Link layer into electrical signals?
Ans:- Physical Layer
Explanation:- The Physical layer takes frames from the Data Link Layer and encodes the 1s and 0s into a digital signal for transmission on the network medium.
(Q) At which layer is routing implemented, enabling connections and path selection between two end systems. ?
Ans:- Network Layer
Explanation:- The Network layer provides routing through an inter-network and logical addressing.
(Q) Which layer defines how data is formatted, presented, encoded, and converted for use on the network?
Ans:- Presentation Layer
Explanation:- The Presentation layer makes sure that data is in a readable format for the application layer.
(Q) Which layer is responsible for creating, managing and terminating sessions between applications?
Ans:- Session
Explanation:- The Session layer setup, maintains and terminates session between applications.
(Q) Which layer provides logical addressing that routers will use for path determination?
Ans:- Network Layer
Explanation:- The Network layer provides logical addressing, typically IP addressing and routing.
(Q) Which layer specifies voltage, wire speed, and pinout cables and moves bits between devices?
Ans:- Physical Layer
Explanation:- The Physical layer is responsible for the electrical and mechanical connections between devices.
(Q) Which layer combines bits into bytes and bytes into frames, uses MAC addressing, and provide error detection?
Ans:- Data Link Layer
Explanation:- The Data-link layer is responsible for the framing of data packets.
(Q) Which layer is responsible for keeping the data from different applications separate on the network?
Ans:- Session layer
Explanation:- The Session layer creates sessions between different host applications.
(Q) Which layer segments and resembles data into a data stream?
Ans:- Transport
(Q) Which layer provides the physical transmission of the data and handless error notification, network topology, and flow control?
Ans:- Data Link Layer
(Q) Which Layer manages device addressing, tracks the location of devices on the network, and determine the best way to move data?
Ans:- Network layer
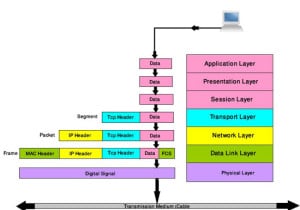
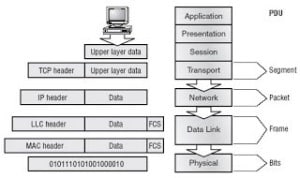
(Q) How Data breaks down on each layer from top to bottom?
(Q) What is Data Encapsulation ? or Order of Encapsulation ? or Which layer is represented by frames? Which layer is represented by segments? Which layer is represented by Packets? Which Layer is represented by bits?
Ans:- Data encapsulation is the process that takes place when one host on a network needs to send data to another host. As data is prepared for transit, it flows down through each layer of the OSI model. At each layer, extra control information is added to the data before being passed to the layer below. This process continues until the data reaches the physical layer where the data is passed onto the network medium as a series of 0’s and 1’s.
(Q) DNS uses which protocol? Why?
DNS is using both TCP and UDP protocol. TCP for Zone exchanges between server and UDP when a client is trying to resolve a hostname to an IP-address.
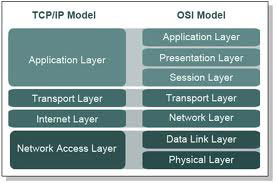
(Q) What are the differences between OSI and TCP/IP model?
- OSI is a reference model and TCP/IP is an implementation of OSI model.
- OSI has 7 layers whereas TCP/IP has only 4 layers The upper 3 layers of the OSI model is combined with the TCP/IP model.
- OSI has physical layer, data link layer, network layer, transport layer, session layer, presentation layer and application layer TCP/IP has: Network layer, Internet layer, transport layer, and application layer.
(Q) MAC address works on which layer? What are the differences of MAC sublayer and LLC sublayer?
Ans:- MAC address works on the data-link layer.
MAC sublayer(802.3):- defines how to transmit data on physical layer
LLC sublayer(802.2):- responsible for identifying different protocol logically & encapsulate them.
You must have knowledge of each layer to give the most of the answers.
I am writing this article after collection interview questions from my friends or my own interview experience. If you have any question regarding OSI model. please pass the comment. so I will add it.
I will recommend you to go through “Top 50 Networking Interview Questions and Answers” before taking your interview.
Also, Check Most Common F5 101 exam question and Answers
We are recommending Networking Self-Teaching Guide and OSI Reference Model for Telecommunications to our readers for depth study.
Video Tutorial:-