Are you looking for the best Kali Linux tools? If yes, you have stumbled upon the right webpage. This article will cover a list of the best Kali Linux tools.
So, without any further ado, let’s get started –
Kali Linux Tools – What do we know?💁
Kali Linux is one of the most popular and widely used operating systems for penetration testing and hacking.
Even though it got popular amongst the general audience when they saw Kali Linux was practically used in the Mr. Robot series, it is not designed for general purposes.
Kali Linux is designed for people in the cybersecurity, analysis, and hacking industry, such as network analysts, penetration testers, hackers, and more.
Kali Linux is originally a Debian-derived Linux distro developed by Mati Aharoni and Devon Kearns, and currently, all the development of this tool is being managed by Offensive Security.
However, due to its open-source nature, you can find many tweaked versions of Kali on the internet. You can even modify Kali to make it completely yours.
Kali Linux is a popular operating system among hackers and security professionals because it has more than 600 pre-built penetration testing tools that can make the penetration testing process much faster. These tools let you automate the process, save time, and capture accurate essential data.
These tools can be categorized in a wide range of categories, such as information gathering, wireless attacks, vulnerability analysis, web app penetration, exploitation tools, sniffing & spoofing tools, password attacks, and more.
You can find a detailed list of these tools on Kali Linux’s official website.
One best thing about Kali Linux is that it gets a very clean installation with basic tools and a terminal when you install it on your computer.
Even though there are over 600 tools, you won’t find them when you install Kali Linux. It happens so that your computer won’t get heavy with tools you won’t ever use.
Once you have installed Kali, you can use Kali Linux Metapackages to install a set of tools that you want to use. For example, if you are into wireless security and want tools to assess wireless security, you can install Kali and then use the kali-Linux-wireless meta package only.
That said, if you are a beginner, you won’t need all of the Kali Linux tools installed on your system. This is the purpose of writing this article.
This article has covered some of the best penetration testing tools in kali Linux you can use, regardless of what metapackages they belong to.
So, here we go –
Best Kali Linux Tools – Our Top Pick👌👌
1. Nmap
Nmap, aka Network Mapper, is one of the most popular Kali Linux tools you can use.
It is quite popular because it lets you discover hosts and services on any computer network. Nmap does this by sending packets and then analyzing the responses it receives.
Nmap offers dozens of amazing features, including host discovery, port scanning, TCP/IP stack fingerprinting, and version detection. It even lets you write scripts to add more features, such as service detection, vulnerability detection, and more.
With such functionalities, Nmap can be used in various areas such as security auditing, identifying open ports, network mapping, network inventory, network asset management, finding and exploiting vulnerabilities, and more.
It is a highly configurable tool, and you can make it completely yours with customized scripts.
Another good thing about Nmap is that it is not only available for Kali Linux. It is a Linux utility tool installed on most Linux distros. On top of that, you can also find the ported versions of Nmap for Windows, macOS, and BSD.
2. Lynis
Next, we have Lynis on our list. Like Nmap, Lynis is not limited to Kali Linux only and is available for macOS and Unix-based operating systems.
It can also be used on various systems, such as Raspberry Pi, QNAP storage devices, IoT devices, etc. Sadly, it is not available for Windows, but let’s not talk about that since here we are talking only about the best Kali Linux tools.
Lynis is an open-source tool that came into existence in 2007 and can serve different purposes such as security auditing, penetration testing, system hardening, vulnerability detection, and compliance testing such as PCI, HIPAA, and more.
It can be used by various professionals such as developers, testers, system administrators, security auditors, and more.
The scanning done using Lynis is modular and opportunistic. It thoroughly scans the components and tests them for vulnerabilities. There are over 300 security tests that you can perform using Lynis. The best thing is that these tests can be done with no dependencies, and the more system components it finds, the more thorough the auditing will be.
For example, let’s say you are using Nginx and want to scan and test it using Lynis. In the initial stage, Lynis will perform a thorough scan designed for Nginx, but it may discover SSL/TLS or other configurations.
It will add additional steps to test that newly discovered configuration.
However, these scans can be tailored, and you can disable some specific tests. You can script some tests on your own to run self-created tests.
Besides that, you can use plugins to add additional test types that can help you collect additional and customized system information.
3. Fierce
Fierce is a great, semi-lightweight tool for network mapping and port scanning. It is often used for locating non-contagious IP addresses and hostnames on a network.
The best thing about Fierce is that it is far simpler to use than IP scanners and DDoS tools, making it a perfect Kali Linux tool for beginners.
Fierce is mainly designed to help corporate networks by allowing them to discover possible targets on their network system to fix the issue before it causes any significant loss.
This Kali Linux tool can scan domains within a couple of minutes, making it a perfect tool to scan for vulnerabilities in a large computer network.
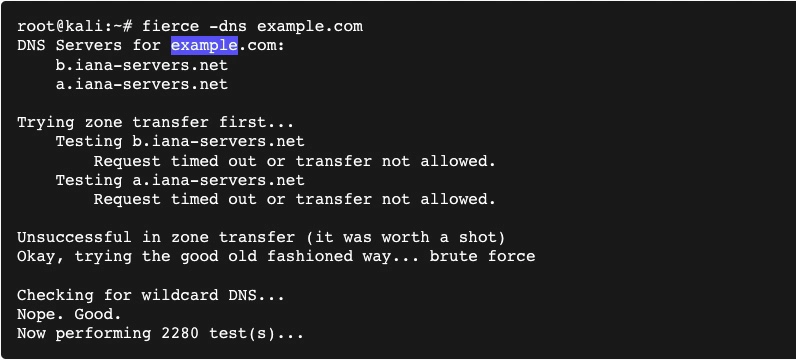
Fierce’s best features include its ability to perform reverse lookups for a specified range, internal and external IP range scanning, examining DNS records, performing an entire Class C scan, nameserver discovery, and more.
These are reasons Fierce is a highly regarded tool amongst the Whitehat community.
Despite being such a powerful and effective tool, it is simple. Once you have defined the target network, it will run several tests on the selected domains and retrieve all the valuable information.
You can later use this information to analyze vulnerabilities and exploitations.
4. OpenVAS
OpenVAS, aka Open Vulnerability Assessment Scanner, is a fully featured vulnerability scanner developed by a team responsible for one of the most famous vulnerability scanning tools, Nessus.
However, unlike Nessus, OpenVAS is licensed under the GPL license, meaning it is free to use.
The best thing about OpenVAS is that it can be authenticated and unauthenticated with various internet and industry protocols.
Currently, the OpenVAS engine comes with over 50K network vulnerability tests which can be used to perform any vulnerability and bug scans, even on a large scale.
In addition, it allows you to write your vulnerability test and integrate it into OpenVAS. This Kali Linux tool can be very helpful for testing and exploring local and remote network vulnerabilities, as it allows you to scan ports and map networks.
In addition, it supports the OpenVAS transfer protocol and fully integrates with SQL databases.
You can easily export all your test results in various file formats, including HTML, LateX, XML, and more. The tool is available for both Linux and Windows platforms.
5. Aircrack-ng
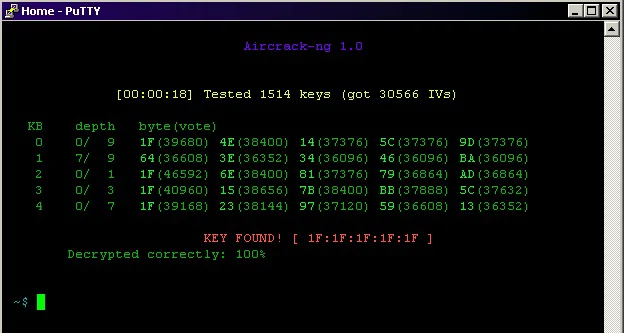
Aircrack-ng is one of the most popular tools suites that allow you to assess the Wi-Fi network for its security and vulnerabilities. This suite consists of four major tools: a packet sniffer, WEP, and WPA PSK cracker, an analyzing tool, and a hash-capturing tool.
Unlike other tools that we have mentioned in this list so far, Aircrack-ng is not only used to scan wireless networks and assess vulnerabilities but can also be used to attack the Wi-Fi network.
It allows you to perform various attacks such as dictionary attacks, replay attacks, de-authentication, fake access points, and more attacks that use packet injections.
Besides that, Aircrack-ng can also help you capture packages and decipher decryption keys. If you can decipher decryption keys, you can decrypt wireless traffic, giving you access to many things. Aircrack-ng is a CLI tool, allowing heavy scripting to use per your needs.
It is primarily a Kali Linux tool but also works on Windows, macOS, FreeBSD, NetBSD, OpenBSD, Solaris, and other platforms.
This tool supports all modern wireless attacks. Therefore, if you are into network or wireless security, I highly recommend making Aircrack-ng a part of your Kali Linux tools stack.
6. Nikto
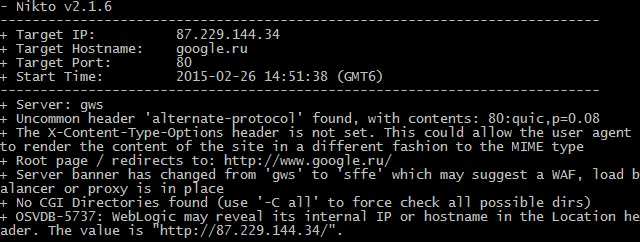
Nikto, aka Nikto2, is an open-source web server scanner that lets you perform vulnerability tests on web servers to scan for various types of items, such as dangerous files, programs, outdated versions of software, and more.
This Kali Linux tool can also help you scan for server configuration errors and other vulnerabilities.
The best thing about Nikto is that it is a free and open-source Kali Linux tool, allowing you to modify it further.
In addition, it is also one of the frequently updated tools with testing capabilities for the latest discovered vulnerabilities.
This makes it a perfect choice for scanning web servers so that you can protect them against attacks.
Currently, Nikto has a database of over 6700+ known web server-related vulnerabilities and lets you scan your web servers against them.
Besides that, Nikto supports version checks for over 1250 web servers and can be used on almost any web server, such as Apache, Nginx, LightSpeed, Lighttpd, and more.
It further supports host-based authentication, proxies, SSL encryption, and more. Once your scan is completed, you can export the test results in various file formats, including CSV, TXT, HTML, XML, and others.
It is written in Perl and can be used as a complementary tool to OpenVAS and other vulnerability scanners.
7. Wireshark
Next, we have Wireshark on our list. It is an open-source network protocol analyzing tool that supports Linux, Windows, OS X, and BSD platforms.
It is a great tool that lets you easily understand what’s happening inside your network at the microscopic level. This is one of the reasons it is widely popular amongst government agencies, educational institutions, and commercial and non-profit enterprises.
It is an open-source tool, meaning it is completely free. Gerald Combs originally introduced this project in 1998, and till now, thousands of people have contributed to this project.
So far, the team has introduced hundreds of deep inspections of protocols that can be done in no time, and more and more protocols are being added.
The best thing about Wireshark is that it offers a graphical user interface that makes it easy to apply filters and organize and manage captured data.
The GUI makes it less intimidating for beginners and allows them to analyze captured data. There is also a text-based version of Wireshark named tshark that offers similar functionalities but with a text-based UI.
Wireshark decryption supports protocols such as IPsec, Kerberos, ISAKMP, SSL/TLS, WPA/WPA2, WEP, and SNMPv3. The GUI also supports coloring rules, making the analysis process much faster.
On top of that, all the scan results can be exported in various file formats such as XML, CSV, plain text, PostScript, and more.
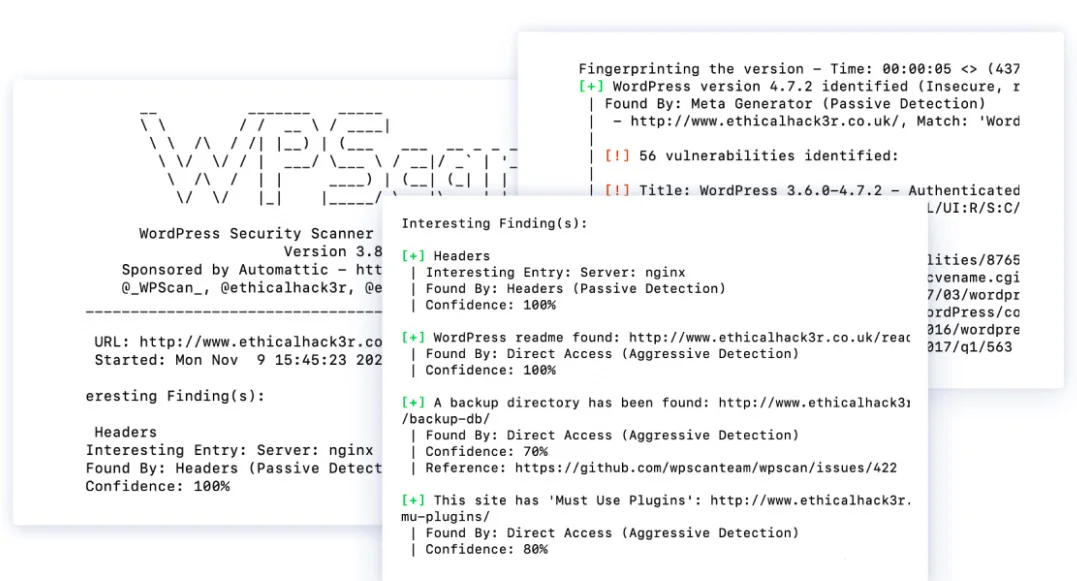
8. WPScan
WordPress is one of the most popular and widely used CMS platforms. This CMS platform is open-source and is trusted by millions of developers across the globe. WordPress is so reliable as a CMS that even the White House uses it to host its official website.
Such massive popularity also attracts attackers and hackers. Therefore, conducting frequent audits of WordPress websites is essential, and WPScan can help you with that.
It is a free, non-commercialized WordPress security scanner tool that allows security professionals and website developers to scan their sites for security vulnerabilities.
WPScan is a CLI tool that uses a database of over 28,992 WordPress vulnerability tests and scans your websites against them.
It also helps you identify weak passwords associated with registered users. It simply runs brute force to see which account can be compromised using a dictionary attack.
With the help of this Kali Linux tool, you can scan your WordPress website’s theme and plugin files, databases, and more. On top of that, it receives frequent updates directly from WPvulndb.com, which updates this tool with all known WordPress vulnerabilities.
9. Skipfish
Next, we have Skipfish on our list. Skipfish is similar to WPScan as it helps you scan web applications for vulnerabilities, but unlike WPScan, Skipfish isn’t only focused on WordPress. Instead, it can help you scan almost all web-based applications easily for vulnerabilities.
Skipfish is quite a powerful and very fast Kali Linux tool capable of running up to 500 requests per second against internet-based targets, over 2000 requests per second on LAN, and up to 7000 requests against local instances. This shows how powerful this tool is.
This Kali Linux tool performs repeating crawling, and dictionary-based tests on your website URLs and creates a digital map of security checks performed so far and their results.
Once the scan completes, Skipfish produces a final report that security professionals can assess to ensure the security of their web application.
Skipfish can scan your web application against high-risk flaws, including server-side query injection, explicit SQL-like syntax in GET or POST parameters, server-side shell command injection, format string vulnerabilities, and more.
10. CMSMap
CMSMap is another web-app scanning tool for Kali Linux. Still, unlike WPScan and Skipfish, it mainly focuses on the top four most popular CMS platforms, including WordPress, Drupal, Joomla, and Moodle. It is one of the most popular CMS vulnerability detection tools.
What I like about CMSMap is that it is completely open-source, unlike WPScan, and is written in Python. This makes it a perfect choice for automating the process of vulnerability and loopholes scanning in any of these CMS platforms.
On top of that, due to its open-source nature, you can modify the source code and make this tool yours with custom scripts.
CMSMap runs multiple scans for all known threats, which makes it a handy tool for detecting security flaws. In addition, it can also be used to run brute force attacks to see how strong your passwords are. You can even launch exploits using this tool once it finds any vulnerability.
CMSMap is not just a tool to identify security flaws but can also be used to attack targets. It supports SSL encryption and verbose mode to debug known issues. Once it generates a report, you can export it in a text file to analyze it further.
11. Metasploit Framework
Metasploit Framework is one of the most popular penetration testing frameworks. It is a Ruby-based framework to create, test, and execute exploits against remotely located hosts. This Kali Linux tool is released under a BSD-style license, meaning you will have access to the tool.
Metasploit offers an open-source tool that is freely available for all users and can be modified as they want.
Besides that, a commercial version of the tool comes with additional in-built features such as network discovery, basic exploitation, remote API integration, automation and infiltration features, and more.
There is no doubt that the commercial tool is great for penetration testing, but that doesn’t mean you cannot do much with the open-source version of Metasploit.
It offers you access to a bunch of security tools that can be used for testing, such as finding targets, launching scans, exploiting security flaws, collecting available data, and more.
The free version of Metasploit Framework is quite powerful, and arguably, I can say that it is one of the best security auditing and penetration testing tools that are freely available.
Metasploit can be installed on other Linux distributions and Windows computers along with Kali Linux.
12. John the Ripper
John the Ripper is one of the most popular multi-platform cryptography testing tools. It is available for 15 platforms, including Linux, Unix, Windows, macOS, and OpenVMS. It is released under GNU General Public License along with a proprietary version.
For most people, the free version of this Kali Linux tool will be more than sufficient. However, if you want additional features such as support for hash types such as DES-based Unix crypt(3), bigcrypt, Kerberos AFS DES-based hashes, and more, the proprietary version might be a worthy choice.
The free version of John the Ripper is quite powerful as it combines several password crackers and breaks programs into a single package. Further, it can auto-detect hash types and includes a highly configurable cracker that can be run against several encrypted password formats.
The most common password-cracking methods of John the Ripper include dictionary attacks and brute force attacks.
Besides that, it automatically changes the decryption method, as per the detected algorithm, which makes the entire process automatic.
In addition, John the Ripper lets you define custom letters and words for building a list for dictionary attacks. Similarly, it lets you configure brute force rules.
13. Kismet Wireless
Next, we have Kismet Wireless on our list. This is an awesome Kali Linux tool that can be used to detect wireless networks and devices, sniffing, wardriving, and wireless intrusion detection. Kismet Wireless works best with Wi-Fi interfaces, Bluetooth interfaces, SDR hardware such as RTLSDR, and other specialized capture hardware.
The best thing about Kismet Wireless is that it can be used for almost any wireless card that supports raw monitoring mode. Besides that, it can be used to sniff traffic from 802.11a, 802.11b, 802.11g, and 802.11n networks.
It is a multi-platform tool and runs flawlessly on Linux, macOS, OpenBSD, FreeBSD, and other platforms. It can also be used in the Windows platform, but only one supported hardware is available for Windows as a packet source.
Some of the best features of Kismet Wireless include its ability to run in passive mode, easy and fast detection of wireless clients and their access points, intrusion detection system, network logging, channel hopping, and scan wireless encryption level of any given access point.
14. Social Engineering Toolkit
Social Engineering is one of the most common and widely used techniques in information security. This technique exploits human errors to gain personal information, such as their contact number, location, and more which can help you in various ways.
This Social Engineering Toolkit helps you kickstart and automate this process. It is an open-source python-based penetration testing framework originally written by David Kennedy, the founder of TrustedSec.
This Social Engineering Toolkit allows you to launch various types of attacks, such as Wi-Fi AP-based attacks that allow you to redirect or intercept packets from various users who are using our Wi-Fi network. Besides that, you can also launch SMS and email attacks that trick your victim into entering their account credentials.
This toolkit makes creating web-based attacks such as DNS spoofing and phishing easy. Lastly, it lets you create payloads very easily.
It also lets you integrate with other third-party modules, making it one of the most configurable and best social engineering tools for Kali Linux.
15. BeEF
Next, we have BeEF on our list. BeEF stands for Browser Exploitation Framework, a very powerful tool that allows you to scan browser vulnerabilities and flaws that can be used to exploit the host. BeEF uses JavaScript, making injecting codes to vulnerable pages easier.
Unlike other security tools, BeEF mainly looks for browser-side vulnerabilities. Once it finds exploitability, it lets you create beachheads that can be used to launch directed command modules and further attack the system of the victims.
Some of the main features of BeEF include Metasploit integration, interprocess communication & exploitation, host & network reconnaissance, history gathering & intelligence, and browser plugin detection.
You can have BeEF on your Linux or macOS machine. However, it is not available for Windows OS.
✅FAQ
What are the top Kali Linux tools for Ethical Hackers?
The Linux distribution Kali Linux, based on Debian, is supported by Offensive Security. Mati Aharoni and Devon Kearns created it.
For people who work in cybersecurity and analysis, Kali Linux is an operating system created explicitly for network analysts and penetration testers.
Some of the top kali Linux tools are Nmap, Burp Suite, Wireshark, Metaspoilt framework, Aircrack-ng, john the ripper, sqlmap, autopsy, social engineering toolkit, etc.
Is Parrot better than Kali?
Parrot OS is superior in providing tools and an interface that is simple for beginners. However, both Kali Linux and Parrot OS give students a wide range of resources they can employ.
What are the features of Kali Linux?
Kali Linux features a unique project called Kali NetHunter that is intended for interoperability with and porting to particular Android devices.
The first open-source Android penetration testing tool for Nexus devices was developed by “BinkyBear,” a member of the Kali community and Offensive Security.
It supports Wireless 802.11 frame injection, one-click MANA Evil Access Point configurations, HID keyboard (attacks akin to Teensy), and lousy USB MITM attacks.
Why is Kali Linux better than others?
Cyber security professionals, penetration testers, and white-hat hackers are the main target audience for Kali Linux’s development.
Parrot OS, BlackArch, and Wifislax are a few additional distributions specializing in penetration testing. With characteristics like the default user being the Kali Live Environment superusers, Kali Linux has distinguished itself from these other distributions in penetration testing and cyber security.
What is the Ghost Phisher tool?
A wireless network audit and attack tool called Ghost Phisher creates a false access point for a network to trick a victim into connecting.
The victim is then given an IP address. The program can launch several attacks, including session hijacking and credentials phishing.
How powerful is Kali Linux?
Except for Apple, Kali will be able to run on the majority of the current hardware. “Windows PCs” are included in this. Therefore, after Kali is installed, your machine will go from running Windows to running Linux.
What tools does Kali Linux use?
The Linux operating system distribution made exclusively for ethical hacking and penetration testing is called Kali Linux.
It includes a wide range of instruments made to handle various hacking and security testing jobs.
Some of the tools that are included in Kali Linux are:-
Aircrack-ng: A tool for cracking wireless network keys.
Burp Suite: A tool for testing web applications for vulnerabilities.
Maltego: A tool for analyzing and visualizing data from various sources.
Metasploit: A tool for testing and exploiting vulnerabilities in systems and networks.
Nmap: A tool for scanning networks and discovering open ports and services.
Wireshark: A tool for capturing and analyzing network traffic.
The tools that are part of Kali Linux are only a few examples. The bundle has many other tools for various hacking and security testing jobs.
What are Kali top 10 tools?
Here are the top 10 tools included in Kali Linux:-
Aircrack-ng: A tool for cracking wireless network keys.
Burp Suite: A tool for testing web applications for vulnerabilities.
Maltego: A tool for analyzing and visualizing data from various sources.
Metasploit: A tool for testing and exploiting vulnerabilities in systems and networks.
Nmap: A tool for scanning networks and discovering open ports and services.
Wireshark: A tool for capturing and analyzing network traffic.
John the Ripper: A tool for cracking passwords.
sqlmap: A tool for testing and exploiting SQL injection vulnerabilities.
Hydra: A tool for performing brute-force attacks on login credentials.
Burp Suite: A tool for testing web applications for vulnerabilities.
Are Kali Linux tools open source?
Yes, a significant portion of Kali Linux’s tools is open-source programs. Software that is freely usable, modifiable, and distributable is referred to as open-source.
Some examples of open-source tools included in Kali Linux are:-
Aircrack-ng: A tool for cracking wireless network keys.
Burp Suite: A tool for testing web applications for vulnerabilities.
Maltego: A tool for analyzing and visualizing data from various sources.
Metasploit: A tool for testing and exploiting vulnerabilities in systems and networks.
Nmap: A tool for scanning networks and discovering open ports and services.
Wireshark: A tool for capturing and analyzing network traffic.
What tools are included with Kali Linux?
Here is a partial list of tools that are included in Kali Linux:
Aircrack-ng: A tool for cracking wireless network keys.
Burp Suite: A tool for testing web applications for vulnerabilities.
Maltego: A tool for analyzing and visualizing data from various sources.
Metasploit: A tool for testing and exploiting vulnerabilities in systems and networks.
Nmap: A tool for scanning networks and discovering open ports and services.
Wireshark: A tool for capturing and analyzing network traffic.
John the Ripper: A tool for cracking passwords.
sqlmap: A tool for testing and exploiting SQL injection vulnerabilities.
Hydra: A tool for performing brute-force attacks on login credentials.
Burp Suite: A tool for testing web applications for vulnerabilities.
Do hackers use Kali?
While ethical hackers and security experts frequently use Kali Linux to evaluate and enhance the security of systems and networks, bad hackers also utilize it for illicit activities.
It’s crucial to remember that it’s unethical and illegal in many places to use Kali Linux or any other hacking tool for illicit activities. Serious repercussions, such as fines and incarceration, may follow for using these tools for unlawful purposes.
With the owners’ consent, ethical hackers and penetration testers use hacking tools and techniques to evaluate and enhance the security of systems and networks. It’s crucial only to utilize these technologies in morally correct ways and to abide by all rules and laws.
Is Kali Linux OK for beginners?
For newcomers who want to learn about ethical hacking and penetration testing, Kali Linux might be a decent option.
The usage of Kali Linux is not recommended for beginners; it should be noted since these tasks require specific training and expertise.
Without the right information and awareness, using Kali Linux or any other hacking tool can be risky and may result in negative outcomes such as security breaches and legal problems.
Starting with core information and abilities, including computer networking and programming, is advised if you are a newbie and wish to learn about ethical hacking and penetration testing.
You may get started using various online tools, including tutorials and courses.
Is Kali better than Ubuntu?
Although Ubuntu and Kali Linux are variations of the Linux operating system, their aims are distinct.
A distribution known as Kali Linux was created primarily for ethical hacking and penetration testing. It contains a wide variety of tools made to carry out different hacking and security testing-related tasks.
Contrarily, Ubuntu is a general-purpose distribution created for various tasks, including desktop, server, and cloud applications. Various software programs appropriate for daily usage are included, together with an intuitive user interface.
Kali Linux and Ubuntu are dependable and well-maintained distributions in terms of performance and stability.
It’s important to note that while Ubuntu is also built on Debian, Kali Linux has a different emphasis on user-friendliness and is known for being more stable and reliable.
Which ” better ” distribution will depend on your needs and preferences. Kali Linux might be a better option if you’re interested in penetration testing and ethical hacking.
Ubuntu might be a better option if you’re seeking a multipurpose operating system for daily use.
Does Kali use Python?
Yes, Python is a supported programming language in Kali Linux.
A sizable selection of tools, many of which are written in Python or have Python bindings, are included with Kali and are intended to carry out various hacking and security testing tasks.
The Metasploit framework, for instance, is developed in Ruby but also provides a Python API (Application Programming Interface) that enables Python scripts to communicate with the system. This framework is a part of Kali Linux.
Other programming languages, including C, C++, and Perl, are also included in Kali Linux in addition to Python.
These languages are frequently used in security testing and hacking, and Kali Linux includes them to give developers a wide range of options for creating tools and scripts.
Do professionals use Kali?
Penetration testing and ethical hacking are crucial processes that advance the safety of networks and systems.
Kali Linux is a popular choice for these professionals due to its extensive range of tools. Many companies and businesses hire ethical hackers and security professionals to carry out these duties.
Can I run Kali Linux on 4 GB RAM?
The answer is yes; you can run Kali Linux on a machine with 4 GB of RAM, although it might not operate as effectively.
While Kali Linux and some of its tools may be used with 4 GB of RAM, more difficult tasks could require additional RAM.
To ensure optimum performance, you might require more RAM if you utilize Kali Linux for virtualization or run numerous applications simultaneously.
It’s important to remember that the amount of RAM you require will depend on the tools you’re using and your usage scenario.
At least 8 GB of RAM, if not more, is advised if you intend to utilize Kali Linux for resource-intensive operations.
In conclusion, while Kali Linux may be used on a PC with 4 GB of RAM, performance issues may arise if you use resource-intensive tools or run numerous applications simultaneously.
Why is Kali Linux called Kali?
The Hindu goddess Kali, regarded as the remover of ignorance and the defender of the oppressed, inspired the name of the Linux operating system Kali. The Sanskrit word “kala,” meaning time, is the source of the name Kali.
The Kali Linux developers selected the Kali moniker because they felt it accurately reflected the distribution’s strength and capabilities.
Since these processes entail finding and “killing” vulnerabilities in systems and networks, the name also conveys the distribution’s emphasis on security and penetration testing.
Offensive Security, a business specializing in cybersecurity services and training, is responsible for the development and upkeep of Kali Linux.
The business named the distribution Kali Linux in honor of the Hindu goddess, representing its emphasis on security and penetration testing.
Is Kali good for Programming?
Although Kali Linux was not created with programming in mind, it does come with several programming languages that can be used for development. Python, C, C++, and Perl are a few programming languages on the Kali Linux operating system.
These languages are frequently used in security testing and hacking, and Kali Linux includes them to give developers a wide range of options for creating tools and scripts.
In addition to the programming languages, Kali Linux also comes with several libraries and development tools that can be used for programming. For example, it includes the GCC (GNU Compiler Collection) and Make, which are tools that are commonly used in software development.
Overall, despite Kali Linux’s lack of a focus on programming, it provides various programming languages and development tools that can be applied to programming tasks.
A distribution like Ubuntu or Fedora can be a good option if you’re searching for one specially made for programmers.
Is Kali Linux hard to learn?
Learning to use Kali Linux properly could take some time if you are new to Linux or have little prior expertise with operating systems and computer networks.
But anyone can master Kali Linux if they desire to learn and are dedicated to putting in the time and effort.
You can start using Kali Linux and learn how to use its many tools thanks to the available internet materials and tutorials.
What’s better than Kali Linux?
BlackArch is a Linux distribution based on Arch Linux, a Kali Linux substitute created with penetration testing and ethical hacking in mind. BlackArch has approximately 2000 tools for these jobs and is regularly updated.
Another choice is Parrot OS, a Linux distribution made specifically for digital forensics, ethical hacking, and penetration testing. Parrot OS has a large selection of tools for various uses based on the stable and secure Debian operating system.
The ideal operating system for penetration testing and ethical hacking will ultimately depend on your requirements and tastes.
When selecting an operating system or toolkit, it is important to consider your needs, expertise level, and any unique requirements you may have.
What code do hackers use?
Depending on the exact goals they are seeking to achieve, hackers employ a range of computer languages and tools.
Some common programming languages that are used in hacking include:-
Python:- In cybersecurity, Python is a well-liked, high-level programming language. It is known for being straightforward to read, making it easy to learn and use.
C:- Writing effective and quick code requires the usage of the low-level programming language C. It is frequently used to create compilers, operating systems, and other system-level software.
C++:– Code written in C++ is effective and high-performing since it is an extension of the C programming language. Software for operating systems, games and other applications is frequently created using it.
Java:- A wide variety of applications, including web and mobile, are created using the well-liked programming language Java. Both its mobility and security advantages are well-known.
Ruby:– Ruby is a high-level programming language used to create clear and concise code. Web applications and other types of software are frequently created with it.
PHP:– Web apps are created using the computer language PHP. Databases and web servers are frequently used in conjunction with it.
Hackers employ a range of frameworks, tools, and programming languages in addition to these to carry out activities, including network security audits, ethical hacking, and digital forensics. Kali Linux, Metasploit, and Wireshark are examples of these tools.
Closing Comments
There you have it – a list of the best Kali Linux tools.
Kali Linux is arguably the best operating system for hacking and penetration testing. It offers a massive collection of tools that makes it easier to test, hack, and perform almost any task related to digital forensics.
Whether you are planning to be a hacker, security professional, or just a normal person who wants to save himself from getting hacked, Kali Linux is the way to go.
Even though you can perform most of the tasks without using any Kali Linux tools, these tools can help you automate the most time-consuming hacking or penetration testing processes. In addition, these tools will also help you increase your efficiency and save a lot of your time and effort.