In today’s digital age, the growing concern for businesses, both big and small, is cyber threats. One major factor contributing to these threats is vulnerable websites.
Unfortunately, these digital portals, intended to serve various purposes – from eCommerce to information dissemination- open doors to hackers who exploit weaknesses to steal sensitive data or disrupt operations.
The severity of the problem goes beyond a minor inconvenience. Cyber-attacks can cause massive financial losses, damage brand reputation, and even lead to legal repercussions.
Worse still, hackers are becoming increasingly sophisticated, and outdated security measures no longer suffice. A single breach can spell disaster for any organization, especially smaller businesses that may never fully recover.
This is where the role of penetration testing and ethical hacking becomes critical. By simulating cyber-attacks, they expose potential security weaknesses and provide actionable recommendations to fortify defenses.
To understand this further, we’ve curated a comprehensive guide that covers everything you need to know about ‘Vulnerable Websites’ for Penetration Testing and Ethical Hacking Training.
This article will walk you through the fundamentals of identifying website vulnerabilities, how penetration testing works, and how to leverage ethical hacking techniques to protect your business.
Let’s dive in and start fortifying your cyber defenses.
Importance of Hands-on Practice in Penetration Testing
Penetration testing, an integral aspect of cybersecurity, is pivotal in safeguarding digital systems against potential threats.
Simulating real-world attacks helps organizations identify vulnerabilities and fortify their defenses. However, understanding the importance of hands-on practice is key to mastering the art of penetration testing.
The hands-on practice holds immense value in the realm of penetration testing. It allows security professionals to gain practical experience and refine their skills. By actively engaging in simulated attacks, testers can develop a deep understanding of the methodologies employed by malicious actors and stay one step ahead.
Furthermore, hands-on practice allows testers to explore diverse attack vectors and identify novel and unexplored vulnerabilities. This practical approach nurtures their problem-solving abilities and fosters a creative mindset to detect and mitigate potential risks.
One of the key advantages of hands-on practice is its familiarity with various tools and frameworks utilized in penetration testing, such as Metasploit, Burp Suite, and Nmap. Through consistent practice, professionals can become well-versed in applying these tools and optimize their utilization to uncover vulnerabilities effectively.
In conclusion, the importance of hands-on practice in penetration testing cannot be overstated. It empowers individuals to enhance their skills, expand their knowledge, and confidently confront the evolving landscape of cyber threats.
By embracing practical experiences, professionals can better protect organizations from potential security breaches and contribute to the overall resilience of digital environments.
Understanding the Legal and Ethical Boundaries of Penetration Testing
In cybersecurity, penetration testing is a crucial practice for organizations to assess their digital defenses. However, it is essential to comprehend the legal and ethical boundaries that govern this process to ensure responsible and lawful engagement.
Penetration testing involves deliberately attempting to exploit system vulnerabilities to identify weaknesses. While this practice is invaluable in uncovering security flaws, it must be conducted within a framework that respects legal and ethical considerations. On the legal front, organizations and testers must adhere to applicable laws, regulations, and agreements.
It is crucial to obtain proper authorization before initiating testing activities to avoid trespassing legal boundaries. Unauthorized penetration testing can have severe legal consequences, including civil and criminal liabilities.
Ethically, penetration testing should prioritize the principles of informed consent, transparency, and privacy. Testers should obtain explicit permission from the system owners and communicate the scope, methodology, and potential risks. Respecting privacy and confidentiality is paramount, ensuring that sensitive information remains protected throughout testing.
Understanding the legal and ethical boundaries of penetration testing fosters a responsible and professional approach. Organizations should engage reputable and qualified testers with the necessary expertise to navigate these boundaries. Additionally, ongoing education and awareness are essential to stay abreast of evolving legal and ethical frameworks in the cybersecurity landscape.
In conclusion, comprehending the legal and ethical boundaries is fundamental to conducting effective and responsible penetration testing. By upholding these principles, organizations can fortify their digital defenses while maintaining compliance with laws and ethical standards, ultimately safeguarding their assets and reputation in an increasingly interconnected world.
List Of Vulnerable Websites To Practice Penetration Tests Legally
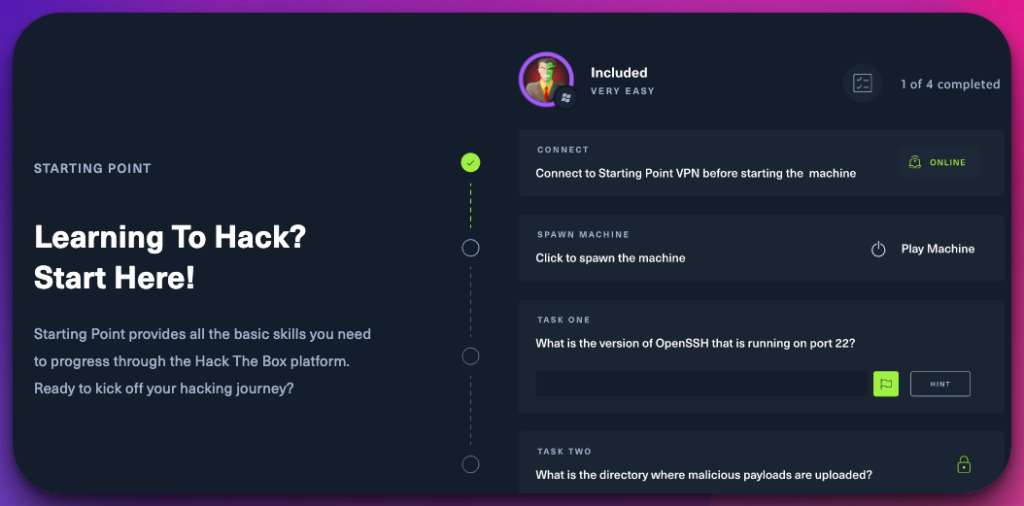
1. Hack The Box
Hack The Box is a revolutionary vulnerable test websites with significant attention to ethical hacking and cybersecurity. It offers a dynamic and immersive environment for individuals passionate about honing their hacking skills and staying ahead of emerging threats.
At its core, Hack The Box provides a virtual playground where users can engage in simulated hacking scenarios. By solving challenges and exploiting vulnerabilities in a controlled environment, participants can gain invaluable practical experience.
The platform encompasses challenges to test specific skills and techniques, such as web application hacking, network exploitation, and cryptanalysis.
One of the remarkable aspects of Hack The Box is its emphasis on a gamified approach. Users progress through different levels and earn points as they successfully conquer challenges. This gamification element adds an element of competitiveness and motivation, inspiring individuals to push their limits and continually enhance their skills.
Moreover, Hack The Box fosters a vibrant community of like-minded individuals. Users can collaborate, share knowledge, and engage in friendly competition. This collective learning environment encourages growth and facilitates the exchange of innovative ideas and techniques.
Hack The Box has become a go-to platform for ethical hacking enthusiasts worldwide with its vast collection of challenges, realistic scenarios, and engaged community. It serves as a training ground for aspiring cybersecurity professionals, enabling them to develop practical skills, stay abreast of the latest techniques, and contribute to the ongoing fight against cyber threats.
In conclusion, Hack The Box has revolutionized the world of ethical hacking by providing an immersive vulnerable websites platform that combines practical experience, gamification, and community engagement. It is an invaluable resource for individuals passionate about cybersecurity, equipping them with the tools and knowledge to navigate the ever-evolving digital security landscape.
Available Challenges:-
- Web application hacking challenges
- Network exploitation challenges
- Cryptanalysis challenges
- Reverse engineering challenges
- Steganography challenges
- Forensics challenges
- Malware analysis challenges
- Wireless network challenges
- Binary exploitation challenges
- Cryptography challenges
- Social engineering challenges
- Exploit development challenges
- Operating system and kernel challenges
- IoT (Internet of Things) hacking challenges
- Mobile application hacking challenges
- Password cracking challenges
- Network packet analysis challenges
- Web server security challenges
- Database security challenges
- Firewall evasion challenges
2. CTFlearn
CTFlearn has emerged as a leading platform in cybersecurity education, offering a gamified approach to learning and enhancing practical skills. With its extensive collection of Capture The Flag (CTF) challenges, the platform has become a go-to resource for individuals seeking hands-on experience in various facets of cybersecurity.
At its core, CTFlearn provides a dynamic environment where users can engage in simulated hacking scenarios. These challenges include web exploitation, binary analysis, forensics, cryptography, and more.
By solving these challenges, participants deeply understand the underlying concepts and develop critical problem-solving and analytical skills. The platform’s interactive and user-friendly interface encourages individuals to embark on their cybersecurity journey at their own pace.
Each challenge presents a unique problem to solve, often requiring a combination of technical knowledge, creativity, and persistence. As users progress through the challenges, they earn points, unlock achievements, and gain recognition within the CTFlearn community.
What sets CTFlearn apart is its commitment to fostering a collaborative learning environment. Users can discuss challenges, share techniques, and exchange insights with a vibrant community of like-minded individuals. This community-driven approach enhances the learning experience and promotes knowledge sharing and camaraderie.
In conclusion, CTFlearn has revolutionized cybersecurity education by providing a platform that combines gamification, practical challenges, and community engagement.
It empowers individuals to develop and refine their cybersecurity skills, preparing them for real-world scenarios. Whether you are a beginner or an experienced professional, CTFlearn offers an immersive and rewarding learning journey that helps you navigate the complex landscape of cybersecurity.
Available Challenges:-
- Web exploitation challenges
- Binary analysis challenges
- Forensics challenges
- Cryptography challenges
- Steganography challenges
- Network security challenges
- Reverse engineering challenges
- Password cracking challenges
- Wireless network challenges
- Exploit development challenges
- Malware analysis challenges
- OSINT (Open Source Intelligence) challenges
- Social engineering challenges
- Cryptocurrency challenges
- Mobile application security challenges
- IoT (Internet of Things) hacking challenges
- Incident response challenges
- Network packet analysis challenges
- Web server security challenges
- Database security challenges
3. HackThisSite
HackThisSite is a prominent platform for penetration testing and ethical hacking training, offering a unique and immersive experience for individuals seeking to develop their cybersecurity skills. As one of the top vulnerable websites, it provides a practical playground for enthusiasts to put their abilities to the test.
Designed to simulate real-world scenarios, HackThisSite presents many challenges that encompass a wide range of vulnerabilities and exploits.
This hands-on approach allows users to delve into the intricate world of cybersecurity, honing their penetration testing skills and understanding the methodologies employed by malicious actors. With its carefully crafted vulnerabilities, HackThisSite offers a dynamic and ever-evolving environment for individuals to explore.
Each challenge presents an opportunity to enhance knowledge and gain practical experience in ethical hacking, from web application vulnerabilities to network security weaknesses.
One of the remarkable aspects of HackThisSite is its vibrant community. Users can engage in discussions, seek guidance, and share insights with like-minded individuals, fostering collaboration and continuous learning. The platform encourages participants to embrace a proactive approach, empowering them to identify vulnerabilities, suggest improvements, and contribute to the website’s security.
In conclusion, HackThisSite is a top choice for individuals looking to develop their penetration testing and ethical hacking skills. By immersing oneself in its challenging and vulnerable environment, one can acquire practical knowledge, refine techniques, and ultimately contribute to the ever-growing field of cybersecurity.
Available Challenges:-
- Web application vulnerabilities
- Network security weaknesses
- Cryptographic puzzles
- Steganography challenges
- Forensics and digital investigation tasks
- Exploitation of binary vulnerabilities
- Password cracking and encryption challenges
- Social engineering scenarios
- OSINT (Open Source Intelligence) challenges
- Mobile application security vulnerabilities
- Reverse engineering tasks
- Malware analysis and detection challenges
- Network packet analysis and sniffing tasks
- Wireless network security weaknesses
- Web server misconfigurations and vulnerabilities
- Database security flaws and SQL injection challenges
- Firewall and network perimeter testing scenarios
- Incident response and forensic analysis simulations
- Secure coding challenges and best practices
- Exploit development and vulnerability research tasks
4. Google Gruyere
Google Gruyere is an exceptional choice for beginners seeking hands-on experience in vulnerability detection, exploitation, and mitigation. This web application, designed by Google, offers a practical and immersive platform for individuals eager to explore the world of cybersecurity.
With its intentionally created vulnerabilities, Google Gruyere serves as a controlled environment for beginners to locate and exploit vulnerabilities while learning the crucial techniques to defend against them.
Users can gain insight into common web security flaws through interactive challenges, including cross-site scripting (XSS), SQL injection, and authentication bypass.
What sets Google Gruyere apart is its user-friendly interface and comprehensive documentation. Beginners are provided with clear instructions and explanations, ensuring they understand the vulnerabilities they encounter and the methodologies required to exploit or mitigate them.
By engaging with Google Gruyere, beginners develop technical skills and cultivate a proactive and security-focused mindset. They learn the importance of identifying vulnerabilities and the strategies to fight against them, ultimately contributing to a safer online environment.
In conclusion, Google Gruyere is an excellent choice for beginners on their cybersecurity journey. Its practical challenges and user-friendly approach empower individuals to locate, exploit, and combat vulnerabilities. By gaining proficiency in vulnerability detection and mitigation, beginners lay the foundation for a successful and impactful career in cybersecurity.
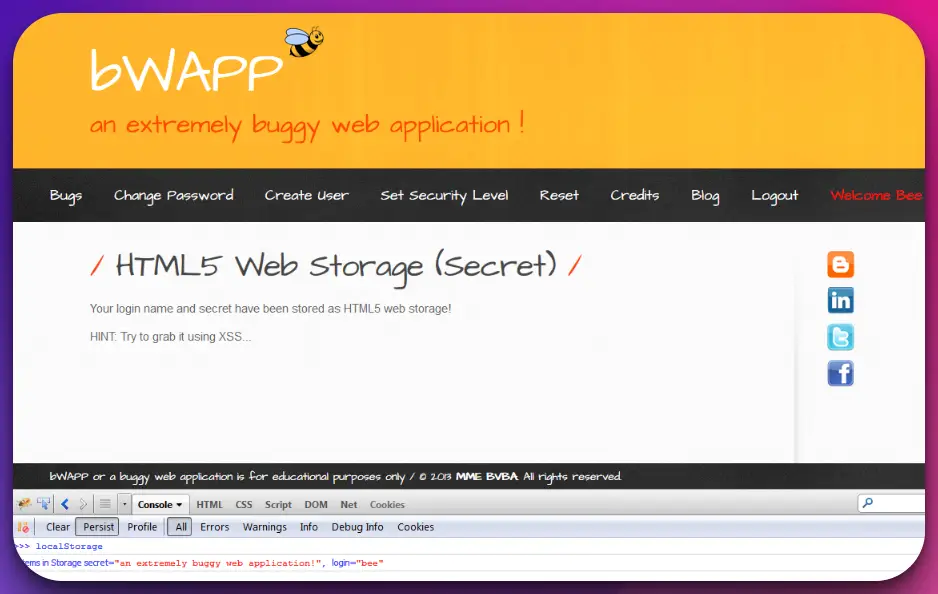
5. bWAPP
bWAPP (Download Here) stands as a remarkable platform in the realm of cybersecurity education, offering a practical and immersive experience for individuals seeking to develop their skills.
With its focus on a vulnerable web application, bWAPP provides a safe environment for learning and understanding various web security vulnerabilities and exploits.
Designed with many intentionally created vulnerabilities, bWAPP allows users to explore and exploit weaknesses in a controlled setting. This hands-on approach enables aspiring ethical hackers and penetration testers to enhance their understanding of the intricacies of web security.
Through its diverse challenges, bWAPP covers a wide spectrum of web vulnerabilities, including SQL injection, cross-site scripting (XSS), command injection, and many more.
Each challenge presents a unique opportunity to delve into the depths of web application security and gain practical experience in identifying and mitigating vulnerabilities.
One of the notable aspects of bWAPP is its user-friendly interface and comprehensive documentation, which provide clear instructions and guidance throughout the learning process. The platform caters to beginners and seasoned professionals, offering a progressive learning path for different skill levels.
With its emphasis on practicality and real-world scenarios, bWAPP is a valuable tool for individuals seeking to strengthen their cybersecurity expertise. By immersing themselves in this vulnerable web application, users can enhance their knowledge, refine their skills, and contribute to creating a more secure digital landscape.
Available Challenges:-
- SQL injection vulnerabilities
- Cross-site scripting (XSS) challenges
- Command injection exploits
- Remote and local file inclusion vulnerabilities
- Cross-site request forgery (CSRF) challenges
- Brute force attacks on authentication mechanisms
- Insecure direct object references
- Server-side request forgery (SSRF) challenges
- XML external entity (XXE) vulnerabilities
- Security misconfigurations and information leakage challenges
- Session management flaws and session hijacking scenarios
- Insecure file upload vulnerabilities
- Server-side template injection challenges
- Cryptographic weaknesses and challenges
- API security vulnerabilities and exploitation tasks
- Code injection and code execution challenges
- Cross-origin resource sharing (CORS) misconfigurations
- Access control vulnerabilities and privilege escalation challenges
- Authentication bypass and account takeover scenarios
- Server-side and client-side validation bypass challenges
6. Damn Vulnerable Web Application
Damn Vulnerable Web Application (DVWA) is an innovative platform that has revolutionized how individuals learn and practice web application security. By providing a purposely vulnerable web application, DVWA offers a safe and controlled environment for aspiring cybersecurity professionals to develop and refine their skills.
DVWA presents various web security vulnerabilities and exploits, encompassing various categories such as SQL injection, cross-site scripting (XSS), command injection, and more.
Each vulnerability is a valuable learning opportunity, allowing users to understand the intricacies of web application security through practical, hands-on exercises.
The platform provides different security levels that cater to various skill levels, ensuring a progressive learning path for users.
Beginners can start with the lower security levels to grasp the fundamentals, while experienced individuals can challenge themselves with the higher levels that simulate real-world scenarios. One of the significant advantages of DVWA is its user-friendly interface and comprehensive documentation.
Clear instructions and guidance accompany each vulnerability, empowering users to tackle the challenges effectively and better understand web security concepts. By immersing themselves in DVWA, individuals can gain practical experience in identifying, exploiting, and mitigating vulnerabilities.
This experiential learning approach equips them with the necessary skills to protect web applications and contribute to building a more secure online ecosystem.
In conclusion, DVWA is an invaluable resource for individuals looking to enhance their web security skills. Providing a hands-on, vulnerable web application empowers cybersecurity enthusiasts to navigate the complex landscape of web vulnerabilities, fostering growth and contributing to the ongoing fight against cyber threats.
Available Challenges:-
- SQL injection challenges
- Cross-site scripting (XSS) challenges
- Command injection challenges
- Directory traversal vulnerabilities
- Insecure file upload challenges
- Brute force authentication challenges
- Remote file inclusion vulnerabilities
- Server-side template injection challenges
- Cross-site request forgery (CSRF) challenges
- Insecure direct object reference vulnerabilities
- Session management vulnerabilities
- XML external entity (XXE) challenges
- Cryptographic weaknesses and challenges
- Server-side request forgery (SSRF) vulnerabilities
- Authentication bypass challenges
- Code injection and execution vulnerabilities
- Information disclosure challenges
- Access control vulnerabilities and privilege escalation challenges
- Business logic flaws and manipulation scenarios
- API security vulnerabilities and exploitation tasks
7. WebGoat
WebGoat is a powerful and interactive platform that empowers individuals to delve into the intricacies of web security. With its diverse challenges, this open-source project provides a safe and controlled environment for learning and practicing various web application vulnerabilities.
Designed to foster a hands-on learning experience, WebGoat offers various interactive lessons and challenges covering various web security topics. Users can explore and exploit vulnerabilities in a controlled setting, from cross-site scripting (XSS) to SQL injection.
One of the notable features of WebGoat is its emphasis on interactive learning. Instead of relying solely on theory, users actively engage with the platform, discovering vulnerabilities, understanding their impact, and experimenting with different exploitation techniques. This practical approach enables learners to develop a deep understanding of web security principles.
Furthermore, WebGoat provides comprehensive documentation and guidance, ensuring users have the necessary resources to navigate the challenges. Detailed explanations and demonstrations accompany each lesson, empowering individuals to enhance their skills and knowledge.
By immersing themselves in WebGoat, individuals can unlock their web security potential. Whether a beginner or an experienced professional, this platform offers a unique opportunity to strengthen your skills, expand your knowledge, and contribute to building a more secure digital landscape.
In conclusion, WebGoat is an invaluable resource for individuals passionate about web security.
Its interactive challenges and comprehensive documentation enable users to acquire practical skills, cultivate a security mindset, and significantly contribute to the ever-evolving field of web application security.
8. Metasploitable 2
Metasploitable 2 is a purposefully vulnerable virtual machine that has become an indispensable asset for penetration testers and exploit developers.
Created by the Metasploit team, this intentionally vulnerable environment is a valuable tool to enhance practical skills in cybersecurity. With a wide array of pre-installed vulnerable applications and services, Metasploitable 2 presents a comprehensive range of attack vectors.
From web application vulnerabilities to network service exploits, this platform offers a simulated environment where users can practice exploiting weaknesses in a controlled manner.
The beauty of Metasploitable 2 lies in its realism and accuracy. The vulnerable applications and services closely mirror real-world scenarios, enabling users to experience and understand the intricacies of actual security flaws.
This hands-on approach fosters a deep comprehension of the vulnerabilities and techniques to exploit them. Metasploitable 2 integrates seamlessly with the powerful Metasploit Framework, a widely used tool for penetration testing and exploit development.
Users can leverage the framework’s extensive collection of exploits, payloads, and auxiliary modules to exploit vulnerabilities within the virtual machine.
By immersing themselves in Metasploitable 2, individuals can gain practical experience, sharpen their skills, and develop the expertise required to identify and mitigate vulnerabilities. It is an invaluable asset for cybersecurity professionals, enabling them to stay one step ahead of evolving threats and contribute to securing digital systems effectively.
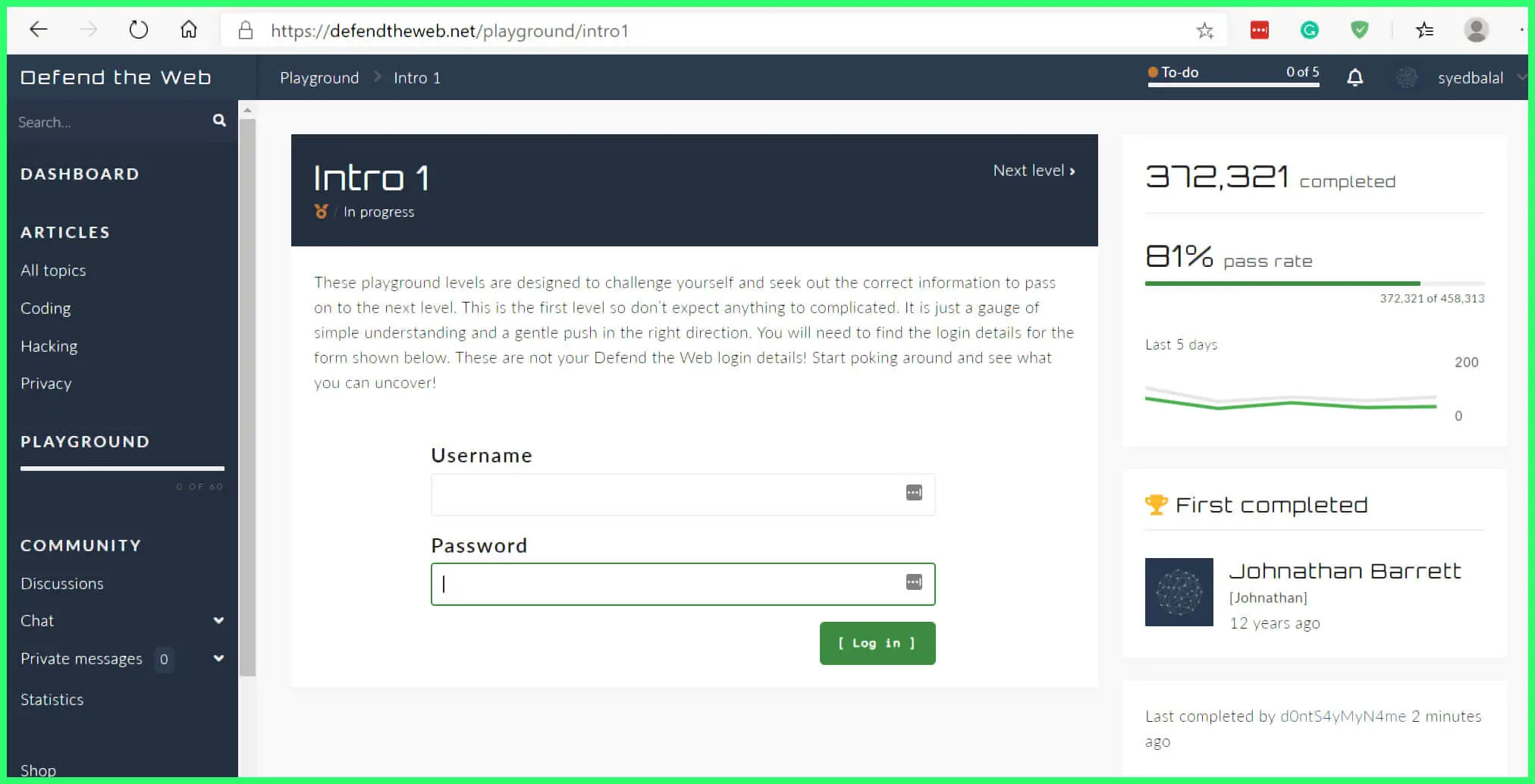
9. Defend the Web ( Formerly HackThis!)
Defend the Web (Formerly HackThis!) is an innovative platform that catalyzes cybersecurity enthusiasts, equipping them with the knowledge and skills necessary to protect the digital landscape. The platform empowers individuals to become cybersecurity guardians with its engaging challenges and educational resources.
Formerly known as HackThis!, Defend the Web embraces a proactive approach to cybersecurity. It encourages individuals to understand hacking techniques and employ that knowledge to fortify digital systems against potential threats. Providing practical challenges, it fosters hands-on experience in identifying and mitigating vulnerabilities.
The platform offers various challenges covering various aspects of cybersecurity, including network security, web application vulnerabilities, cryptography, and more. Participants can navigate these challenges, enhancing their understanding of attack vectors and the necessary countermeasures to defend against them.
Moreover, Defend the Web provides an interactive and collaborative environment. It brings together a community of like-minded individuals who can share insights, discuss strategies, and collaborate on solving challenges.
This collective effort strengthens the cybersecurity community, enabling a continuous exchange of knowledge and fostering innovation. In conclusion, Defend the Web (Formerly HackThis!) is a crucial platform for cybersecurity enthusiasts.
By engaging with its challenges and community, individuals can develop practical skills, enhance their understanding of cybersecurity principles, and contribute to safeguarding the digital realm.
10. Root me
Root Me is an exceptional platform for cybersecurity enthusiasts, providing an immersive and engaging experience in ethical hacking and penetration testing. With its wide array of challenges, this platform serves as a gateway to unlock the intricacies of cybersecurity.
At the heart of Root Me lies a collection of captivating challenges that cover various domains, including web security, network exploitation, forensics, cryptanalysis, and much more.
Each challenge presents a unique opportunity for individuals to delve into the depths of cybersecurity, testing their skills and problem-solving abilities.
One of the remarkable aspects of Root Me is its emphasis on a practical approach. Participants actively engage with vulnerable systems, honing their abilities to identify and exploit weaknesses. This hands-on experience allows users to comprehensively understand real-world scenarios, preparing them to tackle emerging cyber threats.
Furthermore, Root Me fosters a supportive community where users can connect, collaborate, and exchange insights. The platform encourages knowledge sharing, ensuring individuals can access resources, tutorials, and discussions that enhance their learning journey.
By immersing themselves in Root Me, individuals can unlock their potential in cybersecurity. With its diverse challenges and vibrant community, the platform equips enthusiasts with the skills and knowledge needed to navigate the complex landscape of cyber threats, fostering growth and contributing to a more secure digital environment.
How to Find Vulnerable Websites: Unveiling Security Weaknesses
Understanding how to find vulnerable websites is essential for ethical hackers, penetration testers, and security professionals. Uncovering these websites allows for identifying and remedying security weaknesses, contributing to a more robust and secure online environment.
Here are some effective methods to discover vulnerable websites:-
1. Search Engine Queries
Leveraging search engines with specific queries can help discover websites vulnerable to common security flaws. Utilizing advanced search operators and specific keywords, such as error messages or outdated software versions, can yield results pointing to potentially vulnerable websites.
2. Security Databases and Lists
Numerous security databases and lists catalog vulnerable websites. These resources often include websites with known vulnerabilities, misconfigurations, or outdated software versions. Staying updated with these databases enables security practitioners to proactively assess and secure vulnerable websites.
3. Web Application Scanners
Web application scanners are automated tools designed to detect vulnerabilities in web applications. These scanners employ various techniques to identify website vulnerabilities, including SQL injection, cross-site scripting (XSS), and directory traversal. One can pinpoint those susceptible to attacks by scanning a range of websites.
4. Bug Bounty Programs
Bug bounty programs, offered by organizations to incentivize vulnerability discovery, are an excellent source for finding vulnerable websites. Security researchers can participate in these programs and identify vulnerabilities in websites and web applications, earning rewards while enhancing cybersecurity.
5. Online Forums and Communities
Engaging with online forums and communities dedicated to cybersecurity can yield valuable insights into vulnerable websites. Members often share findings, techniques, and resources for discovering and exploiting vulnerabilities, providing a collective knowledge base for finding vulnerable websites.
6. Security News and Research
Keeping up with the latest security news and research can provide valuable information on recently discovered vulnerabilities. Researchers often publish their findings, including vulnerable websites, to raise awareness and encourage remediation. Subscribing to reputable security blogs, mailing lists, and following security conferences can yield valuable leads.
7. Targeted Crawling and Reconnaissance
Targeted crawling and reconnaissance involve scanning specific domains or industry verticals for vulnerable websites. By using tools like web crawlers and reconnaissance frameworks, security professionals can map out websites and identify potential weaknesses that could be exploited.
It is important to note that while finding vulnerable websites is essential for security research and testing, it must always be done ethically and legally. Any discovered vulnerabilities should be reported responsibly to the website owner or appropriate authorities to facilitate remediation.
In conclusion, knowing how to find vulnerable websites is critical for cybersecurity professionals. Individuals can uncover websites with security weaknesses by leveraging search engines, databases, web application scanners, bug bounty programs, online communities, security news, and targeted surveillance.
This knowledge empowers security practitioners to contribute to a safer digital ecosystem by assisting in vulnerability mitigation and promoting proactive security measures.
How do hackers find vulnerable websites?
The realm of cybersecurity is a constant battle between defenders and adversaries. As hackers continuously seek out vulnerabilities, understanding how they find vulnerable websites is crucial for safeguarding digital systems.
Let’s explore some of the methods employed by hackers in their quest:-
1. Automated Scanning Tools
Hackers utilize automated scanning tools, such as vulnerability and web application scanners, to crawl the internet and identify vulnerable websites. These tools leverage techniques, including fuzzing, SQL injection, and cross-site scripting (XSS), to uncover vulnerabilities.
2. Search Engine Queries
Hackers employ search engines to identify vulnerable websites by using specific search queries. They look for websites with common security flaws, misconfigurations, outdated software, or exposing sensitive information. Advanced search operators and targeted keywords can narrow down the search.
3. Security Bulletins and Public Disclosures
Hackers study security bulletins, advisories, and public disclosures to gain insights into vulnerabilities affecting specific software or websites. By monitoring these sources, hackers can identify websites that have not yet patched known vulnerabilities, making them potential targets.
4. Port and Service Scanning
Hackers perform port scanning to discover open ports on target websites. By identifying open ports and associated services, hackers can search for vulnerabilities specific to those services, such as outdated versions or misconfigurations.
5. Web Application Framework Vulnerabilities
Hackers exploit popular web application frameworks and content management systems (CMS) vulnerabilities. These frameworks often have publicly known vulnerabilities or weak configurations that hackers can target to gain unauthorized access.
6. Web Defacement and Domain Enumeration
Hackers actively look for defaced websites or compromised domains. They employ techniques like subdomain enumeration to identify websites that may be vulnerable to attacks. Hackers gain entry into vulnerable systems by exploiting weak subdomains or forgotten domains.
7. Reverse Engineering and Exploit Development
Some hackers specialized in reverse engineering software or discovering unknown vulnerabilities. By analyzing the inner workings of applications, they can identify flaws that others may have missed. This expertise allows them to develop custom exploits targeting specific vulnerabilities.
8. Social Engineering and Phishing
Hackers employ social engineering tactics to trick website administrators or users into divulging sensitive information or granting unauthorized access. By impersonating trusted individuals or organizations, they exploit human vulnerabilities to gain entry into websites.
It is important to note that this overview of methods is provided for educational purposes only, and their misuse is strictly discouraged. Ethical hacking and responsible disclosure are vital in securing vulnerable websites and systems.
Organizations must prioritize security measures such as regular patching, secure coding practices, vulnerability scanning, and ongoing security awareness training to mitigate the risk of website vulnerabilities. By taking proactive steps, organizations can reduce the likelihood of falling victim to malicious hackers.
In conclusion, understanding how hackers find vulnerable websites sheds light on their tactics and motivates organizations to enhance their security posture.
By staying vigilant, implementing robust security measures, and embracing ethical hacking practices, we can collectively safeguard the digital landscape from potential exploits and protect sensitive information from falling into the wrong hands.
📗FAQ’s
Is it illegal to scan a website for vulnerabilities?
The answer depends on the context and the intentions behind the scanning activity.
In many jurisdictions, unauthorized website scanning without obtaining proper permission is considered illegal. This is because such actions may violate laws related to unauthorized access, computer intrusion, or unauthorized use of computer resources.
Engaging in these activities without the website owner’s or authorized party’s explicit consent can lead to legal consequences.
However, there are exceptions where scanning for vulnerabilities is considered legal. Ethical hacking, also known as penetration testing, is a legitimate practice that involves authorized scanning of websites and systems to identify vulnerabilities and help organizations improve their security. Ethical hackers follow strict guidelines, obtain written consent, and operate within a legal framework.
It is crucial to consult local laws and regulations regarding vulnerability scanning to ensure legal compliance. Organizations should establish responsible disclosure programs and engage with ethical hackers who adhere to a code of conduct.
This collaboration helps balance protecting websites from malicious attacks and respecting legal boundaries.
What Are Vulnerable Apps?
Vulnerable apps refer to software applications with security weaknesses or flaws that malicious actors can exploit.
These vulnerabilities pose significant risks to the application’s confidentiality, integrity, availability, and the underlying systems it interacts with.
Various types of vulnerabilities can exist in apps, including:-
Input Validation Issues: Vulnerabilities arising from improper validation or sanitization of user inputs, which can lead to SQL injection, cross-site scripting (XSS), or command injection attacks.
Authentication and Authorization Weaknesses: Flaws in an app’s authentication and authorization mechanisms can result in unauthorized access or privilege escalation, compromising user accounts and sensitive data.
Insecure Data Storage: Failure to encrypt or securely store sensitive information, such as passwords or personal data, can expose it to unauthorized access or data breaches.
Inadequate Error Handling: Poor error handling can provide valuable information to attackers, aiding them in refining their attacks or exploiting system vulnerabilities.
Outdated or Unpatched Software: Apps running on outdated or unpatched software versions may have known vulnerabilities that attackers can exploit.
Insecure Configuration: Misconfigured apps can leave open doors for attackers, allowing them to bypass security controls or gain unauthorized access.
To mitigate the risks associated with vulnerable apps, developers and organizations should follow secure coding practices, conduct regular security assessments, and perform vulnerability scans and penetration testing.
Patching known vulnerabilities promptly and maintaining up-to-date software versions is crucial in reducing the attack surface.
Additionally, users should remain vigilant and keep their apps updated to benefit from security patches released by developers. Practicing good cybersecurity hygiene, such as using strong passwords and being cautious of phishing attempts, further enhances protection against potential vulnerabilities.
In conclusion, vulnerable apps are software applications with security weaknesses, making them susceptible to exploitation.
Addressing these vulnerabilities through secure development practices, regular assessments, and proactive patching is essential in maintaining the security and trustworthiness of applications in an increasingly digital landscape.
What Are 3 Risks of Websites?
Websites have become integral to our digital landscape, offering countless business opportunities, communication, and information-sharing opportunities. However, it is important to recognize the inherent risks that websites can pose.
Let’s explore three significant risks:-
Security Breaches:- One of the foremost risks of websites is security breaches. Cybercriminals exploit website vulnerabilities to gain unauthorized access, steal sensitive data, or launch attacks. These breaches can lead to financial loss, damage to reputation, and potential legal consequences.
Data Privacy Concerns: Websites often collect and store user data, making them potential targets for data breaches.
If proper security measures are not in place, personal information, such as names, addresses, and financial details, can be exposed. This can result in identity theft, fraud, or compromise of user privacy.
Malware and Phishing: Websites can unknowingly host malicious software (malware) or become vehicles for phishing attacks. Malware can infect visitors’ devices, compromising their security and privacy.
Phishing attempts deceive users into revealing sensitive information, such as login credentials, through fraudulent websites, posing significant risks.
Mitigating these risks involves implementing robust security measures, including regular security assessments, secure coding practices, encryption of sensitive data, and prompt patching of vulnerabilities.
Web administrators should also stay updated on the latest threats and follow best practices to ensure a safe browsing experience for users.
Users, on their part, should exercise caution while browsing the web, keep their devices and software up to date, and remain vigilant against phishing attempts or suspicious websites.
By understanding and addressing these risks, website owners and users can collaboratively create a safer online environment, preserving data privacy and protecting against potential threats.
What Types of Websites Are Safe?
In an increasingly interconnected world, ensuring online safety is paramount. When determining what types of websites are safe, several factors contribute to their overall security.
Let’s explore key aspects that characterize safe websites:-
HTTPS Encryption: Safe websites utilize HTTPS (Hypertext Transfer Protocol Secure) encryption to protect data transmitted between users and the website. This ensures that information remains confidential and secure from unauthorized access.
Reputable and Verified Sources: Safe websites often come from reputable sources, such as established businesses, government entities, educational institutions, or recognized organizations. These sources are more likely to prioritize security measures and maintain a trustworthy online presence.
Regular Security Updates: Websites prioritizing safety implement regular security updates to address vulnerabilities and protect against emerging threats. This includes promptly applying patches, fixing software vulnerabilities, and keeping their systems current.
Secure Payment Processing: E-commerce websites handling financial transactions should employ secure payment gateways, indicated by SSL certificates and trusted third-party processors. This helps ensure that sensitive payment information remains encrypted and protected.
Privacy Policies and Data Handling: Safe websites have clear and transparent privacy policies, outlining how user data is collected, stored, and utilized. They adhere to privacy regulations and provide users with control over their personal information.
Positive User Reviews and Ratings: User feedback and ratings can provide insights into the safety and reliability of websites. Websites with positive reviews and a track record of customer satisfaction are generally considered safer options.
While these factors contribute to website safety, it’s important to note that no website is completely immune to risks. Regular user awareness, adoption of strong passwords, and use of reputable security software are essential for maintaining personal online safety.
Website owners and developers can create safer online environments by prioritizing security measures, adhering to industry best practices, and leveraging technologies such as HTTPS encryption.
This ensures that users can confidently navigate the digital landscape, protecting their privacy and security.
What Websites Get Hacked the Most?
In the ever-evolving landscape of cybersecurity, it is crucial to understand what websites get hacked the most to address vulnerabilities and bolster defenses effectively.
While no website is immune to attacks, certain factors make them more attractive targets for cybercriminals. Here are some common types of websites that frequently experience hacking incidents:
E-commerce Websites: E-commerce platforms handling financial transactions and storing valuable customer data often attract hackers seeking financial gain. Breaching these websites can lead to unauthorized access to payment information or personal data.
Government and Institutional Websites: Government websites or institutions dealing with sensitive information, classified data, or public services can be targeted for various reasons, including political motivations or access to valuable resources.
Content Management Systems (CMS): CMS-based websites, such as WordPress, Joomla, or Drupal, are often targeted due to their popularity and potential vulnerabilities resulting from outdated software versions, plugins, or weak user credentials.
Financial Institutions: Websites belonging to banks, insurance companies, or investment firms are prime targets for hackers seeking access to financial assets, personal information or conducting fraudulent activities.
Healthcare Portals: Healthcare websites storing sensitive patient data are lucrative targets for hackers. Medical records, personal information, and insurance details can be exploited for identity theft, blackmail, or financial gain.
Social Media Platforms: Social media platforms are attractive targets due to their vast user bases, personal data, and potential for spreading malicious content or conducting social engineering attacks.
It is important to note that cyberattacks can affect websites of any nature or scale. However, these categories tend to draw more attention due to the potential impact of a successful breach.
Implementing robust security measures, regularly patching vulnerabilities, educating users about best practices, and maintaining strong access controls are essential for mitigating risks and protecting websites against common hacking attempts.
In conclusion, understanding the types of websites often targeted by hackers provides valuable insights into the evolving threat landscape.
Website owners and administrators can fortify their defenses and safeguard against cyberattacks by prioritizing security measures and staying vigilant.
Can Hackers See What You Search? Unveiling the Privacy Implications
In an era where online privacy is paramount, many wonders, “Can hackers see what you search?” The answer lies in the complex web of internet security and data encryption.
Let’s explore the privacy implications of online search activities:-
Unencrypted Connections: When you search the web using unencrypted connections (HTTP), your search queries can be intercepted by hackers who have gained unauthorized access to your network. This can potentially expose your search activity to malicious actors.
Wi-Fi Sniffing: Hackers leveraging Wi-Fi sniffing techniques can intercept unencrypted search queries transmitted over public or compromised networks. This allows them to capture and analyze the data, potentially revealing your search history.
Man-in-the-Middle Attacks: In sophisticated attacks, hackers can position themselves between you and the websites you visit. This enables them to intercept and modify the data exchanged during your search activities, giving them visibility into your searches.
However, it is important to note that the risk of hackers seeing your search activity can be significantly reduced with proper security measures.
Secure search engines and websites that employ HTTPS encryption ensure that your search queries remain confidential, making it difficult for hackers to intercept and decipher your search data.
To enhance your online privacy, it is advisable to use virtual private networks (VPNs) to encrypt your internet traffic, avoid public Wi-Fi networks for sensitive activities, and be cautious of the websites you visit.
Regularly updating your devices, using strong passwords, and employing reputable security software fortifies your defenses against potential threats.
In conclusion, while the risk of hackers seeing what you search exists, adopting security measures and utilizing encrypted connections significantly reduces the likelihood of compromising your search activity.
By prioritizing online privacy and staying vigilant, you can confidently navigate the digital landscape and safeguard your personal information from prying eyes.
What Are 3 Risks of Websites?
Websites pose several risks to both users and website owners:-
- Data Breaches: If a website lacks proper security measures, hackers can access sensitive user data, such as personal information, login credentials, or financial details.
- Malware Infections: Malicious actors can inject malware into websites, infecting users’ devices when they visit the compromised site.
- Phishing Attacks: Websites can be used as a platform for phishing, where attackers impersonate legitimate sites to trick users into revealing sensitive information.
What Type of Websites Are Safe?
Websites that prioritize security and implement best practices are generally considered safe.
These websites use encryption protocols (HTTPS), regularly update their software, have strong access controls, and employ other security measures to protect user data.
Trustworthy e-commerce sites, financial institutions, and government websites often prioritize security to provide a safe browsing experience.
What Are Suspicious Websites?
Suspicious websites typically exhibit characteristics that raise concerns about their trustworthiness. These sites may contain deceptive content, promote scams, engage in phishing activities, or distribute malware.
Suspicious websites often have unprofessional designs, poor grammar and spelling, and unsolicited pop-ups or redirects.
What Websites Get Hacked the Most?
Websites with security vulnerabilities, outdated software, or weak security practices are more likely to get hacked. Small business websites, personal blogs, and websites running outdated CMS versions are often targeted due to their vulnerabilities.
Additionally, websites with valuable data, such as e-commerce sites and financial institutions, are attractive targets for hackers.
How Do I Know If a Website Is Safe?
To determine if a website is safe, you can consider the following:
- HTTPS: Check if the website uses HTTPS encryption, indicated by a padlock symbol in the address bar.
- Reputation: Research the website’s reputation by reading user reviews and checking for any reported security incidents or scams associated with the site.
- Security Indicators: Look for security seals or trust marks from reputable third-party organizations.
- Website Content: Evaluate the website’s content for professionalism, accurate information, and the absence of suspicious elements like unsolicited pop-ups or requests for sensitive information.
Is It Illegal to Scan a Website for Vulnerabilities?
In most cases, scanning a website for vulnerabilities without permission is considered illegal and unauthorized access.
Ethical hacking, also known as white-hat hacking, involves obtaining proper authorization to test website security. Unauthorized scanning of websites can potentially result in legal consequences.
Can Hackers See What Websites You Visit?
Hackers generally cannot see what websites you visit unless they have gained unauthorized access to your device or network.
However, internet service providers (ISPs) or other entities may track and monitor your online activities. Secure connections, such as encrypted VPNs, can enhance privacy and protect against unauthorized monitoring.
Can Someone Hack You Through a Website?
Yes, hackers can potentially hack your device through a compromised or malicious website. They may exploit vulnerabilities in your device’s software, browser, or plugins to deliver malware or execute malicious code.
It is essential to keep your devices and software updated, use reputable security software, and exercise caution when browsing the internet.
What Apps Are Not Safe?
Several factors can contribute to an app being considered unsafe:
- Unverified Sources: Apps downloaded from unofficial or unverified sources outside trusted app stores may be unsafe.
- Lack of Security Updates: Apps that do not receive regular security updates are more susceptible to vulnerabilities.
- Privacy Concerns: Apps that collect excessive user data or do not adhere to privacy best practices can threaten user privacy and security.
What Apps Are Most Likely to Be Hacked?
Apps that handle sensitive user data, such as financial apps, healthcare apps, and those containing personal information, are more likely to be targeted by hackers.
Additionally, popular apps with a large user base attract attention from attackers due to the potential impact of a successful breach.
What Are the Most Compromised Apps?
The most compromised apps may vary as new vulnerabilities are discovered and patched.
However, popular social media, messaging, and productivity apps have been targeted historically due to their widespread use and the potential to access personal information.
What Happens If You Visit an Unsecure Website?
Visiting an unsecure website can expose you to various risks, including:
- Malware Infections: Unsecure websites may contain malware that can infect your device, compromising its security and potentially stealing personal information.
- Data Breaches: Unsecure websites are more vulnerable to data breaches, leading to unauthorized access to your personal information, such as passwords, financial details, or email addresses.
What Makes a Website Not Safe?
Several factors can contribute to a website being deemed unsafe:-
- Lack of HTTPS: Websites without HTTPS encryption may not secure data transmitted between the user’s browser and the website, making it easier for attackers to intercept sensitive information.
- Malicious Code: Websites that contain malicious code, such as drive-by downloads or script injections, pose a risk to visitors.
- Phishing Attempts: Websites designed to trick users into revealing sensitive information, such as login credentials or financial details, are considered unsafe.
What Are 5 Dangers Online?
The online landscape presents various dangers:-
- Malware and Viruses: Malicious software and viruses can infect devices, compromising security and stealing personal information.
- Phishing and Scams: Online scams aim to trick users into revealing sensitive information or making fraudulent payments.
- Identity Theft: Cybercriminals can steal personal information to assume someone’s identity, leading to financial loss and reputational damage.
- Data Breaches: Organizations’ data breaches can expose users’ personal information, potentially leading to identity theft or unauthorized access.
- Cyberbullying and Online Harassment: Online platforms can be used for cyberbullying, harassment, and spreading harmful content.
Do Some Websites Have Viruses?
Some websites may contain viruses or malicious code intended to infect visitors’ devices.
These websites often exploit user browser, software, or plugin vulnerabilities to deliver malware. Having updated security software and exercising caution when visiting unfamiliar or suspicious websites is crucial.
What Are the Safest Website Domains?
Websites that use reputable top-level domains (TLDs), such as .gov (government), .edu (education), or .org (non-profit organizations), are generally considered safer.
These TLDs often require strict verification processes, enhancing the credibility and security of the associated websites.
What Types of Websites Should You Avoid?
It is advisable to exercise caution when interacting with the following types of websites:
- Unsecured Websites: Websites without HTTPS encryption or security measures are riskier to browse.
- Suspicious or Phishing Websites: Websites that exhibit suspicious behavior, unsolicited pop-ups, or request sensitive information should be avoided.
- Illegal or Illicit Websites: Websites associated with illegal activities, piracy, or the distribution of malicious content should be avoided.
What Websites Are Usually Blocked?
Websites that are typically blocked include those containing explicit adult content, pirated media, illegal activities, or malware.
Additionally, some organizations block certain social media platforms, online gaming sites, or streaming services to limit distractions or prioritize network resources.
What Does a Malicious URL Look Like?
Malicious URLs can take various forms, but some common indicators include the following:
- Misspelled URLs: Malicious URLs may contain intentional misspellings or slight variations of legitimate website addresses.
- Unusual Characters: URLs with excessive hyphens, underscores, or random characters may indicate a suspicious website.
- Long, Complex URLs: URLs with long strings of random characters or numbers may be associated with malicious intent.
- IP Addresses Instead of Domain Names: URLs that use IP addresses instead of recognizable domain names can be suspicious.
Who Is Most at Risk of Being Hacked?
While anyone using online services is at some risk of being hacked, individuals who engage in risky online behavior, such as clicking on suspicious links, downloading files from untrusted sources, or using weak passwords, are more vulnerable.
Additionally, high-profile individuals or those with valuable personal or financial information may be targeted more frequently.
How Many Websites Are Vulnerable?
The number of vulnerable websites is significant, as security vulnerabilities can be found in various websites across different industries and sectors.
With the evolving threat landscape, website owners and developers must prioritize security measures and regularly update their systems to mitigate vulnerabilities.
What Is the Biggest Internet Hack in History?
One of the largest internet hacks in history is the Yahoo data breach that occurred in 2013 and 2014. It affected approximately three billion user accounts and involved stealing sensitive information, including names, email addresses, and hashed passwords.
What Does a Black Lock Mean?
A black lock symbolizes that a website uses HTTPS encryption to secure the connection between the user’s browser and the website. It indicates that the website has an SSL/TLS certificate and that data transmitted between the user and the site is encrypted.
How Do I Open Unsafe Sites in Chrome?
While it is generally not recommended to open unsafe sites, Chrome allows users to proceed to an unsafe site by clicking on the “Advanced” link and selecting the “Proceed to [Website] (unsafe)” option. However, this should be done cautiously as it may expose you to risks.
How Do I Know If a Website Is Safe on My iPhone?
On an iPhone, you can look for the lock symbol in your browser’s address bar, which indicates a secure HTTPS connection. Additionally, you can rely on reputable security software or browser extensions that provide website safety ratings or warnings.
Can a Website Steal Information Just by Visiting It?
In most cases, websites cannot directly steal information just by visiting them. However, sophisticated attacks may exploit vulnerabilities in browsers or plugins to silently download malware or execute malicious code on your device.
It is essential to keep your software up to date and use reputable security software to mitigate such risks.
Can a Website Steal My Information?
Websites can potentially steal your information if designed with malicious intent or have security vulnerabilities.
These sites may employ techniques like phishing, cross-site scripting (XSS), or session hijacking to capture your sensitive data. It is crucial to be cautious when sharing personal information online and to trust reputable websites.
How Do Hackers Scan for Vulnerabilities?
Hackers scan for website vulnerabilities using various methods, including automated tools and manual techniques. Automated scanners can identify common vulnerabilities by examining website structures, input fields, or software versions.
Manual techniques involve analyzing website source code, and configurations, or conducting targeted testing to identify specific vulnerabilities.
Can a Hacker See Me Through My Phone?
In general, hackers cannot directly see you through your phone. However, they may compromise your device’s camera or microphone through malware or unauthorized access.
Keeping your device secure, using reputable software, and being cautious with app permissions can help mitigate these risks.
Can Hackers Look at Your Screen or Through Your Phone?
If your device is compromised, hackers can remotely view your screen or access data on your phone. This can occur through malware, unauthorized access, or social engineering attacks.
Strong security measures, such as using secure passwords and avoiding suspicious downloads, can help protect against such attacks.
Can Your Wi-Fi Get Hacked from a Website?
While browsing a website alone is unlikely to hack your Wi-Fi directly, attackers may exploit vulnerabilities in your Wi-Fi network, router, or connected devices through malicious websites.
Keeping your Wi-Fi network secure, using encryption, and regularly updating firmware can help mitigate these risks.
Can You Get Hacked Without Clicking a Link?
Yes, it is possible to get hacked without clicking a link. Attackers can exploit vulnerabilities in software or network configurations, use malicious ads, or deliver malware through infected files.
These attacks often rely on “drive-by” techniques, where simply visiting a compromised website can trigger the exploit.
Do Websites Spy on You?
Websites can collect information about online activities through cookies, analytics tools, or tracking technologies.
While this is often for legitimate purposes like improving the user experience or personalized advertising, it is crucial to review website privacy policies and manage your browser’s privacy settings to control the extent of data collection.
What Apps Should I Delete?
Deleting apps depends on individual preferences, needs, and concerns. Consider removing apps you no longer use, those that collect excessive personal information, or those associated with security or privacy incidents. Regularly reviewing and managing installed apps can help maintain a clean and secure device.
How Do I Check My Phone for Viruses?
To check your phone for viruses, use reputable mobile security software or antivirus apps for your device’s operating system. These tools can scan your device, detect potential malware, and help remove threats.
Which Apps Can Damage Your Phone?
Apps downloaded from unverified sources or containing malware or malicious code can potentially damage your phone. These apps may disrupt system functionality, steal personal information, or render your device unusable. It is crucial to download apps from trusted sources like official app stores.
Is There an App to See If Someone Is Snooping on Your Phone?
Several security apps can help detect unauthorized access or snoopers on your phone. These apps often provide features like intruder detection, app lock, or access logs to identify suspicious activities.
Look for reputable apps with positive user reviews and features aligned with your security concerns.
What App Gets Rid of Hackers?
There is no single app that can eliminate hackers. However, using reputable security apps, practicing good cybersecurity habits, and keeping your device’s software up to date can significantly reduce the risk of being hacked.
What Are Spy Apps Disguised As?
Spy apps can be disguised as legitimate apps, such as calculators, note-taking apps, or file managers. These apps may function normally while secretly collecting user data, monitoring activities, or providing unauthorized access to an attacker.
What Is a Suspicious App?
A suspicious app is an application that exhibits behavior or characteristics that raise concerns about its intentions or security risks. These apps may request excessive permissions, contain intrusive ads, or have a negative reputation due to security incidents or privacy concerns.
How Do I Find Unsafe Apps?
To identify unsafe apps, consider the following:
- User Reviews: Check user reviews and ratings on app stores to identify potential security or privacy issues reported by other users.
- App Permissions: Review the permissions requested by the app during installation. It may indicate a potential risk if they seem excessive or unrelated to the app’s functionality.
- Developer Reputation: Research the app developer’s reputation, credibility, and previous app releases to gauge their commitment to security and user privacy.
- Official App Stores: Download apps only from official app stores, as they usually have security measures to minimize the risk of malicious apps.
Conclusion
In conclusion, the danger posed by vulnerable websites cannot be underestimated. They present a tempting opportunity for malicious actors to exploit weaknesses for their gain.
However, these threats can be mitigated with the right knowledge and skills in penetration testing and ethical hacking.
The reality is that cyber threats will continue to evolve, so the approaches to combat them must evolve too. The tactics discussed in this article for identifying and rectifying website vulnerabilities serve as a starting point for this evolution.
Investing in penetration testing and ethical hacking training isn’t just a good idea; it’s a business imperative in our increasingly digital world.
Remember, the best defense is a good offense. Armed with the knowledge and tools acquired from this training, you’ll be well-equipped to identify vulnerabilities, harden your defenses, and stay one step ahead of hackers.
This proactive approach is the key to maintaining the integrity of your digital presence, preserving your brand’s reputation, and ensuring the continuity of your business operations. Stay vigilant, stay informed, and keep learning.