Users are often worried about their computer’s safety and completion of files installing, when they are downloading any file from the internet or installing any file, or transmitting any data, users try their best to do so, either by installing a certain type of software or by running an algorithm over the file.
In the same way, Checksum is one of the things that can be used to check the data’s integrity and can also help to verify the disk image.
A user can also use some other common techniques like simple parity check, two-dimensional parity check, and Cyclic Redundancy Check to testify the data’s integrity.
To expand your knowledge’s boundary about checksum, here are some of the information.
What is Checksum?
Many people start fretting when listening to the notion ‘checksum’ but in reality, there is nothing to fret about one single word.
The checksum is a unique set of letters and numbers that can be used to check the integrity of a file, data, which means a user can check whether there were any error or changes made during the time of transmission or transferring the data(it does not matter the data is downloaded or transferred).
Note:- The checksum is not used to verify the authenticity of the data.
During the time of transmission, the data may get affected due to noise and the bytes may change such as 0 can convert into 1 or 1 may change into 0 so to detect these changes a task can be done on it so Checksum is used as it is an error check method and is calculated better than VRC, CRC, and LRC.
Basis of Checksum:-
A user can check their data’s integrity as well as disk image by running a Checksum function or Checksum algorithm on the piece of data.
A computer technician can use different types of algorithms for performing checksum tasks on the data. The most common type of algorithms used to perform a checksum on the data is MD5 (Md5 checksum can also be generated with 128 bits hash value.
MD5 stands for message-digest algorithm 5. The Algorithm is supposed to be applied against the given data to create a checksum. This MD5 checksum can identify only unintentional corruption and can be exploited in the terms of malware), SHA-1, SHA-256, and SHA-512.
By using any of the algorithms a user will get the checksum of the same length. The algorithms use cryptographic hash functions that take the file and then made a unique pattern of numbers and letters just for the file.
The size of the file does not matter as the file of 1 MB will get the checksum of the same length as the file of 3 GB.
A simple old checksum would not be the best idea to verify because switching the bytes is very easy due to which the data can easily be exchanged but a user will not be able to detect the error which is expected to have the same checksum.
Therefore, it is recommended to have an advanced version of checksum algorithms which also includes the CRC (Cyclic Redundancy Check) algorithm so that it can even detect slight changes made in the data and can differentiate between an exclamatory mark and a full stop thus providing completely different checksum.
Difference between a Checksum value and a Hash value:-
A checksum is more often called a hash value, hash code, and even just hashes but a Checksum is a disparate application and having the complete opposite function from a hash value.
A checksum is used to find any error made in the file during the transmission or downloading of data whereas a hash value is used to assign the data a unique fingerprint.
Although the concept overlaps to some extent, the main difference is that the hash function is dependent on the statistical property of the key. Checksum and the hash function are designed and optimized differently. Checksum based hash function is also used to cryptograph the data.
How does Checksum detect the error?
A Checksum is applied on both the sender’s and receiver’s side to work. When the data is sent the sender affixed a checksum with the actual pieces of information and then forward it to the receiver’s side.
The sender can be anyone who is posting anything on the internet such as on a website and the receiver can be anyone who is downloading from the site.
The first step at the sender’s side is that the checksum program splits the data into equal subunits that is an n bit length which generally is a 16-bit length.
The converted data that is the equal subunits are then calculated by 1’s complimented method(is the value obtained by converting the bits in binary number) to get the sum of n bits.
The result which underwent 1’s Compliment method is the main thing attached in the end to the actual piece of information called Checksum. When a message is transmitted, the data are joined together with the checksum.
At the receiver’s end, the same procedures take place, and if the result came as zero then it means that the data is transferred safely without any error, and there is no need for any correction in the data. When the result does not come as o, it indicates that the data transmitted have errors in it.
To detect an error in the transmitted file different checksum algorithms can be used such as Parity byte or Parity word, sum complement, position-dependent, fuzzy checksum, and General consideration. The above-explained algorithm is the function of Sum complement.
Uses of Checksum:-
The most common function of the checksum is to detect the error that can be made by noise during the transmission of the file as well as to check the file’s integrity and to ensure the file sent is original and a user can also use the checksum to verify large file at once very easily.
It is used to check that the data downloaded is the same as it was meant to be before downloaded and every part of the file is downloaded because if by any means it is not fully installed then it can cause a problem for the receiver.
A user can also use error detecting and correcting code that is based on checksum to not only detect the defects made by noise in the files, documents, but also to recover the original data in the mistaken areas.
Checksum comparison makes it very easy to develop a platform for delicacy checks. It is very easy to perform a checksum on the file and then compare the two obtained checksum so an unprofessional technician can also use the algorithm and deny any malicious file from entering the device.
A user can sometimes also use parity bits(check bits) and check digits that are some of the special checksum conditions and are best for the small block of the data.
Checksum produced at both the sender and receiver’s side is always the same but the addition of any malicious substance or noise can change the file and create a big difference in the checksum produced; this probably can help in easy identification of a slight change in any form of the data.
To Check the checksum value of any file on windows, open the PowerShell from the Start menu (Seach Powershell in the start menu) and enter the below command
Get-FileHash C:\YourFile Path -Algorithm MD5
Get-FileHash C:\Your File Path -Algorithm SHA1
Like in my case I just downloaded one wireshark.exe from their website and I just want to verify that the file I downloaded is the correct file or no, which means there is no modification happened between original source to my PC.
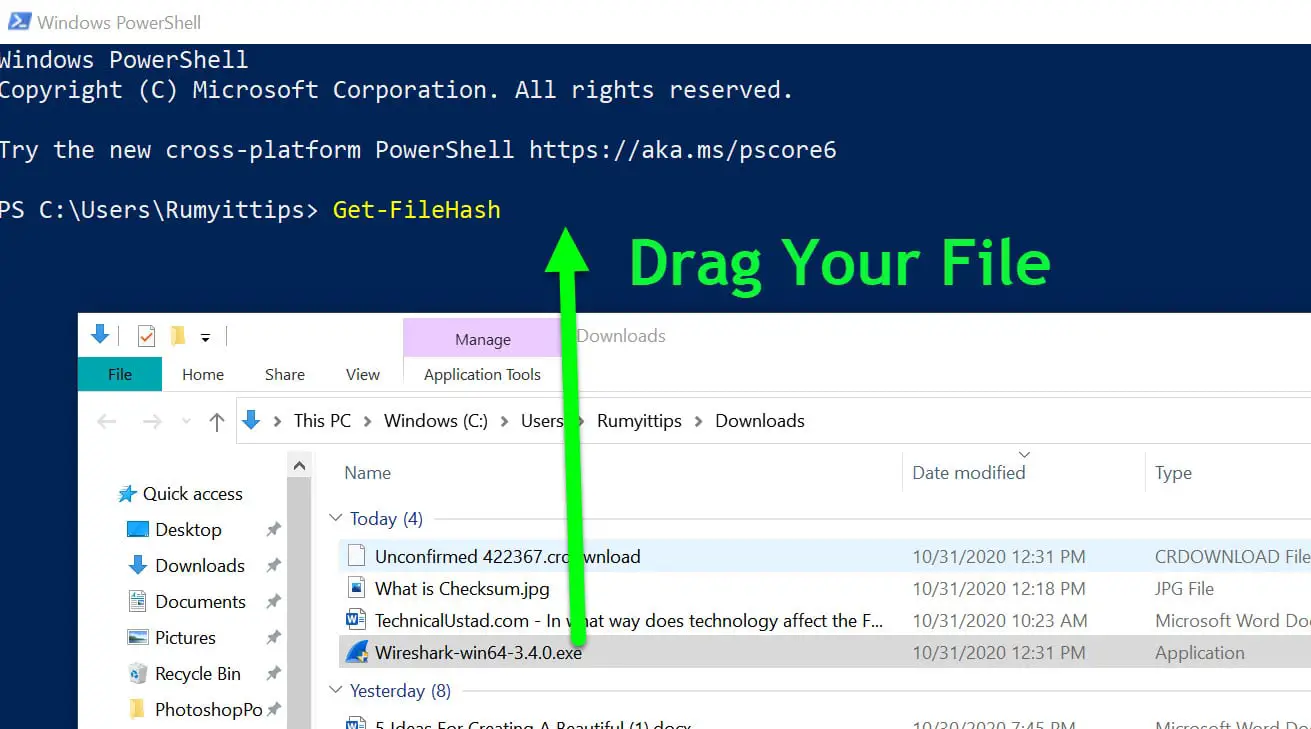
On the PowerShell, enter the Get-FileHash and drag your File on the PowerShell window and add the -Algorithm SHA1 or MD5 in last
so my command will look like the below command
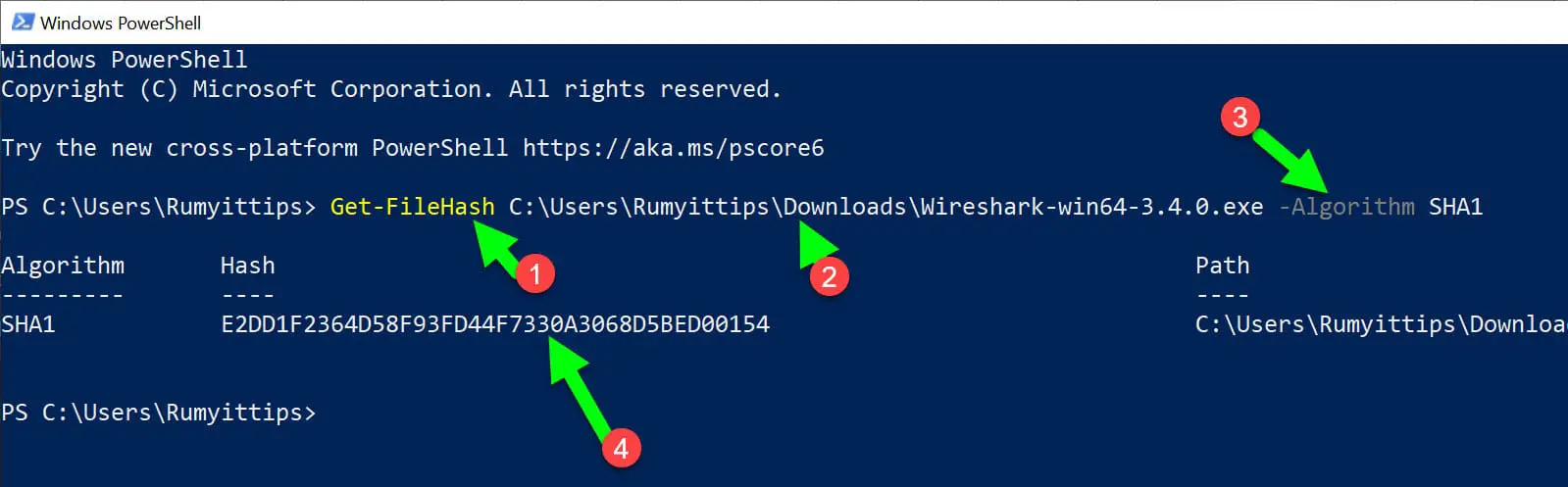
Get-FileHash C:\Users\Rumyittips\Downloads\Wireshark-win64-3.4.0.exe -Algorithm SHA1
As you are seeing I got the SHA1 value of the exe file, copy this hash value that we need to verify with the hash mentioned on the download page.
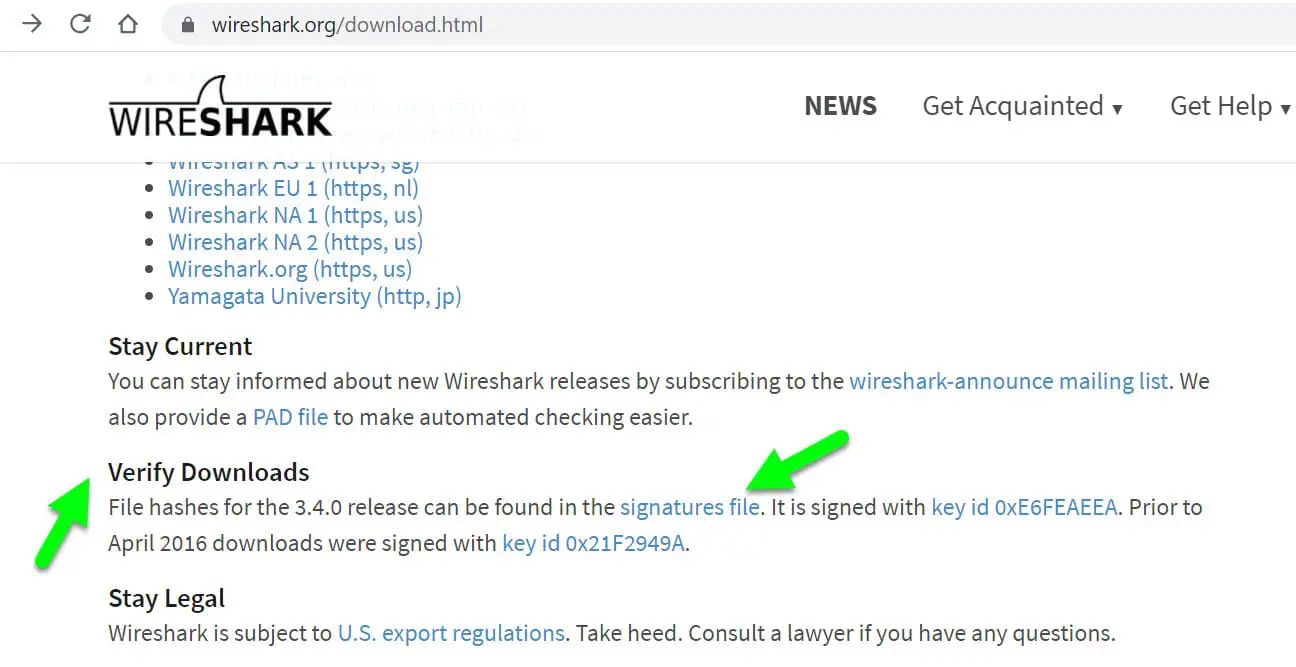
Like in my case, Wireshark is providing the signature file.
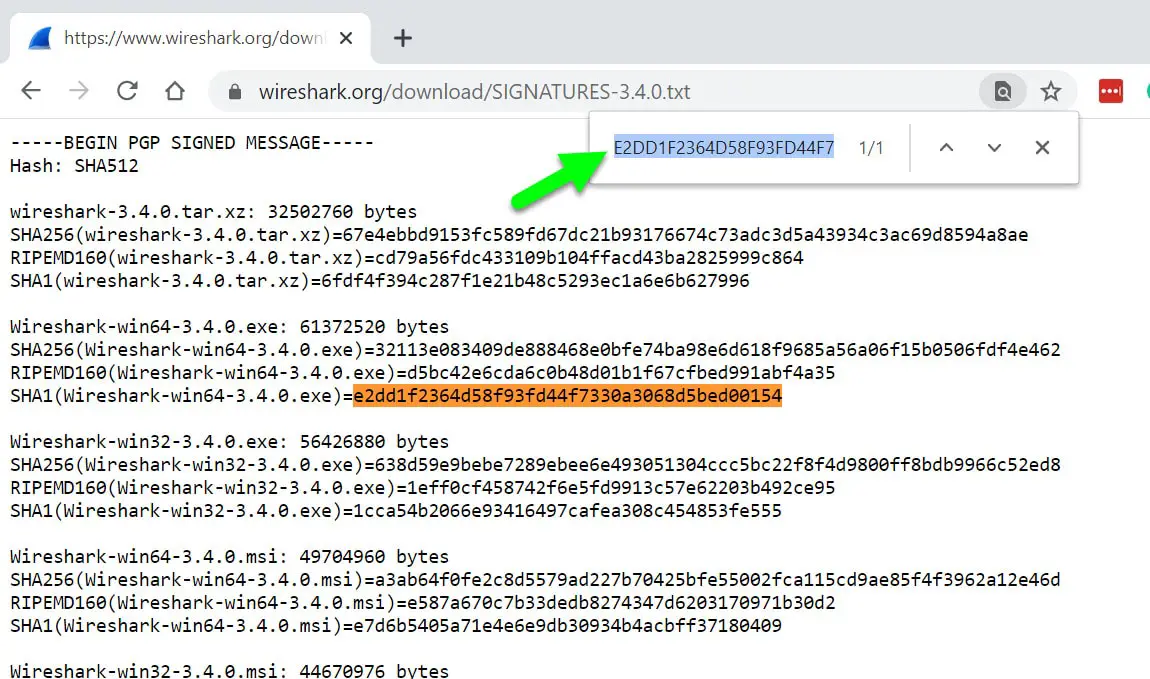
Now just press the Ctrl+F and paste the hash value that you copied from the PowerShell.
As you saw in the below image, my hash is matching with the hash value available on the download page.
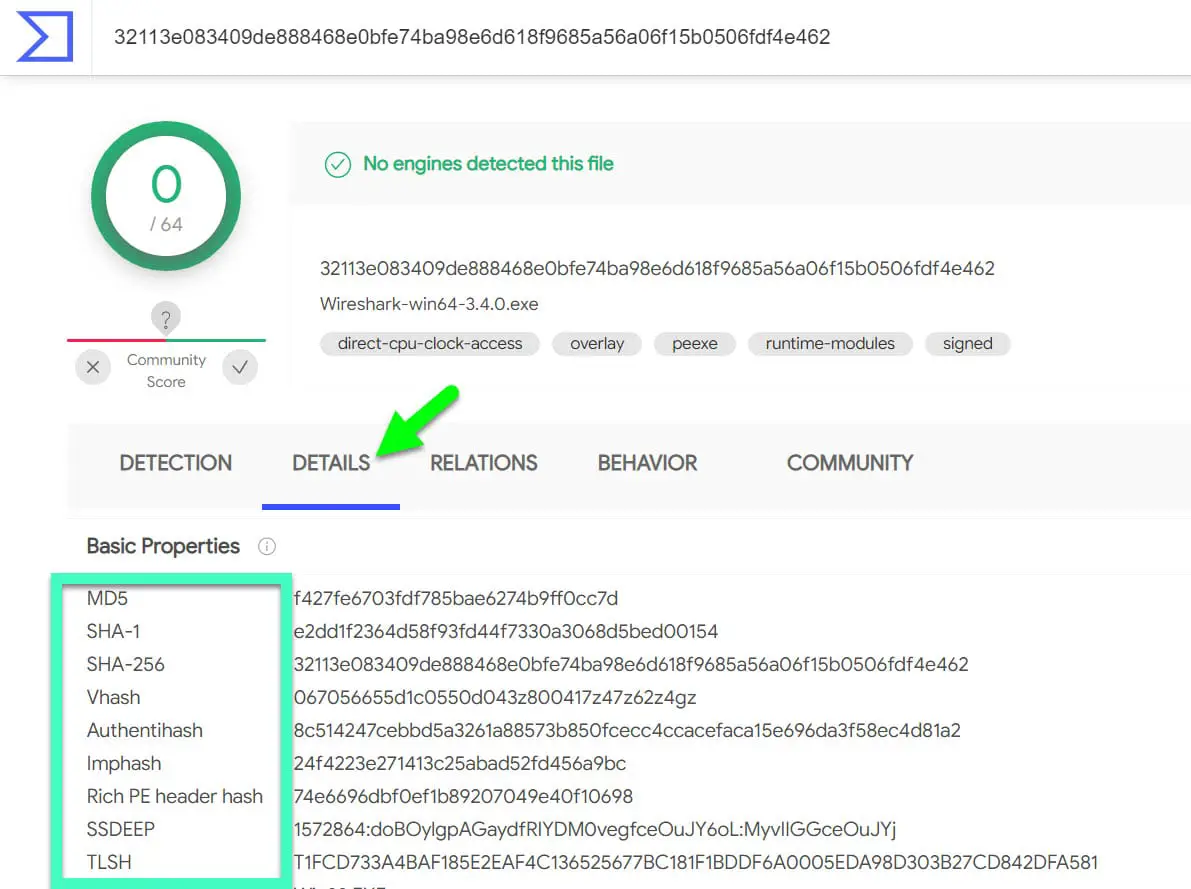
Another best way is to use Virustotal.com, Under the File menu, upload your file.
Click on the Details option, you will get the MD5, SHA-1, and SHA-256 value of your file.
Checksum calculator:-
A checksum calculator is an instrument that is used to calculate the checksum. In the market, there are several options available for checksum calculators but they support different hash functions.
MFCIV is the abbreviation used for Microsoft File Checksum Integrity Verifier, which is one of the best free available calculators for users that only supports MD5 and SHA-1 hash functions yet it is a commonly used, checksum calculator.
IgorWare Hasher is another option working on Windows that supports MD5, SHA-1, and CRC32 and it is not required to be installed. JDigest is also one of the checksum calculators which can function on Windows, Linux, and macOS.
Alternatives of Checksum:-
Like I mentioned above users can select other techniques to check the error that may take place during transmission. A user instead of Checksum can also use Hashbytes to compare the data as well as other options presented.
These options include :
Minimum Distance Coding is best for detecting errors but it can not guarantee any safety against the Preimage attack which basically tries to find the hash value.
Repetition Codes is the type of code in which a bit is repeated several times to get the data transmitted without any error but it is not very effective to secure. It is very simple to handle.
The parity bit is working on the longitudinal redundancy check, transverse redundancy check, and bit grouping techniques.
Cyclic Redundancy Check ( CRC) is another alternative of the Checksum. It is a non-secure hash function that is made to detect any accidental changes made in the data and is good in detecting burst errors but it can not detect any malicious errors so it is not at all secure. It is very easy to implement in the system’s hardware therefore is used widely in the computer network.
Wrap-up:-
In this article, we have seen what a checksum is and its calculator. We have also seen alternatives that you can use instead of using the checksum method. Hopefully, this article has cleared all your doubts.