Imagine working for hours to gather, organize, and send important data only to find out that cybercriminals have intercepted it.
This is a chilling reality in today’s digital world, particularly for organizations relying on outdated or insecure file transfer methods. Many businesses still use standard FTP, oblivious that this method is no longer safe and can expose their data to potential cyber threats.
The consequences can be severe. Businesses risk financial loss and significant damage to their reputation from the violation of confidentiality and integrity of data to non-compliance penalties.
Moreover, data breaches can lead to a catastrophic loss of customer trust. And in the era of GDPR and other stringent data protection regulations, the risk of litigation and heavy fines is more real than ever.
This is where FTPS (File Transfer Protocol Secure) comes into the picture. Unlike standard FTP, FTPS adds an extra layer of security, making it incredibly difficult for unwanted parties to access your sensitive information.
It’s like adding a high-security vault to your data exchange process, ensuring your files remain confidential and arrive at their destination safely.
This article will delve deeper into FTPS, providing a comprehensive understanding of its benefits, how it works, and how you can effectively incorporate it into your data transfer strategies.
Don’t risk your sensitive data anymore – discover how FTPS can offer a safer, more reliable file transfer method.
What is FTPS?🤷♂️
FTP (File Transfer Protocol) has long been a staple for transferring files online. However, FTPS (FTP Secure) is a more secure version of FTP that incorporates the encryption protocols of SSL (Secure Sockets Layer) or TLS (Transport Layer Security).
Unlike standard FTP, which transmits data in clear text, FTPS provides a secure channel for data transmission, protecting sensitive information from unauthorized access. This is especially crucial when transferring sensitive files, such as financial documents or personal data, that require an extra layer of security.
FTPS utilizes a combination of asymmetric and symmetric encryption algorithms to secure the data and establish a secure connection between the client and the server.
The client and server perform a handshake to negotiate encryption settings and authenticate each other’s identity. Once the secure connection is established, data can be transferred securely, preventing eavesdropping or tampering by malicious third parties.
One of the advantages of FTPS is its compatibility with existing FTP clients and servers. Most modern FTP clients support FTPS and can be easily configured on FTP servers by enabling the SSL/TLS encryption options. This means that organizations can enhance the security of their file transfer operations without needing to adopt entirely new software or infrastructure.
FTPS supports two modes of operation: explicit FTPS and implicit FTPS. In explicit FTPS, the client requests a secure connection, typically using a separate port (990) from the standard FTP port (21).
Implicit FTPS, on the other hand, assumes a secure connection from the start and uses a dedicated port (990) for the entire session. The choice between the two modes depends on the specific requirements of the FTPS implementation.
In conclusion, FTPS is a secure extension of FTP that ensures the confidentiality and integrity of data during file transfers. Its compatibility with existing FTP infrastructure makes it popular for organizations seeking to enhance their data security measures.
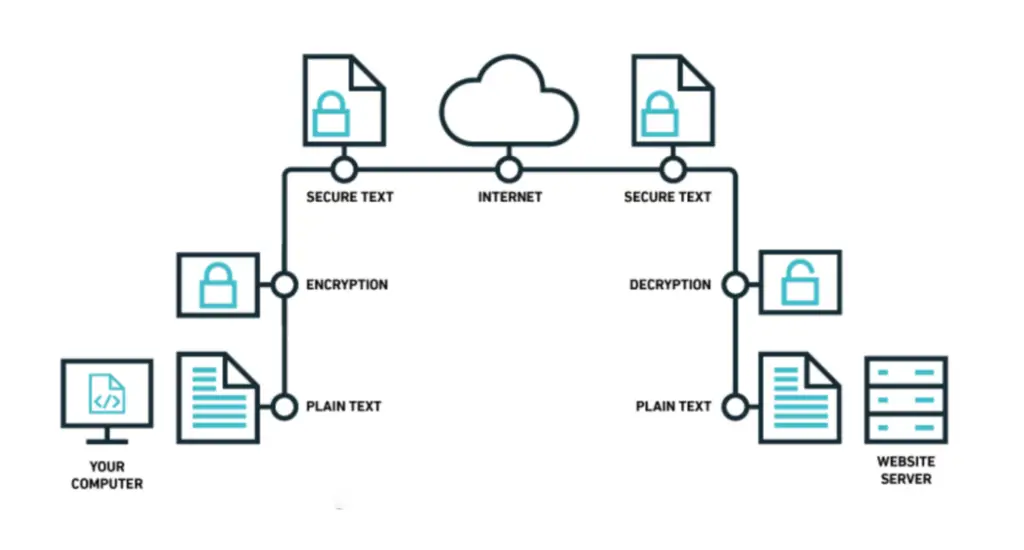
How Does FTPS Work?
In a nutshell, FTPS works by establishing a secure connection between the client and the server, encrypting the data, and ensuring the authenticity of the communication.
This process involves several key steps:-
Step 1:- Establishing a Secure Connection
At the heart of FTPS lies establishing a secure connection between the client and the server. This is achieved by employing SSL/TLS encryption. When a client connects to an FTPS server, it sends a secure connection request. The server responds by presenting its SSL/TLS certificate containing information about its identity and public key.
Step 2:- Authenticating the Server
Before the file transfer can commence, the client verifies the server’s authenticity. It checks the server’s SSL/TLS certificate, ensuring it is valid and issued by a trusted Certificate Authority (CA). This verification process helps prevent man-in-the-middle attacks, where an attacker tries to intercept and manipulate the communication between the client and the server.
Step 3:- User Authentication
Once the server is authenticated, the client needs to authenticate itself to the server. This typically involves providing a username and password combination. Alternatively, more advanced authentication methods like public key authentication can be used, adding an extra layer of security.
Step 4:- Securing the Data Transfer
The data transfer can occur with the secure connection established and both parties authenticated. All data exchanged between the client and the server during this process is encrypted using the negotiated encryption algorithm. This ensures that the data remains unreadable to unauthorized entities even if intercepted.
Step 5:- Data Transfer Modes
FTPS supports two modes for transferring data: passive mode and active mode. In passive mode, the server opens a port and listens for the client to establish a connection.
In active mode, the client opens a port and listens to the server initiate the connection. The mode choice depends on factors such as network configurations and firewall settings.
Step 6:- Handling Firewall and NAT Considerations
Firewalls and network address translation (NAT) can challenge FTPS connections. To address these concerns, FTPS provides options for configuring passive mode to work effectively with firewalls and NAT devices. This involves specifying the range of passive ports and enabling support for NAT.
Step 7:- Closing the Connection
Once the file transfer is complete, it is essential to close the FTPS connection properly. This ensures the release of network resources and maintains the security of the communication channel. The client and server can gracefully terminate the connection, freeing up system resources and ensuring that no unauthorized access can occur after the file transfer.
Setting Up FTPS
Setting up FTPS (FTP Secure) is crucial in establishing a secure file transfer environment. By following the proper configuration process, organizations can ensure the confidentiality and integrity of their data during transmission.
Let’s explore the key steps involved in setting up FTPS.
1. Server Requirements
To set up FTPS, you will need an FTP server that supports SSL/TLS encryption. Ensure the server software you choose has FTPS capabilities and supports the encryption algorithms. Common FTP server software options include FileZilla Server, ProFTPD, and Pure-FTPd.
2. SSL/TLS Certificate Installation
The first step in configuring FTPS is installing an SSL/TLS certificate on the server. Obtain a valid certificate from a trusted Certificate Authority (CA) that matches your server’s domain name. The certificate should be in the PEM (Privacy Enhanced Mail) format. Install the certificate on the FTP server, associating it with the appropriate domain.
3. Configuring FTPS Clients
Next, you must configure the FTPS clients to connect to the server. FTPS clients, such as FileZilla, Cyberduck, or WinSCP, must be set up to use explicit FTPS mode.
This ensures that the client connects to the server securely using SSL/TLS encryption. Configure the client software with the server’s hostname, port number (typically 990 for implicit FTPS or 21 for explicit FTPS), and user credentials for authentication.
4. Passive and Active Mode Configuration
FTPS supports both passive mode and active mode for data transfer. Passive mode is generally recommended as it is more compatible with firewalls and NAT devices.
In passive mode, the server listens on a specified range of passive ports, and the client initiates the connection. Active mode requires the client to listen on a specific port, which can be challenging due to firewall restrictions.
5. Firewall and NAT Considerations
Firewalls and network address translation (NAT) devices can impact FTPS connections. Configure your network devices to allow incoming and outgoing FTPS traffic on the appropriate ports. Enable port forwarding or configure NAT rules to redirect FTPS traffic to the FTP server. This ensures that FTPS connections can be established successfully.
6. User Permissions and Access Controls
Proper user permissions and access controls are essential for FTPS security. Set up user accounts on the FTP server, assigning each user the appropriate permissions and access rights. Consider implementing strong password policies and, if possible, enable multi-factor authentication (MFA) for added security.
7. Testing and Troubleshooting
After the initial setup, it’s crucial to test the FTPS connection to ensure it is functioning correctly. Verify that the server accepts connections and that data can be transferred securely. Perform both uploads and downloads to validate the integrity of the file transfers. If any issues arise, consult the server and client software documentation or seek support from the software’s community.
8. Regular Maintenance and Updates
Once FTPS is set up successfully, regular maintenance is essential to keep the environment secure. Stay updated with the latest security patches and updates for both the server software and client applications.
Regularly review user accounts, remove inactive accounts, and enforce strong password policies. Perform periodic security audits to identify and address any vulnerabilities.
In conclusion, setting up FTPS involves configuring the FTP server with SSL/TLS certificates, setting up FTPS clients, managing passive and active mode configurations, addressing firewall and NAT considerations, implementing user permissions and access controls, testing the connection, and maintaining the environment through regular updates and maintenance.
Following these steps, organizations can establish a secure FTPS environment, protecting sensitive data during file transfers.
FTPS Security Considerations
Regarding secure file transfer, FTPS (FTP Secure) is a popular choice incorporating SSL/TLS encryption to protect data during transmission.

1. SSL/TLS Certificate Management
FTPS relies on SSL/TLS certificates to establish secure connections. It’s crucial to manage these certificates effectively to prevent unauthorized access. Regularly renewing and updating certificates is essential to maintain a secure environment. Additionally, ensure certificates are issued by trusted Certificate Authorities (CAs) and use strong encryption algorithms.
2. Choosing Strong Encryption Algorithms
The choice of encryption algorithms plays a vital role in the security of FTPS. It is recommended to use modern and secure algorithms such as AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman) for robust data protection. Avoid weaker algorithms that may be susceptible to attacks.
3. User Authentication Best Practices
To ensure secure access to FTPS servers, follow user authentication best practices. Enforce strong passwords and consider implementing multi-factor authentication (MFA) for added security. Regularly review user accounts and remove any unnecessary or inactive accounts to minimize the risk of unauthorized access.
4. Handling Firewall and Proxy Issues
Firewalls and proxies are common network infrastructure components that can impact FTPS connections. Configuring firewalls and proxies is important to allow FTPS traffic and enable the passive mode if necessary. Properly configuring network devices ensures smooth FTPS operations and prevents connection issues.
5. Regular Security Audits and Updates
Regular security audits of FTPS servers and client systems are essential to identify and address vulnerabilities. Stay updated with security patches and updates for FTPS software and operating systems. By promptly applying patches, you can protect against known security vulnerabilities and minimize the risk of exploitation.
6. Secure Data Storage
While FTPS ensures data security during transmission, it’s equally important to consider it data at rest. Ensure that files stored on FTPS servers are encrypted and protected against unauthorized access. Utilize secure storage practices, such as disk encryption and access controls, to safeguard sensitive data.
7. Monitoring and Logging for Security Incidents
Implement robust monitoring and logging mechanisms to promptly detect and respond to security incidents. Monitor FTPS server logs for suspicious activities and unauthorized access attempts. Establish real-time alerts for potential security breaches, ensuring quick mitigation of any threats.
8. Compliance with Regulatory Standards
Many industries have specific compliance requirements for data protection and secure file transfers. Ensure your FTPS implementation aligns with relevant regulatory standards such as PCI DSS (Payment Card Industry Data Security Standard) or HIPAA (Health Insurance Portability and Accountability Act). Complying with these regulations helps maintain data privacy and customer trust.
In conclusion, FTPS provides a secure file transfer solution by leveraging SSL/TLS encryption. To maximize the security of your FTPS implementation, consider the security considerations outlined above.
By effectively managing SSL/TLS certificates, choosing strong encryption algorithms, implementing user authentication best practices, addressing firewall and proxy issues, conducting regular security audits, ensuring secure data storage, monitoring for security incidents, and complying with regulatory standards, you can establish a robust and secure FTPS environment.
By taking these steps, you can protect sensitive data, maintain data integrity, and mitigate the risk of unauthorized access during FTPS file transfers.
Advantages of FTPS
File Transfer Protocol Secure (FTPS) is a secure file transfer protocol that combines the familiarity of FTP with the security features of SSL/TLS encryption. FTPS offers several advantages, making it a preferred choice for organizations requiring secure and reliable file transfers.
Let’s explore the advantages of FTPS in detail.
1. Enhanced Security and Data Protection
One of the significant advantages of FTPS is its enhanced security. By utilizing SSL/TLS encryption, FTPS ensures that data is transmitted securely over the network.
This encryption provides confidentiality by encrypting the data, making it inaccessible to unauthorized users. Additionally, FTPS ensures data integrity by preventing tampering or unauthorized modification of files during transmission.
2. Compliance with Regulatory Standards
FTPS facilitates compliance with various regulatory standards and industry requirements. Organizations operating in regulated industries such as healthcare, finance, or e-commerce often must adhere to stringent security and privacy regulations.
FTPS, with its strong encryption and data protection capabilities, helps organizations meet the requirements of standards like HIPAA, PCI DSS, and GDPR.
3. Compatibility with Existing Infrastructure
Another advantage of FTPS is its compatibility with existing infrastructure. Since FTPS is built upon the FTP protocol, it can seamlessly integrate into existing FTP server environments without requiring significant changes or additional investments.
This compatibility allows organizations to enhance the security of their file transfers without disrupting their established workflows.
4. Authentication and Access Control
FTPS provides robust authentication and access control mechanisms. Users connecting to an FTPS server are required to authenticate themselves, typically by providing a username and password combination.
This ensures that only authorized individuals can access and transfer files. Additionally, FTPS allows organizations to define access permissions and restrictions for specific users or user groups, providing granular control over file access.
5. Versatility and Flexibility
FTPS offers versatility and flexibility in terms of configuration options. It supports both passive and active modes for data transfer, allowing organizations to choose the mode that suits their specific network requirements.
FTPS can operate over standard FTP ports (explicit FTPS) or dedicated ports (implicit FTPS), providing flexibility in network configurations and enabling easy integration into the existing firewall and NAT settings.
6. Broad Client Support
FTPS enjoys broad client support, making it accessible across various platforms and operating systems. Popular FTP client applications such as FileZilla, Cyberduck, and WinSCP support FTPS as a standard protocol. This wide client support ensures users have various options when selecting an FTP client, enabling seamless and secure file transfers.
7. Scalability and Performance Considerations
FTPS offers scalability and performance advantages for organizations with growing file transfer needs. It supports concurrent file transfers, allowing multiple users to transfer files simultaneously. Additionally, FTPS implements optimized compression techniques, minimizing the overhead associated with encryption and ensuring efficient and fast data transfers.
8. Mitigation of Network Risks
By utilizing FTPS, organizations can mitigate network risks associated with unsecured file transfers. The SSL/TLS encryption employed by FTPS protects data from interception and unauthorized access, safeguarding it from potential network vulnerabilities.
Also addresses security concerns related to clear-text FTP passwords, reducing the risk of credential theft or unauthorized access. In conclusion, FTPS offers significant advantages for organizations seeking secure and reliable file transfers.
Types of FTPS
File Transfer Protocol Secure (FTPS) is a widely used secure file transfer protocol that combines the reliability and familiarity of FTP with the security of SSL/TLS encryption. FTPS has evolved, and different types have emerged to meet various security requirements.
Let’s explore the types of FTPS and their unique characteristics.
1. Explicit FTPS (FTPES)
Explicit FTPS, also known as FTPES, is the most common type of FTPS. It provides an added layer of security by initiating an explicit SSL/TLS session upon command.
With explicit FTPS, the client requests a secure connection from the server using the “AUTH TLS” or “AUTH SSL” command. This type of FTPS is compatible with most firewalls and network configurations.
2. Implicit FTPS
Implicit FTPS, sometimes called FTPIS, takes a different approach than explicit FTPS. In implicit FTPS, the SSL/TLS session is established automatically when the client connects to the server on the default FTPS port, typically port 990.
This means that the entire FTPS session is encrypted from the beginning without any explicit command from the client. Implicit FTPS is commonly used in legacy systems and may require additional configuration on firewalls and routers.
3. FTPS over SSH
FTPS over SSH, also known as FTP-SSH or SFTP, is a distinct type of secure file transfer protocol that should not be confused with FTPS. While FTPS uses SSL/TLS encryption, FTPS over SSH utilizes the SSH (Secure Shell) protocol for secure file transfers.
FTPS over SSH operates on port 22 and provides secure file transfer capabilities within the SSH session. It offers a higher level of security and is commonly used in UNIX-based systems.
4. FTPS with Client Certificates
In addition to username and password authentication, FTPS also supports client certificate-based authentication. With this type of FTPS, the client presents a digital certificate to the server to establish identity verification.
Client certificate authentication adds an extra layer of security, ensuring that only clients with valid certificates can access the FTPS server. This type of FTPS is commonly used in environments requiring strong authentication measures, such as corporate settings or financial institutions.
5. FIPS-compliant FTPS
FTPS can also be implemented in a FIPS (Federal Information Processing Standard) compliant manner. FIPS-compliant FTPS adheres to the security standards set by the U.S. government.
It utilizes FIPS 140-2 validated cryptographic modules, ensuring that the encryption algorithms and security mechanisms meet the strict requirements of government agencies and industries that require FIPS compliance.
6. FTPS with Extended Validation (EV) Certificates
FTPS can leverage Extended Validation (EV) certificates to enhance trust and security. EV certificates provide an added layer of assurance by validating the server’s identity through a rigorous verification process.
When connecting to an FTPS server with an EV certificate, the client’s web browser displays a green address bar, indicating the highest level of security and assurance.
7. Virtual FTPS (vFTPS)
Virtual FTPS, or vFTPS, is a cloud-based implementation of FTPS that allows organizations to leverage the benefits of FTPS without the need for dedicated hardware or on-premises infrastructure.
With vFTPS, organizations can transfer files securely over the internet using FTPS, eliminating the need for managing and maintaining physical servers. In conclusion, FTPS offers various types to cater to security requirements and preferences.
Whether it’s the widely used explicit FTPS, the automatic encryption of implicit FTPS, the SSH-based FTPS over SSH, client certificate-based authentication, FIPS-compliant FTPS, EV certificates for added trust, or the cloud-based vFTPS, organizations can choose the type of FTPS that aligns with their specific security needs.
By selecting the appropriate type of FTPS, businesses can ensure secure file transfers and protect the confidentiality and integrity of their valuable data.
Here’s a chart comparing Explicit FTPS and Implicit FTPS:-
| Criteria | Explicit FTPS | Implicit FTPS |
|---|---|---|
| Encryption | SSL/TLS | SSL/TLS |
| Connection Method | Client-initiated | Server-initiated |
| Port | 21 | 990 |
| Data Channel Port | Negotiated | 989 (fixed) |
| Firewall Support | Requires explicit rule for data channel port range | Requires an implicit rule for data channel port range |
| Compatibility | Compatible with most modern FTP clients | Compatible with fewer FTP clients |
Limitations and Challenges of FTPS
File Transfer Protocol Secure (FTPS) is a popular, secure file transfer protocol that combines the reliability of FTP with the security of SSL/TLS encryption. While FTPS offers robust security features, it also has certain limitations and challenges that users should know.
Let’s explore the limitations and challenges of FTPS in detail.
1. Complexity of Configuration
Setting up and configuring FTPS can be more complex than other file transfer protocols. It requires installing SSL/TLS certificates, configuring encryption algorithms, managing user authentication, and addressing firewall and NAT traversal challenges. This complexity may require technical expertise and time investment for proper implementation.
2. Potential Compatibility Issues
FTPS may encounter compatibility issues with certain FTP clients and servers. Some older or less common FTP clients or servers may not support FTPS or may have limited support for certain FTPS features. This can pose challenges when establishing secure connections between different FTPS implementations.
3. Firewall and NAT Traversal Challenges
Firewalls and network address translation (NAT) devices can present challenges for FTPS connections. FTPS uses separate control and data connections, and passive or active mode can impact firewall configurations. In some cases, configuring firewalls and NAT devices to allow FTPS connections may require additional network infrastructure adjustments.
4. Maintenance and Certificate Renewal
FTPS requires regular maintenance and certificate renewal to ensure continued security. SSL/TLS certificates have expiration dates and must be renewed periodically.
Failing to renew certificates promptly can lead to disruptions in FTPS operations and potential security vulnerabilities. Certificate management and renewal processes should be carefully planned and monitored.
5. Performance Considerations
The additional overhead introduced by SSL/TLS encryption in FTPS can impact performance compared to non-encrypted file transfer protocols. Encryption and encryption require additional computational resources, leading to slower file transfer speeds, especially when handling large files or high volumes of data. Organizations should consider performance implications when implementing FTPS.
6. Limited Scalability
FTPS may have limited scalability compared to other file transfer protocols. The overhead associated with SSL/TLS encryption and managing secure connections can impact the ability to handle many concurrent file transfers.
Organizations with high-volume file transfer needs may need to consider alternative solutions or implement additional infrastructure to scale effectively.
7. Certificate Trust and Management
FTPS relies on SSL/TLS certificates for secure communication. The trust of these certificates is crucial for establishing secure connections. Organizations must ensure that SSL/TLS certificates are obtained from trusted Certificate Authorities (CAs) and properly managed. Failure to handle certificates securely can result in trust issues and potential security breaches.
8. Complexity of Key Management
FTPS requires proper key management for encryption and authentication purposes. Organizations must securely generate, store, and manage the cryptographic keys used in SSL/TLS encryption.
Key management practices include protecting private keys, rotating keys periodically, and ensuring the integrity of key storage systems. Proper key management can add complexity to the FTPS implementation.
In conclusion, while FTPS offers secure file transfer capabilities, it has certain limitations and challenges that organizations should consider.
These include the complexity of configuration, potential compatibility issues, firewall and NAT traversal challenges, maintenance and certificate renewal requirements, performance considerations, limited scalability, certificate trust and management, and key management complexity.
Despite these challenges, many organizations use FTPS successfully by implementing proper planning, configuration, and ongoing maintenance to ensure secure and reliable file transfers.
FTPS vs. Other Secure File Transfer Protocols
FTPS vs SFTP: Key Differences and Use Cases
Regarding secure file transfer protocols, two popular options that often come up in discussions are FTPS and SFTP. While both provide secure file transfer capabilities, they have significant differences in their underlying technology and use cases.
Let’s explore the key differences and use cases of FTPS and SFTP.
1. Security Mechanism
The primary difference between FTPS and SFTP lies in their security mechanisms. FTPS, as File Transfer Protocol Secure, uses SSL/TLS (Secure Sockets Layer/Transport Layer Security) encryption to secure data during transmission.
On the other hand, SFTP, or SSH File Transfer Protocol, relies on the SSH (Secure Shell) protocol for secure file transfers. SFTP encrypts both data and commands, providing end-to-end encryption.
2. Port Usage
FTPS and SFTP also differ in their port usage. FTPS typically uses port 21 for control commands and an additional port, often port 990, for secure SSL/TLS connections.
In contrast, SFTP uses port 22, the default SSH port, for control and data transmission. This can simplify network configurations as there’s no need to open additional ports for secure connections.
3. Firewall and NAT Traversal
Regarding firewall and NAT traversal, FTPS can present challenges due to its use of separate control and data connections, especially in passive mode.
FTPS requires additional configuration on firewalls and NAT devices to allow incoming connections on the dynamically assigned ports. SFTP, on the other hand, operates within an SSH session over a single port, making traversing firewalls and NAT devices easier.
4. Authentication Mechanisms
Authentication mechanisms also differ between FTPS and SFTP. FTPS supports various authentication methods, including username/password combinations and client certificates.
SFTP primarily relies on SSH key-based authentication, offering more robust security through public key cryptography. This makes SFTP suitable for environments requiring stronger authentication measures.
5. Platform Support
Regarding platform support, FTPS enjoys broader compatibility across different operating systems and platforms. It is supported by most FTP client applications and servers, making it more accessible for users.
SFTP, an extension of the SSH protocol, is primarily supported on UNIX-based systems. However, SFTP client and server implementations are available for major operating systems.
6. Use Cases
The choice between FTPS and SFTP depends on specific use cases and security requirements. FTPS is often preferred when there is a need to integrate secure file transfers into existing FTP infrastructure.
It provides backward compatibility with FTP, making it suitable for organizations transitioning from traditional FTP to a more secure solution. FTPS is also useful when compatibility with legacy systems or specific FTP client applications is required.
SFTP, on the other hand, is commonly used in UNIX-based environments where SSH is already implemented. It is ideal for strong security and authentication scenarios, such as transferring sensitive data or complying with regulatory standards.
SFTP’s ability to encrypt data and commands and its robust SSH key-based authentication makes it a preferred choice for secure file transfers.
Conclusion: FTPS and SFTP offer secure file transfer capabilities with distinct features and use cases. FTPS utilizes SSL/TLS encryption, operates on separate control and data ports, supports various authentication methods, and enjoys broader platform support.
SFTP relies on the SSH protocol, operates over a single port, primarily uses SSH key-based authentication, and is commonly implemented in UNIX-based systems.
When choosing between FTPS and SFTP, consider factors such as security requirements, firewall and NAT configurations, platform compatibility, and the need for backward compatibility with existing FTP infrastructure.
Organizations can select the appropriate protocol to ensure secure and efficient file transfers by understanding the key differences and assessing specific use cases.
FTPS vs HTTPS: Choosing the Right Protocol
Regarding secure data transmission, two protocols often come to mind: FTPS (File Transfer Protocol Secure) and HTTPS (Hypertext Transfer Protocol Secure).
Both protocols offer encryption to protect data during transmission but have different features and use cases. Choosing the right protocol depends on various factors.
Let’s compare FTPS vs HTTPS and explore how to make an informed decision.
1. Security Mechanisms
FTPS and HTTPS employ different security mechanisms. FTPS utilizes SSL/TLS encryption to secure file transfers. It establishes a secure channel between the client and server, encrypting data and commands.
On the other hand, HTTPS is an extension of HTTP that uses SSL/TLS to encrypt web communications, ensuring the confidentiality and integrity of data exchanged between a web server and a client.
2. Use Cases
The choice between FTPS and HTTPS depends on the specific use cases and requirements. FTPS is commonly used for secure file transfers, particularly in scenarios where large files or batch transfers are involved.
It is well-suited for organizations that must transfer files between servers or exchange files with clients. In contrast, HTTPS is primarily used for secure web communication, such as securing online transactions, protecting user information on websites, or securing web APIs.
3. Port and Protocol Differences
FTPS and HTTPS also differ in their ports and protocols. FTPS typically operates on ports 21 and 990. Port 21 is used for control commands, while port 990 is used for secure SSL/TLS connections.
On the other hand, HTTPS operates on port 443 by default, using the HTTP protocol over an encrypted SSL/TLS connection. The use of different ports can impact network configurations and firewall settings.
4. Authentication
Authentication mechanisms differ between FTPS and HTTPS. FTPS supports various authentication methods, including username/password combinations and client certificates.
HTTPS, however, primarily relies on digital certificates issued by trusted Certificate Authorities (CAs). HTTPS ensures server authenticity and verifies the identity of the website or web server to establish a secure connection.
5. Platform and Browser Support
FTPS and HTTPS enjoy platform and browser support to varying degrees. FTPS has broader support across different operating systems and FTP client applications.
It is widely supported by FTP clients and servers, making it accessible. On the other hand, HTTPS is supported by all major web browsers and is considered the standard protocol for secure web communication.
6. Ease of Implementation
Implementing FTPS and HTTPS also differs in terms of ease of implementation. FTPS requires setting up and configuring an FTP server and client with SSL/TLS certificates, encryption algorithms, and user authentication.
HTTPS, however, requires obtaining and installing an SSL/TLS certificate on the web server. HTTPS may be easier for websites as it leverages existing web server infrastructure.
7. Regulatory Compliance
Regulatory compliance requirements can influence the choice between FTPS and HTTPS. Certain industries, such as finance and healthcare, have specific regulations and standards for data protection during transmission.
FTPS and HTTPS can both address compliance requirements. Still, organizations must ensure they choose the protocol that aligns with their specific industry regulations, such as PCI DSS for payment card data security or HIPAA for healthcare data protection.
8. Consideration of Network Environment
When deciding between FTPS and HTTPS, it’s important to consider the network environment and any limitations or restrictions that may impact the protocol’s performance.
Some networks may have stricter firewall rules or proxies that affect FTPS connections. HTTPS may be a more viable option in such cases as it typically bypasses these limitations since it operates on the standard HTTP port.
In conclusion, choosing between FTPS and HTTPS depends on several factors, including use cases, security requirements, ease of implementation, regulatory compliance, and network environment.
FTPS is suitable for secure file transfers, while HTTPS is commonly used for secure web communication. Carefully assess your specific needs and consider the strengths and limitations of each protocol to make an informed decision.
By choosing the right protocol, you can ensure the secure data transmission by your requirements.
Best Practices for FTPS Implementation
Implementing File Transfer Protocol Secure (FTPS) requires careful planning and adherence to best practices to ensure a secure and reliable file transfer environment.
By following industry best practices, organizations can mitigate risks, enhance data security, and optimize the performance of their FTPS implementation.
Let’s explore the best practices for FTPS implementation in more detail.
1. Use Strong SSL/TLS Encryption
One of the key best practices for FTPS implementation is to use strong SSL/TLS encryption algorithms. Select widely recognized and secure encryption algorithms, such as AES (Advanced Encryption Standard), for securing data transfers.
Ensure that your FTPS server and client are configured to use the latest versions of SSL/TLS protocols and prefer secure cipher suites.
2. Secure Certificate Management
Effective certificate management is crucial for a secure FTPS implementation. Obtain SSL/TLS certificates from trusted Certificate Authorities (CAs) and regularly monitor their validity.
Implement a robust certificate management process that includes certificate renewal, proper storage of private keys, and the use of certificates signed with strong hashing algorithms.
3. Enforce Strong Authentication
Enforce strong authentication measures for FTPS connections to enhance security. Utilize secure authentication methods, such as username/password combinations, two-factor authentication (2FA), or public key authentication.
Consider implementing password policies that enforce complex passwords and regular password changes to protect user credentials.
4. Implement Access Controls and User Permissions
Maintain control over FTPS operations by implementing access controls and user permissions. Assign users appropriate access rights and permissions based on the least privilege principle. Review and audit user accounts regularly to ensure only authorized individuals can access sensitive data.
5. Harden the FTPS Server
Apply security hardening practices to the FTPS server to minimize vulnerabilities. Disable unnecessary services and features, close unused ports, and update the server software with the latest security patches. Regularly monitor the server logs for any suspicious activities or unauthorized access attempts.
6. Enable Logging and Monitoring
Enable logging and monitoring capabilities to maintain visibility into FTPS activities. Configure detailed logging to record FTPS sessions, user activities, and file transfers.
Regularly review the logs to identify any anomalies or potential security breaches. Implement real-time monitoring to detect and respond to any unauthorized access attempts promptly.
7. Implement Network Segmentation
To enhance security, consider implementing network segmentation by isolating the FTPS server from other critical systems. This helps minimize the impact of a potential breach by containing it within a separate network segment.
Use firewalls and network segmentation techniques to restrict access to the FTPS server and allow only authorized connections.
8. Regularly Update and Patch
Stay vigilant about regularly updating and patching your FTPS server and client software. Keep track of security advisories and updates released by the software vendors.
Promptly apply patches and updates to address security vulnerabilities and ensure the latest security features are in place.
9. Perform Security Audits and Testing
Regularly conduct security audits and testing to evaluate the effectiveness of your FTPS implementation. Perform penetration testing and vulnerability assessments to identify potential weaknesses.
Conduct regular security audits to assess compliance with industry standards and regulatory requirements.
10. Educate Users and Implement Training
Educate users and provide training on secure FTPS practices. Ensure that users understand the importance of secure password management, file transfer best practices, and the potential risks of improper FTPS usage.
Regularly remind users about security policies and promote a culture of security awareness.
In conclusion, implementing FTPS following best practices is essential to establish a secure and reliable file transfer environment.
By utilizing strong SSL/TLS encryption, securing certificate management, enforcing strong authentication, implementing access controls, hardening the FTPS server, enabling logging and monitoring, implementing network segmentation, regularly updating and patching, performing security audits and testing, and educating users, organizations can mitigate risks and maintain the confidentiality and integrity of their data during FTPS transfers.
📗FAQ’s
What is the difference between SFTP and FTPS?
SFTP (Secure File Transfer Protocol) is a network protocol that uses SSH (Secure Shell) for secure file transfer. It encrypts both the data and commands being transmitted over the network.
FTPS (File Transfer Protocol Secure) is an extension of FTP that adds SSL/TLS (Secure Sockets Layer/Transport Layer Security) encryption for secure file transfer.
Here’s a chart that outlines the main differences between SFTP and FTPS:-
| Criteria | SFTP | FTPS |
|---|---|---|
| Protocol | SSH File Transfer Protocol | File Transfer Protocol over SSL/TLS |
| Port | 22 | 989 (implicit) or 21 (explicit) |
| Security | End-to-end encryption, authentication, and integrity protection | Encrypted authentication and data transfer, integrity protection |
| Certificate | No need for a separate certificate | A separate SSL/TLS certificate is needed |
| Firewall | Can be used with firewalls | May require additional configuration for firewalls |
| Client software | Requires a dedicated SFTP client | Can be used with standard FTP clients with SSL/TLS support |
| Platform | Cross-platform | Primarily for Windows, but also available on Unix-based systems |
| Compatibility | Compatible with most operating systems | Some FTP clients may not support FTPS |
| Performance | Slower than FTPS | Faster than SFTP |
| Mode of operation | Session-oriented | Connection-oriented |
| Compliance | Compliant with HIPAA, PCI DSS, and other regulatory requirements | Compliant with HIPAA, PCI DSS, and other regulatory requirements |
Secure File Transfer Protocol (SFTP) and File Transfer Protocol Secure (FTPS) are both safe ways to send files over the internet, but they are not interchangeable. When it comes to security, SFTP employs SSH while FTPS makes use of SSL/TLS.
SFTP works on any OS, while FTPS is designed for Windows but is also supported by Unix-based systems. HIPAA and PCI DSS are two examples of regulations that both methods meet.
Is FTPS still used?
Yes, FTPS is still used today as a secure method of transferring files over the internet.
What is the difference between FTP and FTPS?
FTP (File Transfer Protocol) is a network protocol used to transfer files between a client and a server. FTPS, on the other hand, is a secure extension of FTP that adds SSL/TLS encryption to protect data being transmitted over the network.
Which is better SFTP or FTPS?
SFTP is generally considered more secure than FTPS, as it encrypts both the data and commands being transmitted, whereas FTPS only encrypts the data.
Why use FTPS instead of SFTP?
FTPS is sometimes preferred over SFTP because it uses the standard FTP protocol, making it easier to integrate into existing systems. Additionally, some servers may not support SFTP.
Which is faster FTPS or SFTP?
Neither FTPS nor SFTP is inherently faster than the other, as transfer speeds largely depend on the network conditions and server performance.
What are the risks of FTPS?
The risks associated with FTPS include potential attacks on the SSL/TLS encryption, as well as vulnerabilities in the FTP protocol itself.
Is FTPS considered secure?
FTPS is generally considered secure, as it uses SSL/TLS encryption to protect data being transmitted over the network.
What port does FTPS require?
FTPS typically uses port 990 for control messages and port 989 for data transmission.
Does FTPS require SSL?
Yes, FTPS requires SSL/TLS encryption to secure data transmitted over the network.
Is FTPS HIPAA compliant?
Yes, FTPS can be HIPAA compliant using appropriate security measures such as encryption, access controls, and audit trails.
Why is SFTP not secure?
SFTP is generally considered secure, but it can be vulnerable to attacks on the SSH protocol if the server is not properly configured.
What port does SFTP use for FTPS?
SFTP typically uses port 22 for both control messages and data transmission.
Which SFTP is most secure?
The security of an SFTP implementation largely depends on the strength of the encryption used, the security of the underlying SSH protocol, and proper server configuration.
Why is SFTP better?
SFTP is considered better than standard FTP because it encrypts both the data and transmitted commands, providing a higher level of security.
How do I connect to FTPS?
To connect to an FTPS server, you must use an FTP client that supports SSL/TLS encryption. You will also need to enter the server’s hostname or IP address, port number, and your login credentials.
How does FTPS authentication work?
FTPS authentication typically involves using a username and password credentials, which are transmitted over the network in an encrypted form using SSL/TLS encryption.
Does anyone still use SFTP?
Yes, SFTP is still widely used as a secure method of transferring files over the internet.
Is HTTPS more secure than SFTP?
HTTPS (Hypertext Transfer Protocol Secure) and SFTP are two different protocols that serve different purposes. HTTPS is used for secure web browsing, while SFTP is used for secure file transfer. Both protocols use encryption to protect data being transmitted over the network.
What is better than SFTP?
There are several secure file transfer protocols that are considered better than SFTP, including SCP (Secure Copy), which is similar to SFTP but uses the SSH protocol for authentication and encryption, and WebDAV (Web Distributed Authoring and Versioning), which provides secure file transfer capabilities over HTTP.
Can SFTP use port 443?
SFTP typically uses port 22 for both control messages and data transmission, but it can be configured to use other ports as well, including port 443.
What is implicit FTPS?
Implicit FTPS is a variant of FTPS that uses SSL/TLS encryption from the beginning of the connection, without requiring an explicit command from the client to start encryption.
Does SFTP use TLS or SSL?
SFTP does not use SSL (Secure Sockets Layer), but it does use the related protocol, TLS (Transport Layer Security), for encryption and authentication.
Is SFTP SSL or TLS?
SFTP uses TLS (Transport Layer Security) for encryption and authentication, not SSL (Secure Sockets Layer).
How does SFTP work for dummies?
SFTP establishes a secure connection between a client and server using the SSH (Secure Shell) protocol. The client can then use commands to upload, download, or manipulate files on the server, all while the transmitted data is encrypted for security.
Why do banks use SFTP?
Banks use SFTP as a secure method of transferring financial data and other sensitive information between internal systems and external partners or customers.
Does SFTP need a server?
Yes, SFTP requires a server to establish a secure connection between a client and the remote system.
How do I access my FTPS from my browser?
To access an FTPS server from a web browser, you must use a browser that supports FTPS and SSL/TLS encryption. You can then enter the server’s hostname or IP address, port number, and your login credentials to access the server.
How do I open FTPS in Chrome?
To open FTPS in Chrome, you can use a Chrome extension such as “FTP Extension for Chrome” or “Secure FTP Client for Google Chrome,” which provide FTPS support within the browser.
How do I connect to FTPS in Windows?
To connect to an FTPS server in Windows, you can use the built-in “FTP Client” application, which supports FTPS and SSL/TLS encryption. You can then enter the server’s hostname or IP address, port number, and your login credentials to access the server.
Conclusion
In conclusion, FTPS is not just a secure choice – it’s an essential step in securing your file transfers in an increasingly cyber-threatened world.
By using FTPS, you add a robust layer of security to your data and ensure compliance with data protection regulations.
You no longer have to worry about the integrity and confidentiality of your data being compromised nor face the daunting repercussions of a potential data breach.
Embracing FTPS is about future-proofing your business, safeguarding your reputation, and instilling a deeper trust with your stakeholders. By understanding and implementing FTPS as detailed in this article, you will take a substantial stride towards a safer and more secure digital business environment.
Remember, in data exchange, it’s not just about transferring files – it’s about transferring them safely, and FTPS is the key to achieving this. Equip your business with FTPS today and experience the peace of mind with secure file transfer.