Mac users still face cyber threats even as Apple continues to speed up efforts to ensure their devices are safe and secure. In 2022, it was reported that macOS had the fewest malware infections—a clear indication of macOS’s superiority over other operating systems.
Apple’s macOS is said to suffer malware or virus attacks rarely. It’s less vulnerable than Windows, all thanks to the frequent release of system updates to resolve lingering vulnerabilities. However, this doesn’t mean Mac users aren’t potential cyberattack victims.
Criminals can still bypass your device’s strong defenses and launch malware attacks. You may not see it coming because malware on Mac has evolved enough to evade most of the standard detection methods.
In this article, we will look at malware on Mac, its impact, and how to detect, remove, and prevent your Mac from getting it. Read on!
How vulnerable are Macs to malware attacks?
Can my Mac get malware? This is a common question most Mac users grapple with when faced with the uncertainty of their device’s security.
Your Mac is no exception when it comes to malware attacks. Like any other unprotected device, it’s vulnerable to malware and hackers. The worst part is that an infection that looks harmless can seriously risk your Mac hardware and private data.
There are many ways malware can attack your Mac. Let’s take a look at a few:
Downloading software and files
Downloading files from untrusted sources is the easiest way to expose your device to malware. Any content from the internet that’s not from a reputable source is a potential avenue for malware and other types of viruses.
Remote Desktop Protocol (RDP)
Remote Desktop Protocol allows criminals to connect to your device remotely over a network connection. They can use automation to scan the internet for any devices open to the connection protocol, guess login details, and then infiltrate it with malware.
Email attachments
Email attachments could be sent through phishing emails seeking to siphon crucial information from you or just any other email from an unfamiliar sender. Some emails may contain attachments or links that’ll infect your device with malware.
Drive-by downloads
This is a cyberattack method for malware to infect your device without any significant action on your part. For example, you might inadvertently click on a link, leading to the automatic download and installation of malware.
Social engineering
Hackers may resort to various social engineering tricks to manipulate you into installing malware on your Mac. This could be through deceitful schemes or crafty approaches to convince you to install malicious software or disclose sensitive information.
P2P sharing and torrents
Developers often rely on peer-to-peer sharing and torrents to disseminate their open-source software. However, these two are also known for being abused as avenues to share malicious code into devices.
Still, Mac computers come equipped with robust built-in security features. These features are formidable protection against the ever-present threat of viruses and malware. For instance:
XProtect
XProtect is a built-in antivirus software that operates seamlessly in the background, conducting scans and promptly isolating any malicious threats it encounters. It stands ready to intercept any malware attempting to infiltrate your system.
Malware Removal Tool (MRT)
Malware Removal Tool works hand in hand with XProtect to secure your Mac. When XProtect successfully identifies malware, MRT swiftly destroys it from your Mac’s system. It performs the delicate function of removing digital infections and restoring your Mac to normal.
App Review, Notarization, and Gatekeeper
Mac has a trifecta of security features, consisting of App Review, Notarization, and Gatekeeper, that work harmoniously to keep it safe. App Review rigorously scrutinizes each app before it enters the App Store, ensuring that only trusted software is available.
Notarization then scans for hidden malice and provides the approval that Gatekeeper relies on to allow or deny an app’s execution. This combined effort ensures that you’re using only certified, safe software.
While these features offer a substantial shield, it’s crucial to understand that vigilance and good cyber hygiene remain paramount. Cybercriminals are crafty, continually evolving their tactics to evade these safeguards.
They create malware designed to circumvent these security measures, making it possible for certain malicious software to slip through the cracks. Here are five common categories of malware that attack your Mac:
- Adware: This malware overwhelms you with many ads and pop-ups. Some websites have numerous Ads that appear whenever you click on any section of the webpage. Certain adware pop-ups may even lead you to harmful websites if clicked.
- Spyware: Spyware is software that secretly monitors your online activities without your knowledge or consent. It can capture every online action you take, exposing sensitive information such as emails and login credentials to cybercriminals.
- Trojans: Trojans disguise as seemingly legitimate programs that cybercriminals trick users into downloading. Once you click the download link or file, hidden malware within the Trojan is secretly installed on the Mac, often with malicious intent.
- Ransomware: Ransomware is malicious software that locks down your device, rendering your data, applications, and files inaccessible. You’re then required to pay a ransom, frequently in cryptocurrency, as a condition for unlocking your Mac.
How to detect and remove Malware on Mac
When you start witnessing the following behavior from your Mac, there’s a high probability that it is infected with malware:
- Slow than usual performance
- Constant pop-up Ads
- Files getting locked and encrypted
- Redirections to various fake pages and websites
- Changes in the Browser’s default search engine.
If you notice the above symptoms, check for malware on Mac, and follow these simple steps to get rid of it:
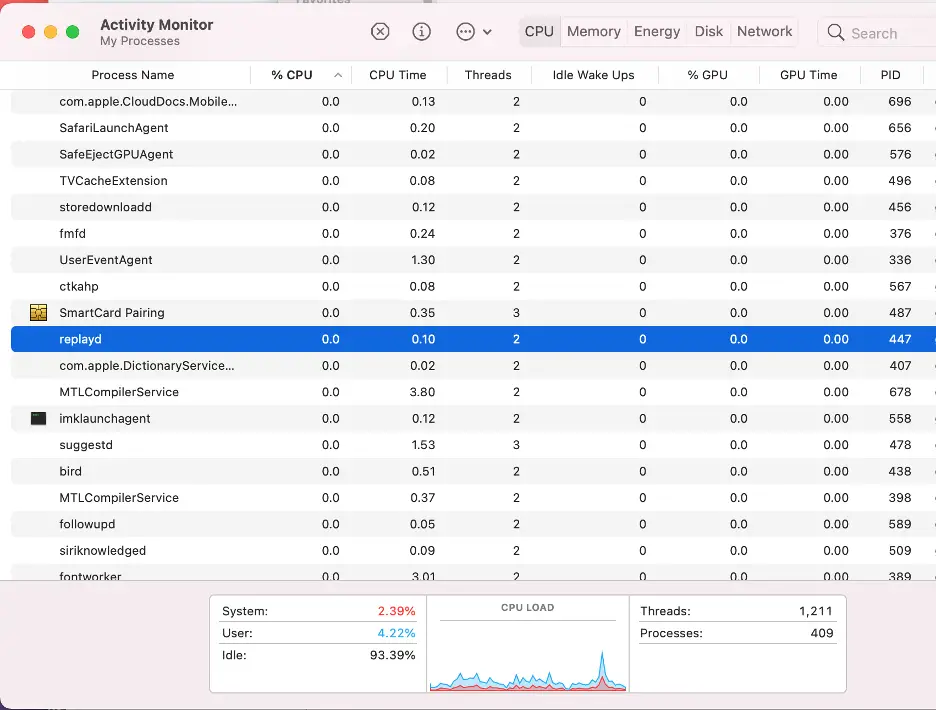
Use Activity Monitor
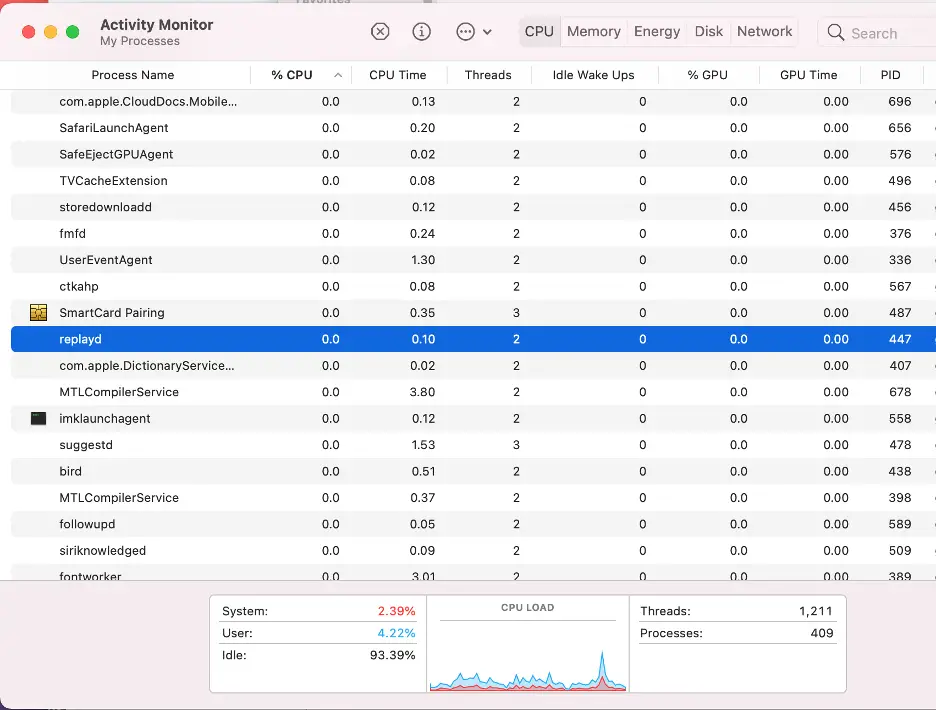
When dealing with a potentially infected Mac, your first line of defense is the Activity Monitor. This built-in macOS tool monitors running processes, including those running in the background.
If any processes are eating up space on your Mac, the Activity Monitor will help you see it. The tool should always be among the first steps in Mac malware removal and returning your device to its normal functioning. Here’s how to check Activity Monitor for macOS malware:
Go to the Applications folder
Click on Utilities
Proceed to click on the Activity Monitor
Click the CPU tab and sort processes by CPU usage
Look for unfamiliar processes consuming significant CPU power.
If you identify anything malicious, such as an App you never installed, follow these steps to remove it:
Open Activity Monitor from Applications
Locate the problematic app in the processes list
Click the x button to quit it
Move the app to the Trash from your Applications folder and empty it.
While this method is a good start, it may only partially eliminate all traces of Malware. To ensure thorough removal, proceed to uninstall suspicious apps.
Uninstall suspicious apps
Mac users enjoy Apple’s protection to keep apps free of known malware. There are also additional protections to enforce access from apps to user data.
As a Mac user, you know that an app notarized by Apple indicates that it has been checked for malicious software, and they found none. However, if you unintentionally install a malicious app on a Mac, it’s vital to remove it promptly.
You can do this by following these steps:
Go to your Applications folder
Drag the app to the Trash
Navigate to Folder
Type ~/Library
Proceed to check the application support folder for related files to the app, then delete them. Look in other folders within ~/Library, such as Launch Agents and Launch Daemons, and remove anything related to the app.
Disconnect from the Internet
Malware can still work and wreak havoc on your Mac without the Internet. Common types of malware on Mac are designed to work offline. However, most of them are designed to infiltrate your device using the internet.
They rely on internet connections to steal crucial data and spread it even further. To stop it, turn off your internet connection when dealing with potential malware.
Here is how to get started:
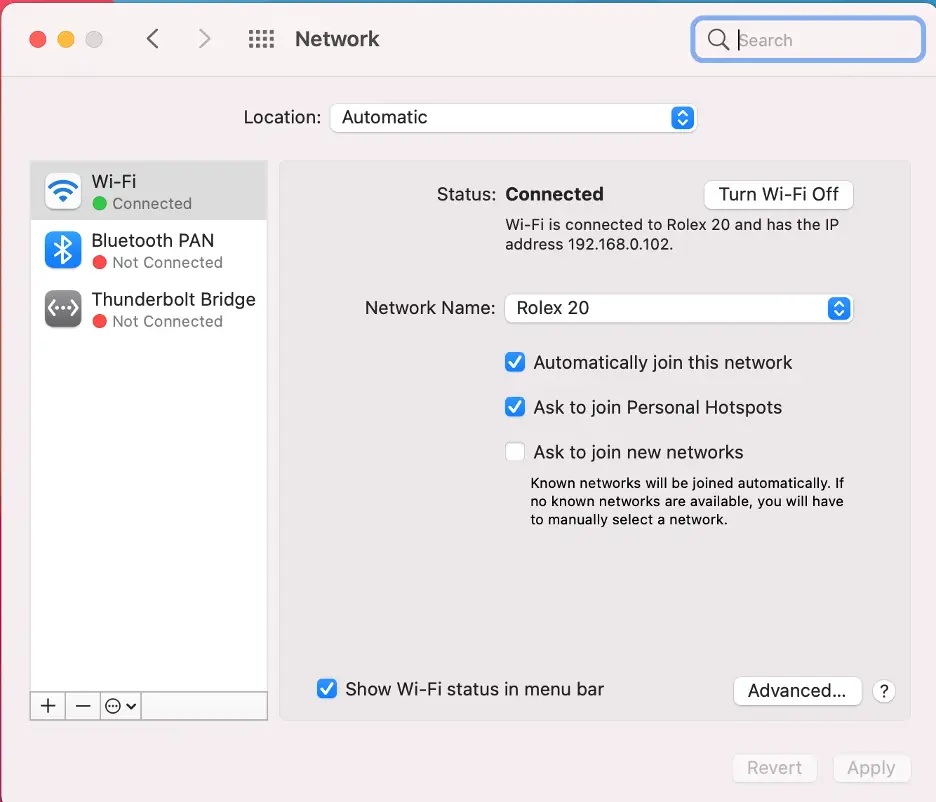
Access System Preferences
Click on Network
Select Wi-Fi from the sidebar
Click Turn Wi-Fi Off.
Boot into safe mode
Sometimes, your device can be attacked by malware that launches as soon as macOS starts. The only first-hand solution you have is to boot your Mac in safe mode. This will help eliminate the malware while checking your start-up disk and clearing system caches.
Here’s how to do it:
For Intel-based Macs:
- Restart your Mac
- Hold down the Shift key during the start-up process
- Wait for the login Window to appear and release the key.
You’ll see Safe Boot in the screen’s upper-right corner.
Follow these steps to confirm Safe Boot is enabled:
- Click the Apple logo
- Go to About This Mac
- Click System Report
- Click on Software
- Check and confirm if the Boot Mode says Safe.
Run an antivirus Scan
On top of the above-highlighted steps, manual malware removal is also possible and can help get the job done. While time-consuming, antivirus software can quickly scan your entire Mac manually for threats and suspicious behavior.
Most of these apps and software have extensive databases to identify and remove malware effectively on your Mac.
Final thoughts
Your Mac can still get malware and viruses despite Apple’s efforts to keep their devices safe and secure. As a Mac user, you must stay vigilant and always protect your device from malware and other cyber-attacks.
This is crucial to maintaining its performance and data security. The above-outlined steps will help you to effectively identify and remove malware from your Mac, keeping it running smoothly.
Remember to keep your system and apps updated and maintain good digital hygiene to protect your Mac from future threats.