Cisco Firesight Manager is management device which is either run on a Virtual machine or either hardware it’s same with Firepower, it’s available in both software module and Hardware appliances.
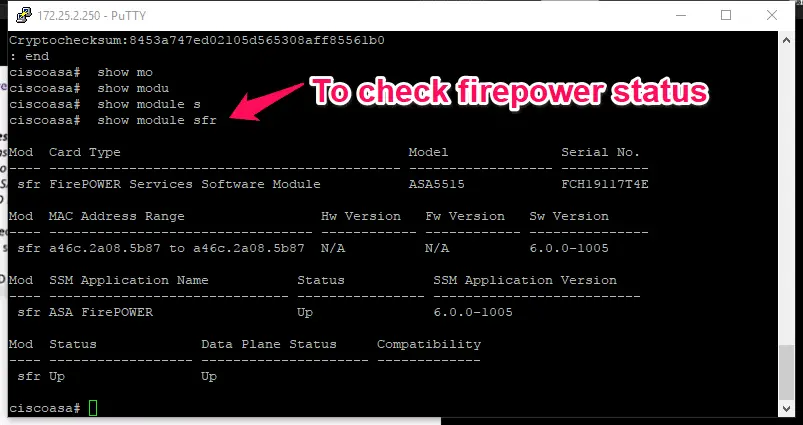
In Our current scenario, firepower software module is installed on current Cisco ASA firewall that you can easily verify with entering #show module sfr command in the global configuration mode.
It will show you, Status of your Firepower module or appliances, as mentioned in below screenshot firepower status is UP.
There is some pre-requisite before integrating Firesight with Firepower:-
- Make Sure 443 is allowed between ASA and Firesight
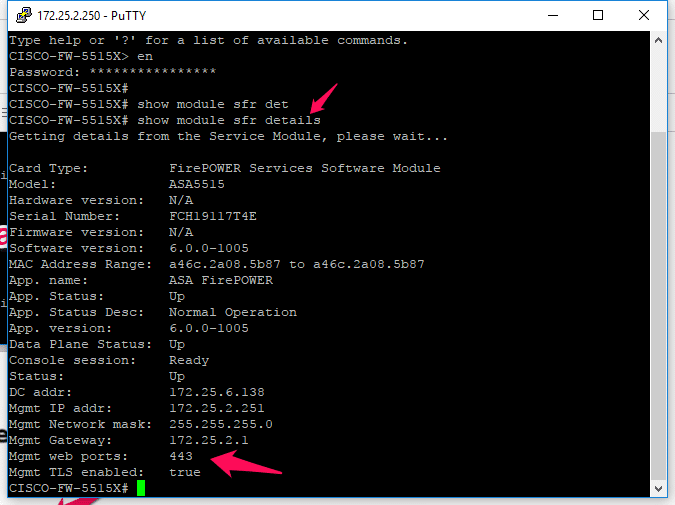
You are easily able to verify this by issuing #show module sfr details command in global configuration mode on ASA.
It will show you “mgmt. web ports = 443” and “mgmt. TLS=enabled” means 443 is allowed for communication.
- Compatibility of Firesight module
My , Current Firepower version = 6.0.0
ASA 5515 = 9.8(1) .5
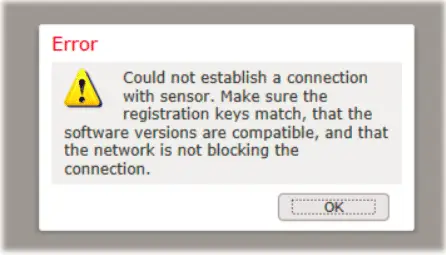
For current firepower version, only firesight 6.0.1 is supported. You will get below error message.
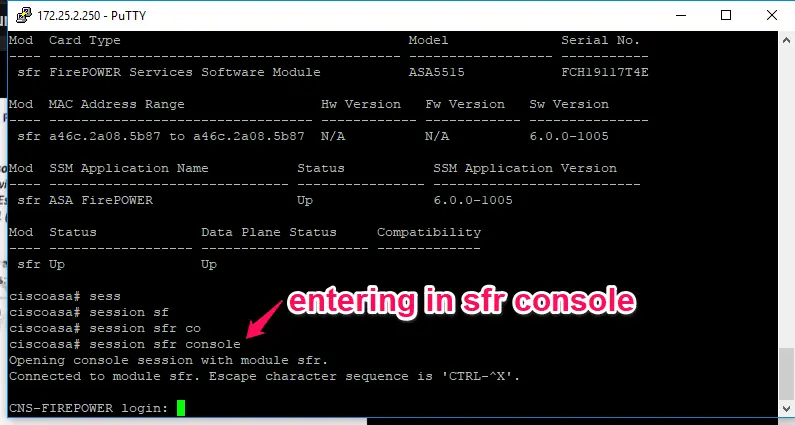
To enter into SFR console from the Cisco ASA, enter #session sfr console command from the global configuration command.
Here are current passwords is default username = admin, Passwords = Admin123
Now you need to add your manager IP by
- Configure manager add manager_IP Yoursecretkey
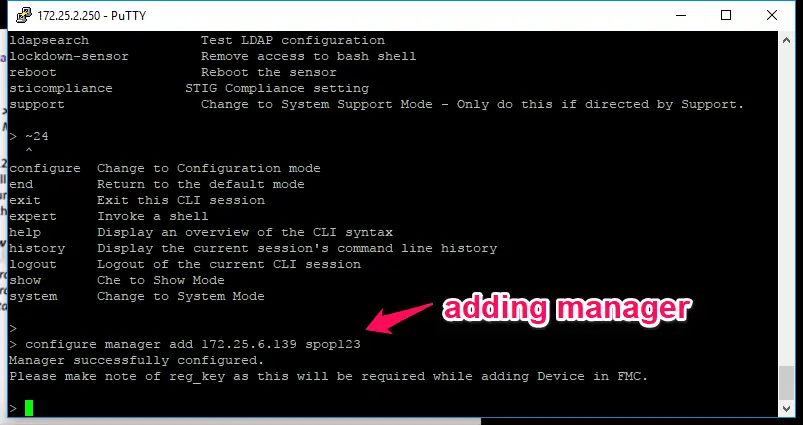
Now enter the command #show managers to view the manager registration status.
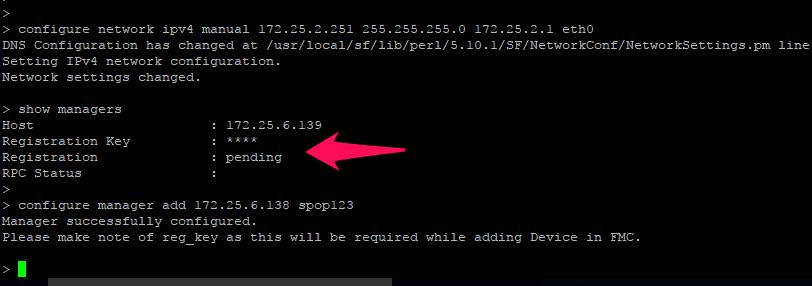
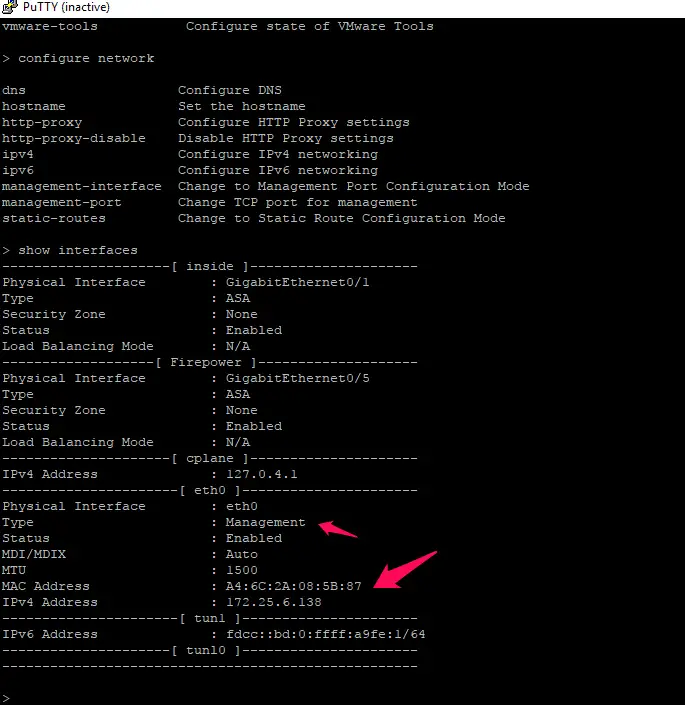
Remember one thing here is you need to integrate Cisco firepower module with firepower, not the Cisco ASA firewall itself. For that issue, the >configure network command to view the management IP address of firesight management IP.
Now you need to login to your Firesight manager by navigating to
Devices > Device Management > Add Devices and enter the details of SFR IP along with registration key that you entered in the time of manager addition on the cisco firepower.
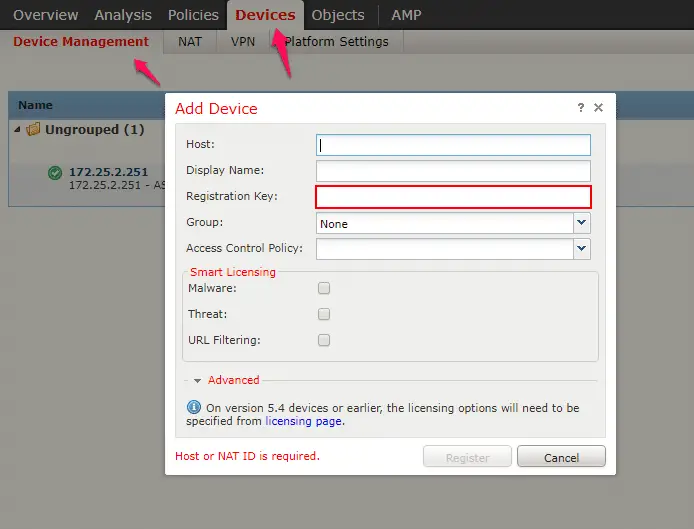
After integration, it will show you integrated device IP under device management.
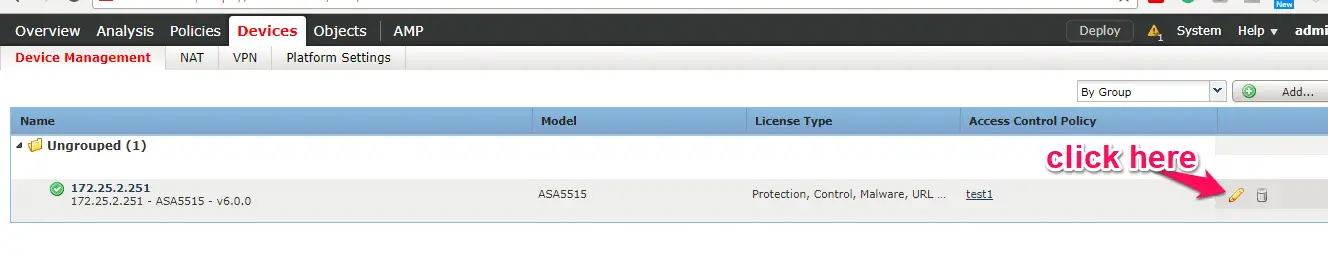
Click on the edit icon to Edit icon to view the more details
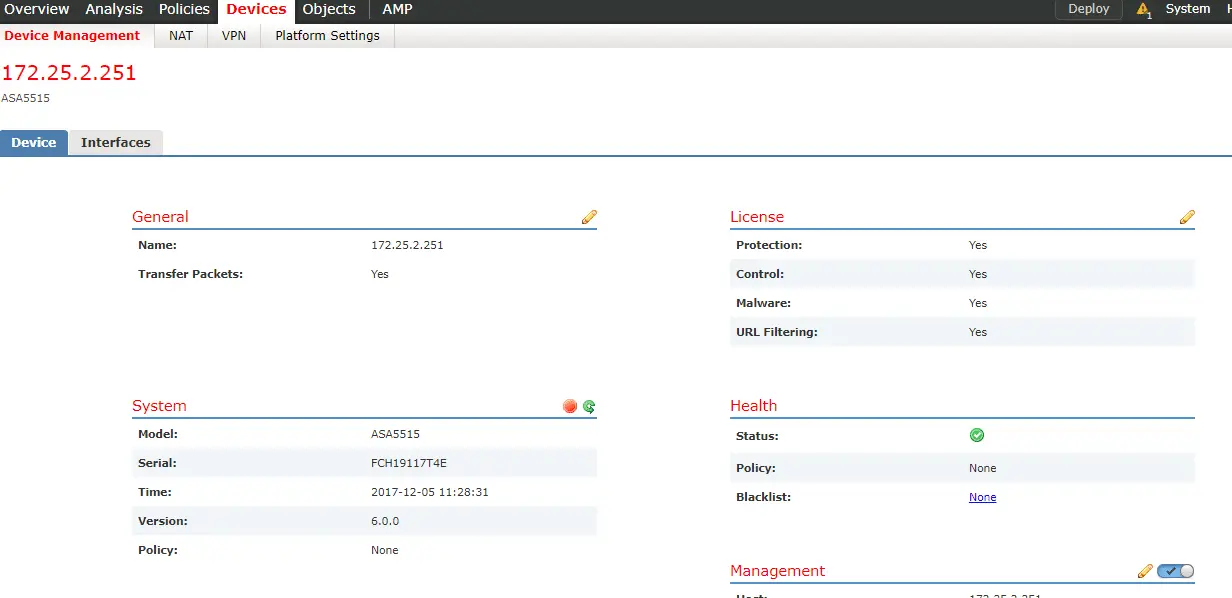
To redirect traffic from ASA to firesight:-
In Router mode:-
1-Configured access-list to specify what traffic will be redirected to SFR for inspection
access-lsit SFR extended deny ip ……..
access-lsit SFR extended permit ip any any
2-configured class map to match access-list created in step 1
class-map SFR
match access-list SFR
3- associated class map to global policy.
policy-map global_policy
class SFR
sfr fail-open monitor-only
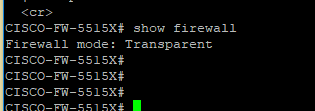
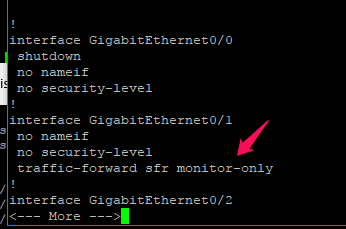
In our Scenario, ASA is running under Transparent mode
And currently, Gig0/1 is used for monitoring this traffic
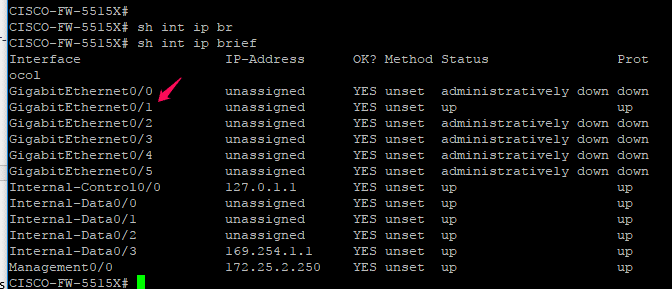
Cisco FirePOWER SFR Module Cannot Ping
One issue I faced here is I am not able to ping from Firepower Module, which you can be fixed with below command.
admin@-SFR:~$ sudo chmod u+s /bin/ping
We are recommending our readers to read Cisco Firepower Threat Defense (FTD) to achieve their carrier goal in Cisco Firepower technology.



























