A new word for many computer technicians but very helpful for users to be ignored by experts. So let’s start learning about ‘crc sha’ in the present article.
crc sha is a modern instrument found in present software due to which, many do not know its function, what does the term ‘crc sha’ means, where it is found, and many other things.
crc sha is an instrument used nowadays to detect the integrity of the files or also known as File integrity .
It enables users to create a hash code(It is also known as hash values, hash codes, digest, or just hashes, are the values returned by the hash function.
These hash codes are returned with another hash code by the devices that are equal to the algorithm, not all the different objects are required to send different hash codes)for the downloaded files from the internet so that it can detect the file’s integrity.
File integrity is the method and the process that takes place to prevent the data from getting attack by cyberattacks so that no unauthorized changes can be made by them.
The integrity of the file tells the users if an authorized hacker has used the file or not. Fiel integrity becomes mandatory with the course of time due to networks and configuration getting complex day by day.
Before we go into the details about crc sha, let’s find out what these 2 words mean separately and what their function is.
CRC:-
CRC is the short form of Cyclic Redundancy Check which was invented by W. Wesley Peterson in the year 1961.ITt is a 32-bit function used in almost all the standards that were published in 1972 after the work of several researchers on it.
CRC is based on the Cyclic error-correcting mode theory (algorithm) which is used commonly in digital networks and storage devices. CRC is the most common function known for detecting error and then correcting it.
A cyclic redundancy check allows the device to use a method of finding the check value or CRC which is a fixed short length bitstream (also known as a binary sequence as it is a sequence of bit).
It allows the users to detect any accidental changes or errors made by unauthorized users in the communication channel as well as to detect any changes made in magnetic and optical devices storage.
After finding the CRC, it christens the block of data which have to be sent or stored with this CRC forming a Codeword also known as the checksum.
A device when receiving or reading this codeword compares the check value of this codeword with its own or in the same way as before performs a CRC on the whole check value and then compares the result it gets with the same expecting residue constant.
If the result after comparing does not match with the expected residual constant then the file is used by an unauthorized user and the block contains altered data due to which the device may take certain action against it, either by rereading it completely for the second time or by requesting the sender to send it again.
If the result came back with the same expected residue constant then the data is said to be error-free but as most of the things we have in the present time have a chance of carrying defect so does these files do.
Cyclic redundancy Check is appreciated by the known users due to its simple implementation in hardware, smooth contemplation of mathematical equations, and is the easiest way to detect any error in the file created by noise in the communication channel.
The check value has a fixed short length bit generated by a function that is used as a hash function from time to time. It is also best to detect and fight against the attacks of burst force that is the sequential flow of inaccurate symbols in the messages.
CRC uses Generator Polynomial with either having 0 or 1 as its coefficient. It treats the check values as a polynomial.
At the time of dividing the data bits, if the remainder comes as 0 then the file is transmitted without any altered or error in the communication channel and can be allowed, and if the remainder came as nonzero then the file send becomes full of errors.
The remainder will always be zero so the file with zero remainders won’t be detected by the CRC code. When the check value of CRC is n but long then it is also called an n bit CRC.
SHA:-
The Secure Hash Algorithm (SHA) was published as a Federal Information Processing Standard (FIPS) by the National Institute of Standards and Technology( NIST).
Secure Hash Algorithm is a menage of cryptographic hash functions whose main aim was to protect the data by providing a password or something. The most important function of SHA is to verify the integrity of the downloaded file or any information from the internet.
The cryptographic hash function is an inevitable work called determinism that means the user will always get the same type of response in every hash but they won’t get different messages with the same hash value as well as it is very fast to fetch the assigned hash value for any given messages. The hash function uses a bitwise operation, modular addition, and compression functions.
The cryptographic hash function is a hash function(it is a function used to convert arbitrary size data into fixed-size output. The hash function returns the value known as hash values, hash codes, digests, or just as hashes.
The cryptographic hash function is a one-way function that means once it is done it is impractical to reverse it.
Every single message has its own uniques hash value which another message may have a different unique value that can never match with one another.
These hash values, codes, digests, or whatever users want to call them from the name mentioned above are then collected together in a hash table structure.
These signals are also unique and because of their property of determinism as they depend on the hash value assigned to them which was in itself unique.
When these new-made hash codes are compared with the previous one and they are both completely match then the sent information is not altered during the transmission and if not then the data is altered by the hacker.
All these unique hashes made it very hard for cyberattacks to happen which made this function the most secure a user could ask for.
The SHA family is a group of 6 members, the members of the Secure Hash Algorithm keep getting updated compare to its previous members.
The main differences between these versions are the length of the bits or number of the bits given by the hash function to the file that is also known as a message digest.
The most fascinating thing about this hash code is that the more the length of the digest has, the more tight security it will have so that it would be pretty hard to break it by using brute force.
These members are SHA-0, SHA-1, SHA-224, SHA-256, SHA-384, and SHA-512. SHA-0 is the first version of the Secure Hash Algorithm published in 1993 by the National Institute of Standards and Technology(NIST) made by the National Security Agency of USA (NSA) and later the new updated version of the first member was made because it was the most vulnerable and easy to hack in.
SHA-1 was the better version of the SHA-0 due to its being most vulnerable, SHA-1 was also made by the National Security Agency as a Digital Signature Algorithm’s part which uses a 160-bit hash function.
It bears a resemblance to the MD5 (Message-Digest algorithm 5 ) but in this version of cryptography also found a weakness due to which after 2010, it was not used widely as it was once used by the cryptographic users.
Similarly, all these members of the Secure Hash Famly exceed the other by the addition in their bit number as SHA-2 has its own family of hash functions containing variable digest or hash values. SHA-224, SHA-256, SHA-384, SHA-512 have different bit lengths such as 224, 384, 512 etc.
The second and the fourth function is also called as novel hash functions due to having respective 32-bit and 64-bit sequence and are also known as bitstream.
The 6 members of the family of the Security Hash Algorithm start the process by starting the process of assigning the message according to the Merkle Damgard Strengthening Technique.
How to View the SHA value of any windows file?
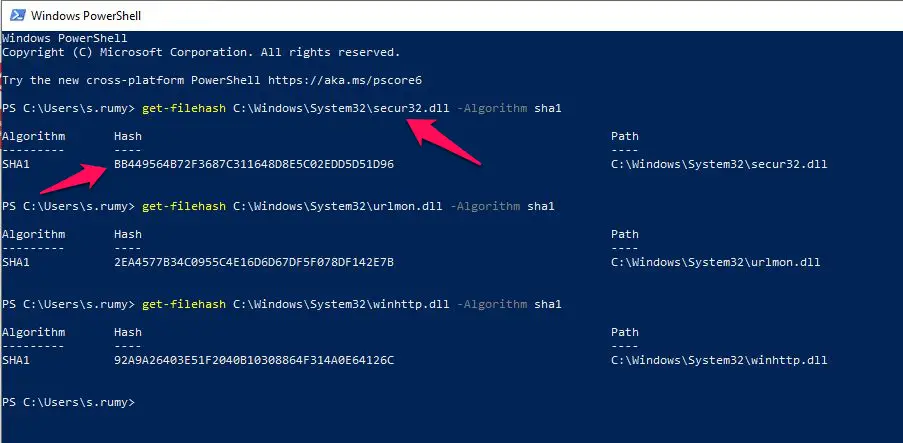
With PowerShell, you are able to view the SHA value of any file. like in my case I want to view the SHA value of the DLL file named secur32.dll under the system32 folder.
open the PowerShell by searching PowerShell in the start menu and enter the below command
get-filehash filelocation -Algorithm sha1
like in my case my file location is C:\Windows\System32\secur32.dll
so my command will be
get-filehash C:\Windows\System32\secur32.dll -Algorithm sha1
it will show you the Hash value of the file.
What is crc sha?
CRC aka Cyclic Redundancy Check is a function used to check whether the data sent is altered or not during the transmission by creating a checksum or check code and SHA.
SHA stands for Security Hash Algorithm is most widely used in networking as well as in many software and in the windows operating system like Windows 10, 8, even Window 7 promotes the ‘crc sha’ for the same purpose that is to check the integrity of the file downloaded over the internet by users.
In spite of being very helpful, any users are not aware of the ‘crc sha’ option available to them because of it being recently discovered. These users can find the option of ‘crc sha’ in the context menu.
Importance of crc sha:-
CRC-SHA( Cyclic Redundancy check, Secure Hash Algorithm) together are present as a single option in many software and are utilized in checking the file’s integrity after downloading it from the internet by providing them a hash code.
The device then matches the new hash code with its own hash code and if the hash codes match with each other then the file downloaded is not modified or altered by unauthorized users such as hackers.
Many users want to remove this option as sometimes they do not want to use it or they do not know how to use it. If you are one of them they just follow the prescribed steps to remove the crc sha.
Step 1: Search and Launch “7-ZIP” from the start menu’ search bar or as most new Windows users call it Cortana Search Bar.
Step 2: Now, navigate to Tools> Options.
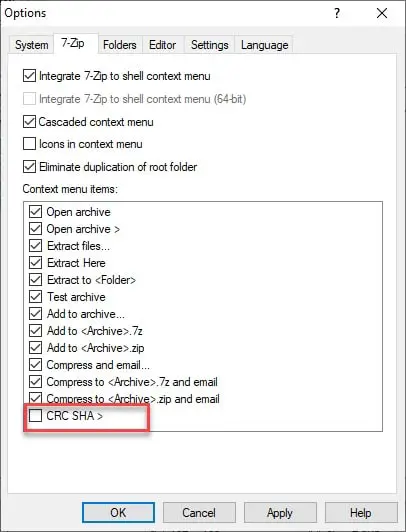
Step 3: On the appeared Window, go to the 7-ZIP tab, uncheck crc sha option, click Apply, and OK.
This will remove the crc sha option from your computer.
📗FAQ
What is CRC and SHA?
CRC (Cyclic Redundancy Check) and SHA (Secure Hash Algorithm) are two types of hash functions used in computer science to verify the integrity of data. They are commonly used to check if data has been altered or corrupted during transmission or storage.
What is CRC 7zip?
CRC 7zip is a type of Cyclic Redundancy Check (CRC) used by the 7-Zip file archiver to verify the integrity of compressed data. It is a 32-bit checksum that is computed based on the contents of the compressed file.
What is Windows CRC?
Windows CRC is a built-in tool in Microsoft Windows that allows users to compute and compare cyclic redundancy checks (CRCs) for files or folders. It can be used to verify the integrity of downloaded files or to detect if files have been modified.
What is CRC SHA in Windows 10?
CRC SHA in Windows 10 is a feature that allows users to compute both the CRC and SHA checksums for files or folders. The CRC is a 32-bit checksum used to detect errors in data transmission, while the SHA is a more secure hash function used for cryptographic purposes.
Is CRC faster than SHA?
Yes, CRC is generally faster than SHA as it is a simpler and less computationally intensive algorithm. However, SHA is considered more secure than CRC and is commonly used in cryptographic applications.
Is CRC a hash?
Yes, CRC is a type of hash function used to verify the integrity of data by generating a fixed-length checksum based on the contents of the data.
Should I trust 7-Zip?
7-Zip is a widely used open-source file archiver that has been audited and found to be secure. However, as with any software, there is always a risk of vulnerabilities being discovered, so it is important to keep 7-Zip and other software up-to-date to ensure maximum security.
Is CRC a good hash function?
CRC is a good hash function for detecting unintentional errors in data transmission or storage, but it is not suitable for cryptographic purposes as it is susceptible to intentional tampering or collision attacks.
What is CRC why it is being used?
CRC is a type of checksum used to verify the integrity of data by generating a fixed-length value based on the contents of the data. It is commonly used in data transmission or storage to detect errors or corruption.
What is the difference between CRC and hash?
CRC and hash are both types of algorithms used to generate a fixed-length value based on the contents of data, but they have different purposes.
CRC is primarily used to detect errors in data transmission or storage, while hash is used for a variety of purposes including cryptography, data retrieval, and data deduplication.
Why is CRC needed?
CRC is needed to ensure the integrity of data during transmission or storage. By generating a fixed-length checksum based on the contents of the data, CRC can detect errors or corruption caused by factors such as noise, interference, or storage degradation.
What does CRC mean in RAM?
CRC in RAM (Random Access Memory) refers to a cyclic redundancy check that is used to verify the integrity of data stored in memory.
It is commonly used in memory controllers to detect errors caused by factors such as electromagnetic interference or component failure.
What is SHA in computers?
SHA (Secure Hash Algorithm) is a type of cryptographic hash function used to generate a fixed-length value based on the contents of data. It is commonly used in computer security applications such as password hashing and digital signature verification.
Which SHA hash is most secure?
SHA-3 is currently the most secure of the SHA hash functions as it was designed specifically to address the security weaknesses found in previous versions of SHA.
Which CRC is used in Ethernet?
The CRC used in Ethernet is called CRC-32 or Ethernet CRC. It is a 32-bit Cyclic Redundancy Checksum that is computed based on the contents of an Ethernet frame. It is used to detect errors or corruption in the transmission of data over an Ethernet network.
Which protocols use CRC?
CRC is used in a variety of protocols to verify the integrity of data. Some examples include Ethernet, USB, SATA, and Bluetooth.
What can CRC not detect?
CRC is designed to detect common types of errors that occur during transmission or storage, such as single-bit errors, burst errors, and most random errors. However, it is not able to detect all types of errors, such as errors that affect an even number of bits or errors that occur in specific patterns.
What OSI layer is CRC at?
CRC is not associated with a specific OSI layer as it can be used at any layer where data integrity needs to be verified. However, it is commonly used at the data link layer in protocols such as Ethernet.
What layer is CRC done?
CRC can be done at any layer where data integrity needs to be verified, but it is commonly done at the physical or data link layer of the OSI model.
Is 7-Zip Russian?
Yes, 7-Zip is a file archiver developed by a Russian software engineer named Igor Pavlov.
Is 7-Zip a vulnerability?
While 7-Zip has been audited and found to be secure, like any software, it is not immune to vulnerabilities. It is important to keep 7-Zip and other software up-to-date to ensure maximum security.
Is 7-Zip spyware?
No, 7-Zip is not spyware. It is a legitimate file archiving software that has been widely used for many years.
What are worst hash functions?
The worst hash functions are those that are vulnerable to collisions, meaning that two different inputs can produce the same hash value. Some examples of vulnerable hash functions include MD5 and SHA-1.
What is the most significant bit in CRC?
The most significant bit in a CRC is the leftmost bit of the polynomial used to generate the checksum. It is also known as the highest-order bit or the leading coefficient.
Is CRC32 hash safe?
CRC32 is not considered a safe hash function for cryptographic purposes as it is susceptible to intentional tampering or collision attacks. It is only suitable for detecting unintentional errors in data transmission or storage.
Can CRC detect 3 bit errors?
Yes, CRC can detect 3-bit errors in data transmission or storage. However, the likelihood of a 3-bit error occurring is relatively low compared to single-bit errors or burst errors.
What is CRC in cybersecurity?
CRC in cybersecurity refers to the use of cyclic redundancy checks to verify the integrity of data in secure communications, password hashing, and digital signature verification.
What is the CRC hash function?
The CRC hash function is a type of cyclic redundancy check used to generate a fixed-length checksum based on the contents of data. It is commonly used to detect errors or corruption in data transmission or storage.
Can CRC hashing be used as in security applications?
CRC hashing is generally not suitable for security applications as it is vulnerable to intentional tampering or collision attacks. However, it can be used in conjunction with other security measures to provide an additional layer of data integrity verification.
Why is CRC replaced by checksum?
CRC is not being replaced by checksums, as they are two different methods of verifying the integrity of data.
Checksums are a broad category of algorithms used to generate a fixed-length value based on the contents of data, while CRC is a specific type of checksum used to detect errors or corruption in data transmission or storage.
Which hash is best for file integrity?
The best hash for file integrity depends on the specific requirements of the application. For general purpose file integrity checks, SHA-256 is a widely used and secure option.
What is the disadvantage of CRC?
The disadvantage of CRC is that it is vulnerable to intentional tampering or collision attacks, making it unsuitable for cryptographic applications.
Additionally, it is not able to detect all types of errors, such as errors that affect an even number of bits or errors that occur in specific patterns.
What are the main features of CRC?
The main features of CRC include the ability to detect errors or corruption in data transmission or storage, a fixed-length checksum that is relatively easy to compute, and the ability to detect common types of errors such as single-bit errors, burst errors, and most random errors.
What is an example of a CRC checksum?
An example of a CRC checksum is the Ethernet CRC-32 checksum, which is a 32-bit value computed based on the contents of an Ethernet frame. It is commonly used to detect errors or corruption in the transmission of data over an Ethernet network.
Wrap-up:-
In this article, we have tried presenting in front of you one of the most underrated and underutilized services in Windows 10.
Hopefully, you get a clear idea of crc sha.