Before starting to describe Types of Firewalls, I want to describe what is a Firewall and how it’s working.
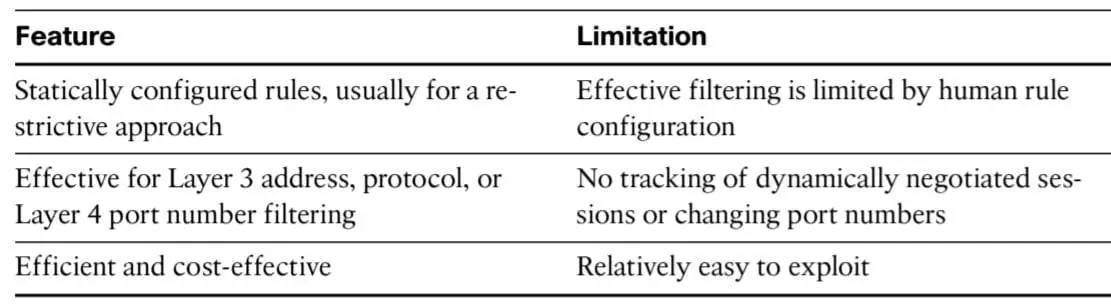
In a technical word ” A firewall is a Hardware/Software device that enforces an access control policy between two or more security domains.
The firewall can enforce security policies on only the traffic that passes through it, not around or behind it. Each firewall has its own set of security policies and its own concept of a trust boundary.”
Above mentioned image is itself enough to tell you what is a firewall? 🤔 really it’s that much easy to understand. 🤷♂️ Yes
Technology is rapidly growing which is bringing also a lot’s of cybersecurity challenges especially hacking. In most cases, you would feel that you are safe until it really gets on you and your system gets hacked.
It is not about just a system sometimes the most important and secret information for an organization gets leaked and there is hardly anything that you are able to do about it. This is why the firewall is important. 😎
A Firewall is designed to protect your privacy and security, by monitoring 👓 your PC/office network for suspicious activity. A firewall is acting as a wall for you against malicious activity.
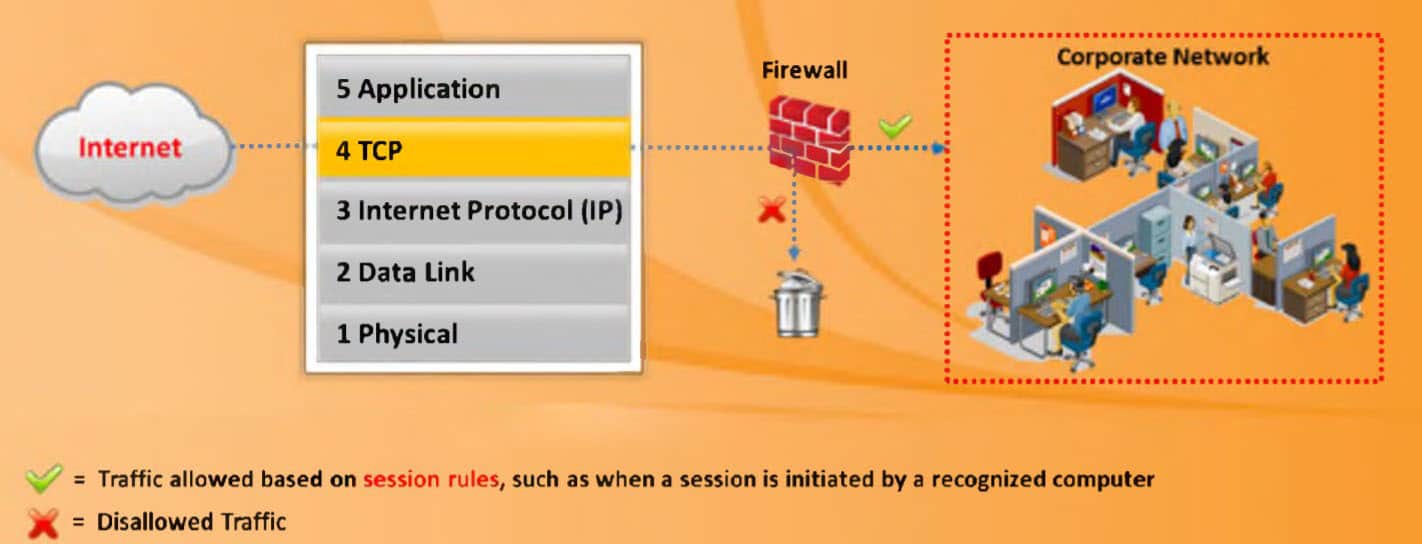
A firewall can basically be referred to as a network security device that monitors network traffic that comes in and goes out and accepts or rejects the data packets based on certain security rules.
This makes it so important in the world of security and makes you wonder about the types of firewalls so that you can use the best suited for your organization.
The network traffic is something that you are not able to understand straight away. The traffic is too large and too heavy to be understood by a human brain and even other technological systems out there.
A firewall is made specifically to deal with the traffic of networks and then see if some unusual activity is going around. The establishment of the barrier is necessary between the income network and income traffic from external sources is necessary in order to neglect any chances of hacking.
A firewall can take one of the following approaches to its access control:-
Permissive access control:- All traffic is allowed to pass through unless it is explicitly blocked.
Restrictive access control:- No traffic is allowed to pass through unless it is explicitly allowed.
Still confused 🤔 Don’t Worry no one can explain better than Keith. Watch out below mentioned video.
There are various types of firewalls that should be discussed in the details. But before that, you would want to know how exactly does firewall work. It carefully analyzes incoming traffic on rules that have already been established.
It guards the traffic at a computer’s entry point. Ports are also guarded at the same point in time because this is somewhere information is exchanged with external devices.
Now it totally depends on which types of firewall you would want for your organization and set the security patterns in your IT firm at the same point in time. So you need to carefully plan your activities before you finally choose a firewall.
Here Are Some of The Major Types of Firewalls
Sure, here’s a detailed chart on Types of Firewalls:-
| Type of Firewall | Description | Pros | Cons |
|---|---|---|---|
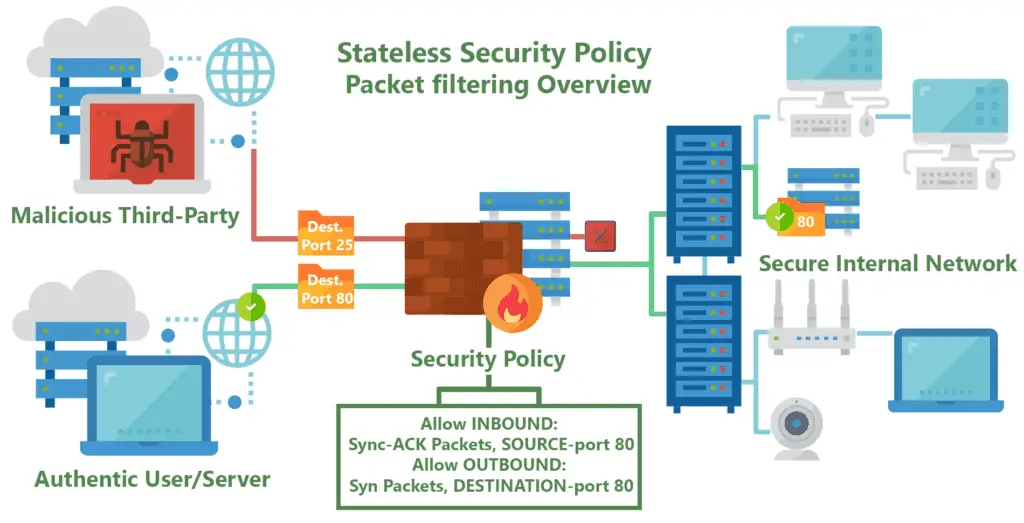
| Packet Filtering Firewalls | Examines network traffic based on source/destination IP address and port numbers, and either allows or denies traffic based on pre-defined rules. | Simple, fast, and inexpensive. | Does not examine the content of network traffic, making it vulnerable to more sophisticated attacks. |
| Stateful Inspection Firewalls | Similar to packet filtering firewalls, but also tracks the state of network connections to determine whether incoming traffic is part of an existing connection. | Offers additional protection by blocking malicious traffic that would otherwise appear legitimate based on port numbers and IP addresses. | Can be resource-intensive and may not be as effective against more complex threats. |
| Application-Level Firewalls | Analyzes network traffic at the application layer, identifying specific types of traffic and either allowing or denying it based on pre-defined rules. | Offers more granular control and can block malicious traffic that would be allowed by packet filtering or stateful inspection firewalls. | Can be expensive and may have performance limitations. |
| Next-Generation Firewalls | Combines the features of traditional firewalls with additional capabilities such as intrusion prevention, deep packet inspection, and application awareness. | Offers advanced threat detection and prevention capabilities, including the ability to block certain types of traffic based on content. | Can be very expensive and may require significant resources to operate effectively. |
| Proxy Firewalls | Acts as an intermediary between the client and server, analyzing traffic before passing it on to its destination. | Offers granular control over network traffic, including the ability to block specific content or apply encryption to certain types of traffic. | Can introduce latency and may be resource-intensive. |
| Cloud Firewalls | A type of firewall that is hosted in the cloud and designed specifically for cloud-based infrastructure. | Offers scalability and flexibility for organizations that use cloud-based services. | May require significant configuration and management to ensure effective protection. |
1. Packet filtering firewall
When you are talking about types of firewalls, you will have to arrive at one of the most basic firewalls that are around. A packet-filtering firewall happens to be the oldest firewall as it was one of the first firewalls which were established.
It creates a checkpoint at a traffic router or a traffic switch. It just checks on the information getting in through the medium of the router. It checks a few things.
The IP address is one of the first things which needs to be taken into the account at all costs and here it is taken into the account as well.
Apart from it, packet type, port number, and other surface-level information need to be taken into the account.
The information packet follows a strict number of rules. If any sort of information blocks those rules and goes past them, the information gets dropped right there and then, and nothing is done any further.
The good thing about this firewall is that the information that it carries is not too heavy. It means that your system will not get affected by its medium.
You will be able to perform your operations and your system will still be able to process other things at the same point in time. The fact that this firewall is not too resource-intensive keeps it at the top of other things.
A packet filtering firewall is the most feasible firewall for your organization. So if your system is not too advanced with all the technological tools and you still want to go for a security system, a packet filtering firewall will work the finest for you.
Your information will not get easily hacked no matter how hard someone tries and there are no chances of the information getting leaked at the same point of time.
This type of firewall is rather easier to bypass as well. You need to get around with the fact that it is the most basic firewall that you can think of which is not going to be difficult to operate.
Pros:-
- It is very simple to use
- It does not impact your resources as it is very resource-intensive
Cons:-
- The security system is not going to ensure a hundred percent safety.
- The set rules can even block the information which shouldn’t be blocked.
2. Circuit Level Gateway Firewall
Just like the firewall that we have discussed above, circuit-level gateways are very simple to use as well. The important thing here is that you should be able to quickly get rid of unusual access to the information.
You would want that the information is circulated around nicely and it does not create damage for you. This is why the firewall is needed in the first place.
You need to make amends with the fact that you are required to have too many resources when you use a firewall. But with circuit-level gateways, you do not require your resources to get consumed at a high level.
This type of firewall works by transmission control protocol handshake. This TCP handshake will confirm the fact that the session of the packet is legitimate and it is not expired. You need to understand that you are required to conduct this information nicely and crisply.
You have to plan it out nicely so that the firewall can work just about fine for you. Firewalls do create a change in terms of security and it keeps you safe. You feel safe at the same point in time and you do not think otherwise.
Circuit level gateways are designed in such a way that you are able to maintain your resources nicely and it does not impact your system much.
You will be able to access the other information on your system without really having to worry about if it is going to work at the same point in time when you are using a firewall in the same system.
But sometimes this firewall might not prove to be all that safe. If a packet contains malware but has the right TCP handshake, the information would pass through and do its damage.
Pros:-
- It is very simple to use just like a packet filtering firewall.
- TCP handshake adds to the level of security.
Cons:-
- Just like a packet filtering firewall, it is not really the safest.
- It might not work on all the devices.
3. Stateful inspection firewalls
This firewall is basically termed as a combination. It contains both packet filtering technology and transmission control protocol handshake. The level of protection that this fusion creates is the next level. When you are running an IT firm, you are already stuck in grabbing out a lot of funds.
So if you have to spend just a little bit more on the security so that what you are trying to build does not fall down, you should be going for the best-suited firewall for your system.
This is an important thing that should always be taken into account while understanding things.
The level of security will be top-notch will never have to worry about what you should be doing at the same point in time.
The above-mentioned firewalls might be cheap and economical for your use but they do not guarantee a hundred percent protection and you need the most amount of surety so that you can access your information freely without having to worry if such information can create any sort of damage for the organization itself.
This technology is going to do a couple of things for you. It is going to be very resource unfriendly. It will carb out the most number of resources out of your system just in order to maintain the level of security which you might not have been able to do otherwise.
It will also slow the transfer of legitimate packets but it will surely not risk your security purposes which is your priority when you are running an IT firm.
The information can be accessed slowly and steadily but if it gets destroyed with a breach of information, you are in loads of trouble and there is no way you can get back from there.
In complete technical definition ” A stateful firewall is a firewall technology that is storing information based on source and Destination IP-address, source and Destination Ports, Initial Sequence number and TCP Flags”
In stateful firewall technology, a firewall is allowing the inside traffic that is going outside and keeping the session for that packet and once it’s seeing the reply from the same packet it’s allowing the connection.
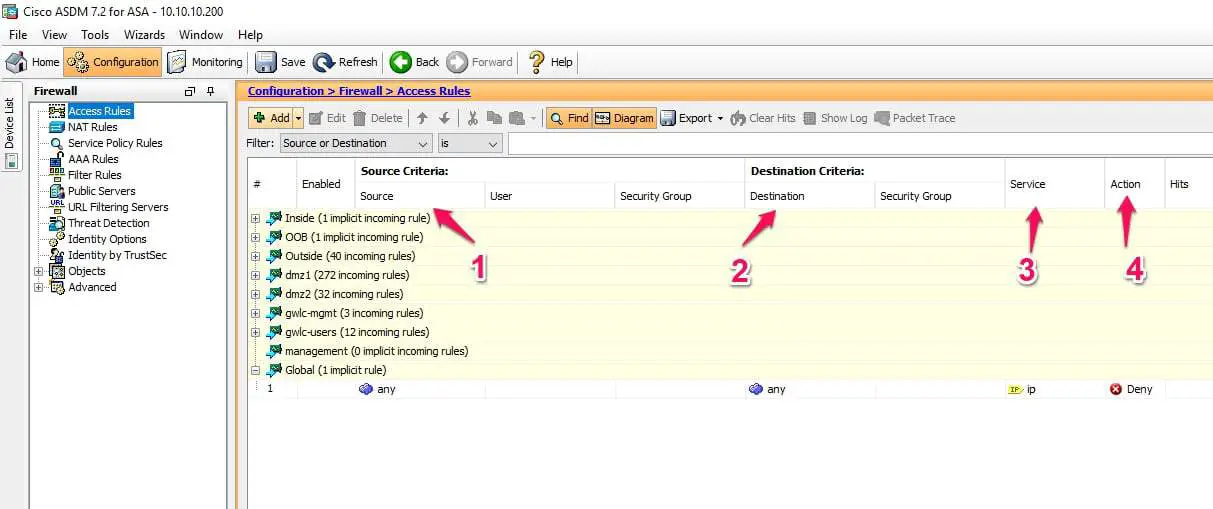
Below is the image of the Cisco ASA firewall which is a stateful firewall, If you see in the access rules is based on Source IP-address, Destination IP-address, Services and Finally action.
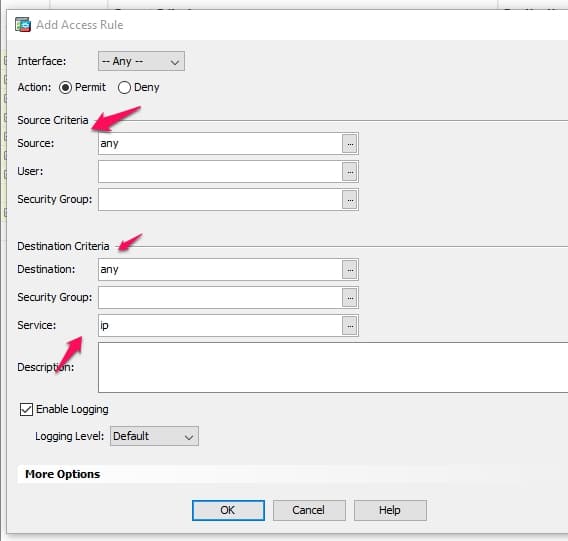
Below is an example of the criteria required for the stateful rule.
Example of Stateful Firewall:-
- Windows Firewall is a stateful firewall.
- Cisco ASA/PIX was a Stateful firewall
- Checkpoint Point Firewall was the First firewall that brings the concept of a Stateful firewall.
Pros:-
- The security levels get improved here
- It will suit your system no matter what is the device.
Cons:-
- It is going to prove costly to install it in the first place
- You will find it difficult to understand the layers of this firewall.
4. Application Layer Gateway ( proxy )
If you are talking about types of firewalls, you would not get a firewall that is more different and unique than proxy firewalls. It operates on the application layer, unlike the other firewalls that we have discussed until now.
It filters the information coming into your internal Network from your internal source. The uniqueness that is there is a cloud-based solution that it provides.
It means that it is going to be using another proxy device. It does not connect the traffic directly. The proxy firewall will first look into the source of the traffic and check if there is any sort of authenticity attached to it.
It looks at both the packet as well as TCP protocol so you do not have to worry about the level of security here. The fact that it checks on the source of traffic nicely and in a descriptive way is something that is very commendable.
Generally, hacking can account at any level and if you try to skip one, you will find malware in your system at the same point in time. It is going to spoil your information like nothing else and you will have to start from the very bottom all over again.
It creates that check and once the check is complete, the packet will be approved. Thus it creates another level of checking on the information which means that it creates another layer of security.
The vaster the security system, the less are the chances of information suffering from anything. The process is going to be even slower than stateful inspection firewalls but if you are getting more security with this firewall, you can let the small suffering get right through. The protection of your network is going to be top-notch with the help of proxy firewalls.
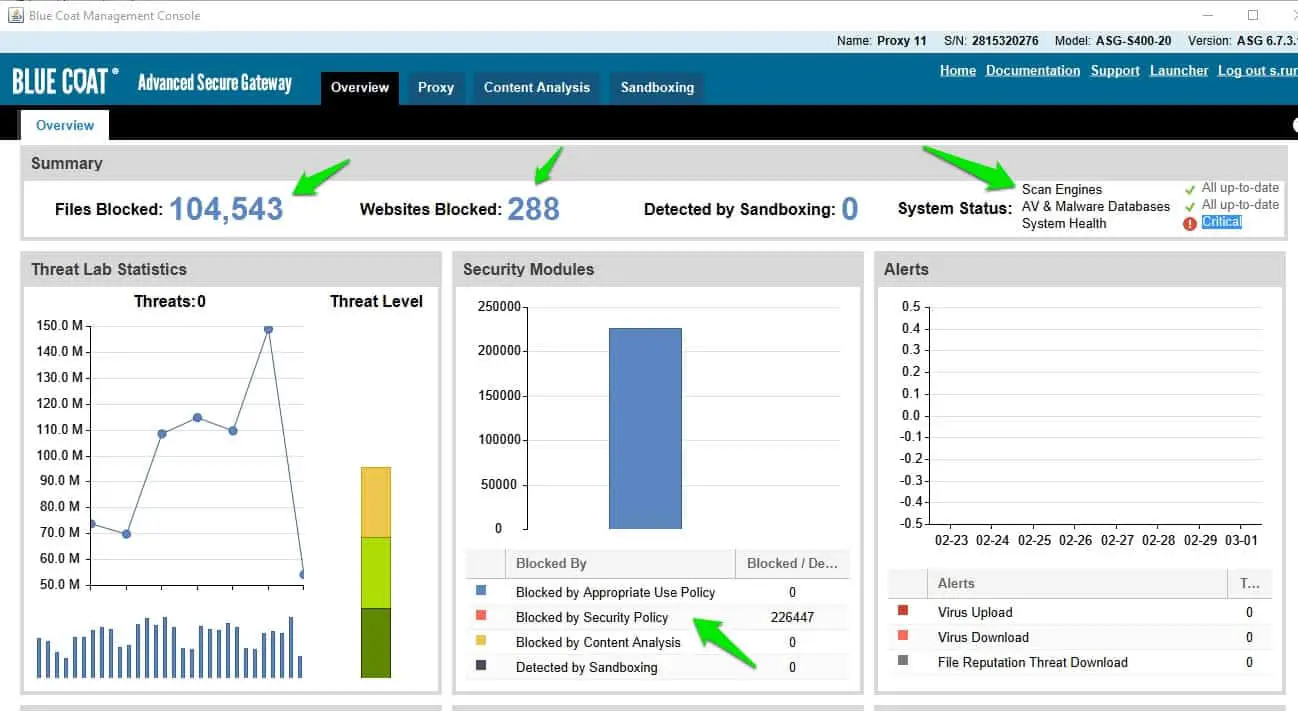
Now let’s have a look at the interface of One of the Top proxies “Bluecoat proxy”,
Note:- Bluecoat Proxy is not a Free proxy server it’s the top proxy server used by the organizations.
As you have seen in the below image, it’s showing the Files blocked, Website Blocked and Website blocked by the security policy.
Pros:-
- It is a very unique firewall and its use proves to be successful as well
- It is one of the most technologically advanced firewalls out there
Cons:-
- The processing here tends to be slow
- Again, it is not that easy to understand it and you will be required to employ experts
5. Next-generation firewalls
As the name suggests itself, it is meant for the next generation and the generation to follow as well. There are three things that are taken to account in the case of this firewall.
Deep packet inspection, TCP handshake check, and surface-level packet inspection. To add to it, there are intrusion prevention systems that are also taken into the account.
This firewall was built with a lot of hard work and there was a lot of time put in to make this firewall and come to terms with it which was not possible so easily.
This firewall is going to ensure security at some other level itself. So even if you are producing the costliest of the information and have not been able to establish a security system that can truly withstand your content and nothing goes out of context, you would need next-generation firewalls in your bag.
Its installation is one of a kind and you are going to see the impact of it straight away too since its design is done in a very different sense in the first place. You would get the benefits of the firewall and security is not going to be an issue any longer for your IT firm.
There are times when people get trapped and do not reach out to the actual next-generation firewalls. You will see various firewalls with the same name but you need to understand the attributes that are mentioned above and they are going to be things that will make it unique.
You should be looking to verify those specific capabilities before investing in a firewall in the first place otherwise you might lose your money and still not get your security system right.
In Complete technical definition,” A next-generation firewalls have full visibility of the application that is passing through the firewall”
Ex:- With a stateful firewall you are able to control the sessions based on IP address and port numbers but what about the application running on the allowed port numbers.
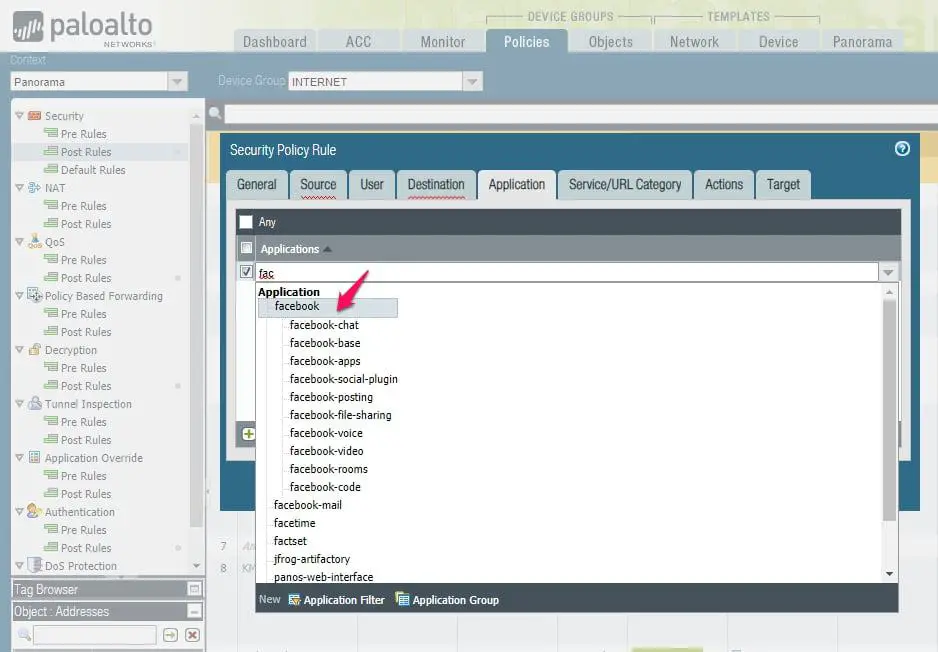
like if you want to control the Facebook or youtube traffic that is running on port 443, you are not able to control it with a stateful firewall.
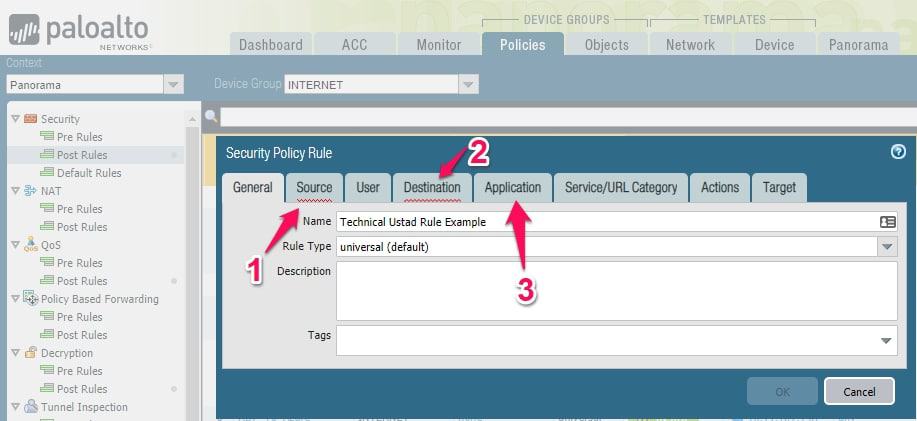
Let’s have a look at the below image of PaloAlto next-generation firewall, if you compare this with Cisco ASA firewall rules you will realize here you have one additional option “Application”
with this, you are able to control applications like Facebook, as you saw in the below image even on Facebook there is multiple options to control like Chat, voice, video, etc that you are not able to achieve with a stateful firewall.
Pros:-
- There are high levels of security ensured here
- It adds intrusion prevention systems which are very rare in other cases
Cons:-
- It is a very costly firewall and new organizations might not find it feasible
- It is very hard to reach out to the correct next-generation firewalls
6. Software Firewalls
This type of firewall has its own set of specialties which sets it apart. These are installed in a local device which is not the case with other firewalls. You would need separate hardware in order to get in with the firewall nicely and carefully.
There is a major benefit that you receive with software firewalls. It is highly useful for creating that defense. The defense will be made in-depth. You will be required to keep away the individual network endpoints from one another.
Isolation is a very important part here. Generally, software firewalls are easy to install and you can keep the security system intact.
It is a time-consuming process. You have to make the individual network endpoints which you might not require on other firewalls that are around. You need to spend your time in but you will get used to it after a point.
It is not difficult to get there but when you make those network endpoints individually, it becomes a washed-up process to follow after a certain point of time.
The good thing here is that you can still get the same level of security that you want from a firewall and you do not have to spend a lot of money to achieve it.
The major advantage you will get here is that every device will be able to stay compatible with a single software firewall. Sometimes you go on to choose a firewall and it does not work on your device. It means you lose all your money in the process.
But you do not face the same situation with software firewalls. The other thing that you need to consider is that you will not be required to go very complicated in order to achieve success with it. Software firewalls can be your go-to security system for a long time too.
Personally, I am using GlassWire Firewall to protect my PC against hackers.
Pros:-
- It is compatible with every device
- The defense mechanism is maintained in a very unique yet subtle manner
Cons:-
- It is a time-consuming process
- There are a lot of complications involved in order to achieve success with it
7. Hardware firewalls
When it comes to the types of firewalls, these firewalls are the polar opposite of software firewalls as the name would suggest itself. In a software firewall, you use no physical appliance. But in hardware firewalls, you are required to use the physical appliance.
It works in a manner similar to a traffic router. The main job done by hardware firewalls is to intercept data packets and traffic requests. It needs to be done before they are connected to the network’s servers.
There are a few things that it does but the primary motive of it is making sure the malicious traffic from outside the network is intercepted before there is a risk involved with the network endpoints of the company.
The inside attacks are possible in hardware firewalls. The thing with hardware firewalls is that you will not be able to understand the capabilities that it possesses straight away.
You will have to buy the hardware firewalls first and only then will you come in terms with it. The capacity to get rid of the risk may vary but you would want to buy a version that can remove the risk completely. You want to eradicate the risk involved at any and all costs.
You have to understand that the manufacturer of hardware firewalls May produce a different firewall in terms of risk that it can eradicate. So you can look at the past experiences of the people before you actually go on to buy it.
It is sure to consume a lot of your time out of the context but security is one of the primary motives of an IT firm and you need to maintain the level of security at all costs. If you choose the right kind of hardware firewalls, you will end up ensuring security.
Pros:-
- It intercepts the data requests really quickly
- The malware is removed in any and all cases
Cons:-
- Inside attacks are very much possible in this case
- Some manufacturers go on to produce hardware firewalls that barely ensures safety in terms of risk
8. Cloud firewalls
This is another one of the types of firewalls whose name suggests the entire thing itself. These firewalls go hand in hand with proxy firewalls as they are used simultaneously by many IT firms.
They compliment each other pretty well and there are many other reasons why they are used on simultaneous terms.
A cloud firewall is used very often in proxy firewalls because sometimes you need to maintain a greater level of security with the kind of information you might have in hand. You need to almost make sure that you are able to have both ends meet at the same point in time.
There is a huge benefit that you are supposed to get with cloud firewalls. You will be able to scale it with your organization. As the organization tends to grow, you need to alarm your security systems at the same point in time.
It is the same as when a human body starts to grow, the desire to eat food and the capacity to eat the food tends to grow at the same point in time.
If you do not eat properly, your body will end up facing a lot of physical problems. The same is the case with your security systems too.
Cloud firewalls are much like hardware firewalls too. They do excel at parameter security just like hardware firewalls. The cost involved here is not huge either and a decent level of security is maintained at the same point of time. The use of cloud firewalls has grown over a period of time and that speaks for itself.
Pros:-
- It can be used in place of proxy firewalls
- It is very simple to install it on your device
Cons:-
- There are times when it is not able to ensure security all that well
- It might not work on all the devices
9. Web Application Firewall ( WAF)
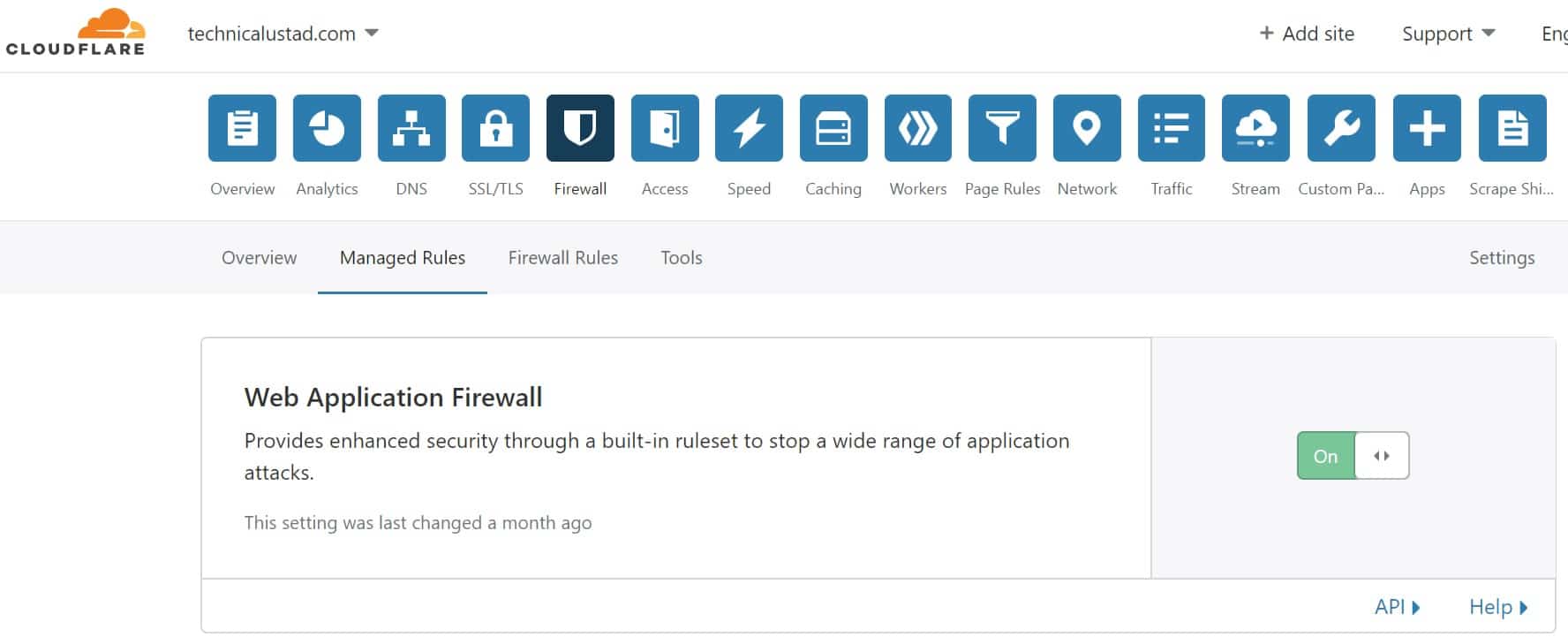
Web Application Firewall ( WAF) is the must-have firewall for every organization especially if they have a public-facing website. WAF is providing enhanced security through a built-in ruleset to stop a wide range of application attacks.
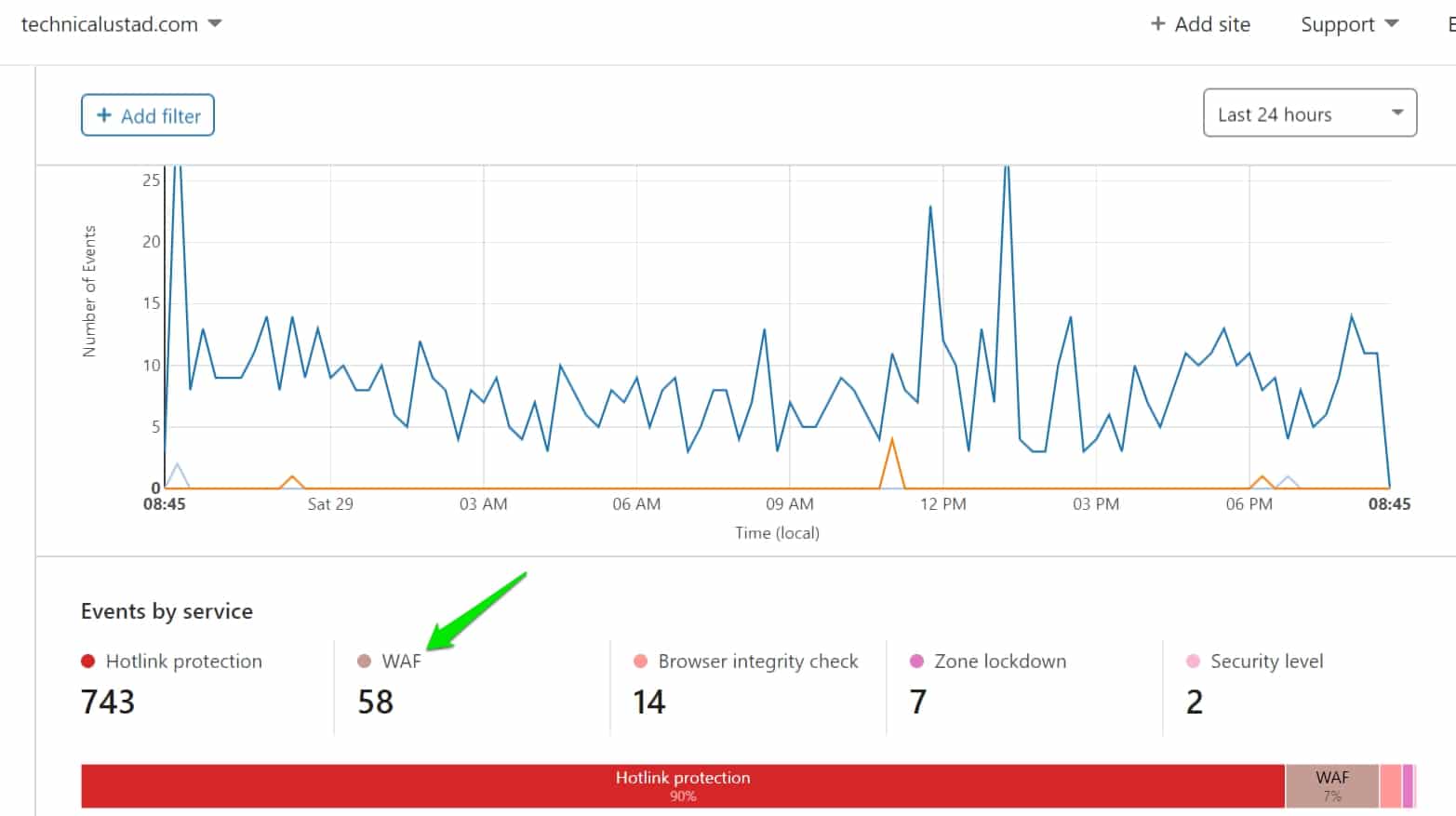
On Technicalustad, we are using the Cloudflare WAF to protect our website.
on average it’s blocking around 50 application attacks on our website
I showed the public WAF like Cloudflare but what about organizations like a bank or government organizations.
Most of the banks are using F5 ASM ( WAF) to protect their websites.
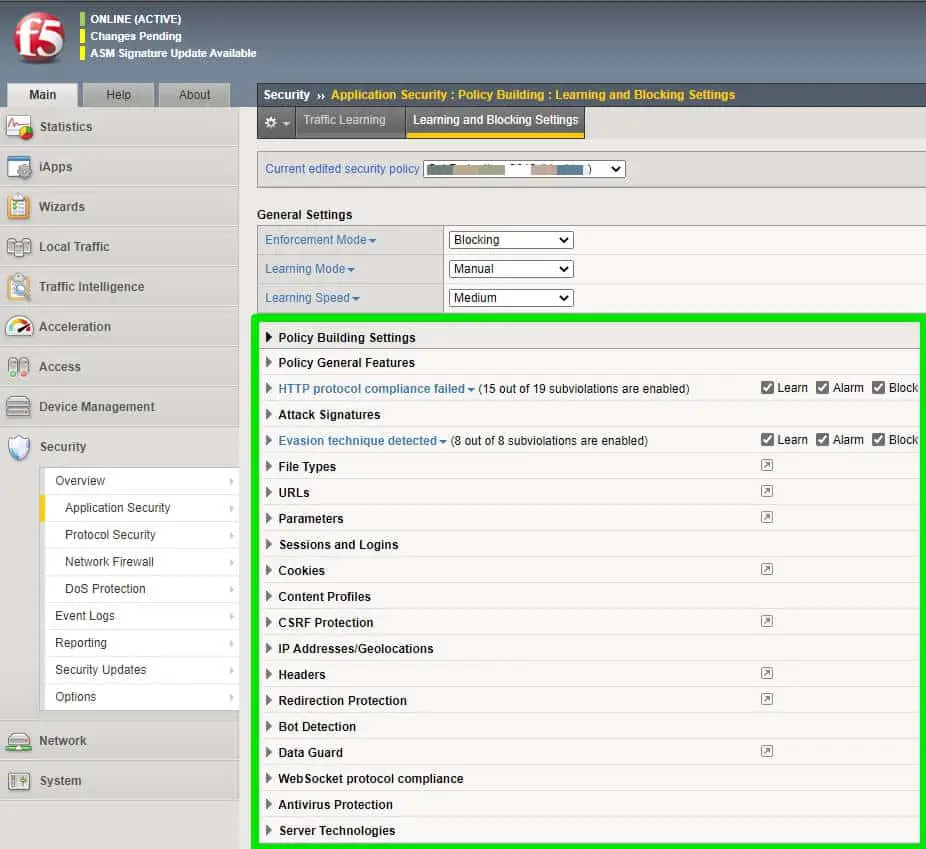
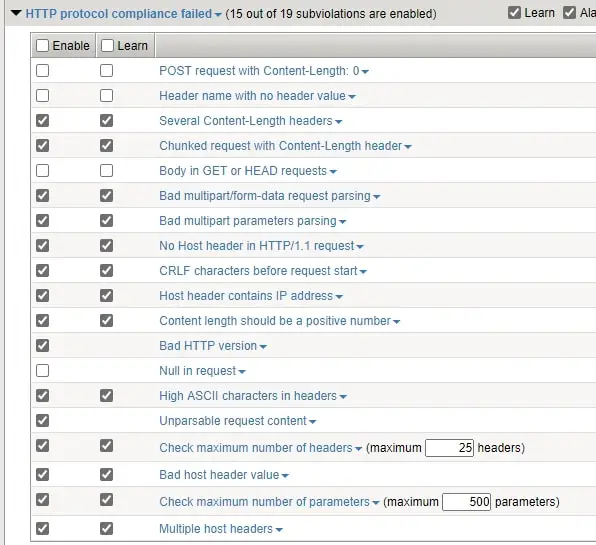
F5 ASM/WAF is protecting an application based on:-
- HTTP Protocol compliance
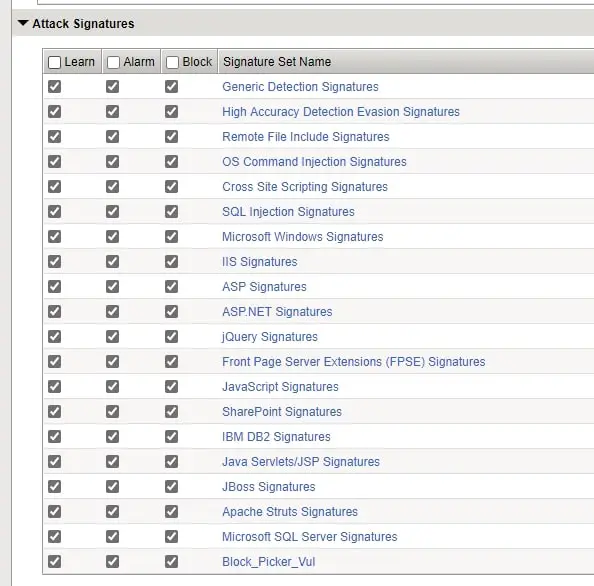
- Attack Signature
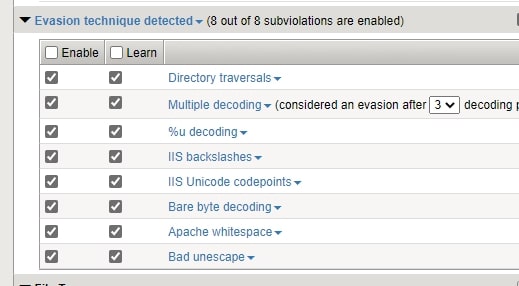
- Evasion techniques
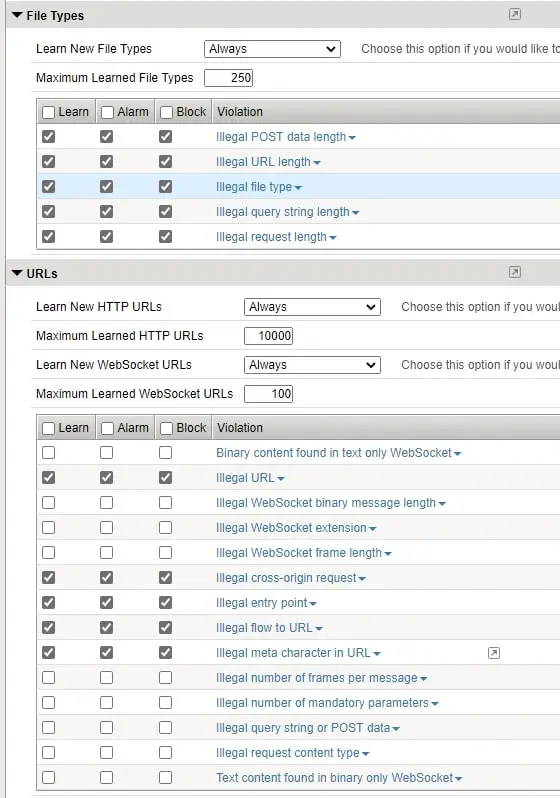
- File Types
- URL’s
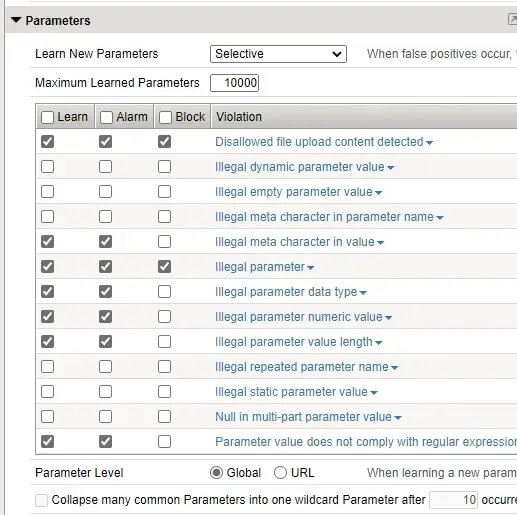
- Parameters
- Sessions and logins
- Cookies
- Headers etc.
WAF is enabling the signatures that an application is using like below.
WAF is also protecting your application from all the known Evasion techniques.
With a next-generation firewall, you are not able to provide security like WAF mostly in terms of FileTypes used and parameters, URLs used by the application.
With any next-generation firewall, you are not able to control the HTTP Compliance ( validation checks that the system performs on HTTP requests to ensure that the requests are formatted properly.) but with WAF you are able to control this.
📗FAQ
What are the 8 types of firewall?
The 8 types of firewall include packet-filtering firewall, stateful inspection firewall, circuit-level gateway firewall, application-level gateway firewall, next-generation firewall, software firewall, hardware firewall, and cloud-based firewall.
What are the 2 main types of firewall?
The two main types of firewall are software firewall and hardware firewall. Software firewalls are installed on a computer and provide protection for that specific device, while hardware firewalls are physical devices that are installed between a network and the internet, providing protection for the entire network.
What is a firewall and its types?
A firewall is a security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules.
The main types of firewall are packet-filtering firewall, stateful inspection firewall, circuit-level gateway firewall, application-level gateway firewall, next-generation firewall, software firewall, hardware firewall, and cloud-based firewall.
Which type of firewall is most common?
The most common type of firewall is the packet-filtering firewall. It is also the most basic type of firewall and examines the header of each packet to determine whether it should be allowed or blocked.
What are 3 common firewall designs?
Three common firewall designs are single-layer, two-layer, and three-layer. Single-layer firewalls are basic packet filters that operate at the network layer.
Two-layer firewalls combine packet filtering with application-level filtering. Three-layer firewalls include additional layers for proxy services and content filtering.
What are the 3 methods of firewall?
The three methods of firewall are packet filtering, proxy service, and stateful inspection. Packet filtering examines the header of each packet to determine whether it should be allowed or blocked.
The proxy service examines the application-level data in addition to the header. Stateful inspection combines both packet filtering and proxy service.
What is the strongest type of firewall?
The strongest type of firewall is the next-generation firewall. It combines packet filtering, application-level filtering, intrusion prevention, and deep packet inspection to provide advanced threat protection.
What type of firewall is VPN?
A VPN is not a type of firewall, but it can be used in conjunction with a firewall to provide additional security. VPNs create a secure, encrypted connection between two networks, which can be used to transmit data securely over the internet.
Which firewall is best?
The best firewall for a particular organization depends on its specific needs and requirements. However, next-generation firewalls are generally considered to be the most effective at providing advanced threat protection.
What type of firewall is Windows?
Windows includes a software firewall called Windows Firewall. It is a basic packet-filtering firewall that is included with the operating system.
What are the four basic firewall rules?
The four basic firewall rules are allow, deny, block, and forward. The allow rule permits traffic to pass through the firewall, the deny rule blocks traffic, the block rule discards traffic without sending a response, and the forward rule sends traffic to another destination.
What is 2 tier firewall?
A two-tier firewall is a network security architecture that consists of two firewalls, one placed at the perimeter of the network and another within the network. The external firewall filters incoming traffic, while the internal firewall filters outgoing traffic.
What is the safest firewall?
The safest firewall is one that is properly configured and regularly updated to protect against the latest threats. Next-generation firewalls are generally considered to be the most effective at providing advanced threat protection.
What is the simplest firewall?
The simplest form of firewall is a basic packet-filtering firewall. It examines the header of each packet to determine whether it should be allowed or blocked.
What is the simplest form of firewall?
The simplest form of firewall is a basic packet-filtering firewall. It examines the header of each packet to determine whether it should be allowed or blocked. This type of firewall is relatively easy to configure and does not require a lot of resources to operate.
What are the 7 layers of a firewall?
There are no specific “layers” of firewall, but the Open Systems Interconnection (OSI) model can be used to describe the different functions that a firewall may perform.
These layers include the physical layer, data link layer, network layer, transport layer, session layer, presentation layer, and application layer.
How do firewalls work?
Firewalls work by monitoring and controlling incoming and outgoing network traffic based on predetermined security rules. They examine the headers and content of network packets to determine whether they should be allowed or blocked.
How many firewalls should be there in the network?
The number of firewalls that should be used in a network depends on the network’s size and complexity, as well as its security requirements. In general, it is recommended to use at least two firewalls for added security.
What is an IP firewall?
An IP firewall is a type of firewall that filters network traffic based on IP addresses. It examines the header of each packet to determine whether it should be allowed or blocked based on the source and destination IP addresses.
What are the four common firewall architectures?
The four common firewall architectures are single-layer, two-layer, three-layer, and multi-layer. These architectures differ in the number of layers of protection they provide and the types of security mechanisms that they use.
What firewalls do large companies use?
Large companies may use a variety of firewall technologies, including hardware firewalls, software firewalls, and cloud-based firewalls. Next-generation firewalls are increasingly popular due to their advanced threat protection capabilities.
What the firewalls Cannot protect against?
Firewalls cannot protect against all types of cyber threats, including social engineering attacks, zero-day exploits, and internal threats such as employee negligence or malicious insiders.
What is the oldest type of firewall?
The oldest type of firewall is the packet-filtering firewall. It has been in use since the early days of the internet and is still a widely used technology today.
Can a VPN bypass a firewall?
A VPN can be used to bypass some types of firewalls, particularly those that use packet filtering. However, some firewalls may be configured to block VPN traffic.
Can hackers get through firewall?
Hackers may be able to get through a firewall if it is not properly configured or if there are vulnerabilities in the firewall software or hardware. However, firewalls can still provide a significant level of protection against cyber attacks.
Do I need a VPN if I have a firewall?
A VPN can provide additional security and privacy beyond what a firewall can offer. While firewalls can block incoming and outgoing traffic based on predetermined rules, a VPN can encrypt traffic to protect it from interception and analysis.
Can a firewall Stop Viruses?
Firewalls can provide some protection against viruses by blocking incoming traffic from known malicious sources. However, they are not effective at detecting or removing viruses that are already present on a system.
Is A firewall better than a router?
Firewalls and routers serve different functions in network security. Routers are used to direct network traffic between different networks, while firewalls are used to monitor and control that traffic based on security rules. Both are important for network security, but they serve different purposes.
Is antivirus a firewall?
Antivirus and firewall are two different types of security software. Antivirus software is used to detect and remove malicious software, while firewalls are used to monitor and control network traffic based on security rules.
Do I need Windows Firewall if I have antivirus?
Windows Firewall can provide an additional layer of protection beyond what an antivirus program can offer. While antivirus software is designed to detect and remove malware, Windows Firewall can block incoming traffic and prevent unauthorized access to your computer.
Do all operating systems have a firewall?
Most modern operating systems include a built-in firewall, including Windows, macOS, and Linux. However, the level of protection provided by these firewalls may vary depending on the operating system and the specific configuration.
Does Microsoft have a firewall?
Yes, Microsoft includes a firewall called Windows Firewall in its Windows operating system. It is a basic packet-filtering firewall that can be configured to block incoming traffic and prevent unauthorized access to your computer.
What should be the first rule in a firewall?
The first rule in a firewall should be a deny-all rule, which blocks all incoming and outgoing traffic by default. This ensures that only traffic that is explicitly allowed by the firewall rules is allowed to pass through.
What is first rule in firewall?
The first rule in a firewall should be a deny-all rule, which blocks all incoming and outgoing traffic by default. This ensures that only traffic that is explicitly allowed by the firewall rules is allowed to pass through.
What is level 7 firewall rule?
A level 7 firewall rule, also known as an application-level rule, is a rule that is applied at the application layer of the network stack. It examines the content of network packets to determine whether they should be allowed or blocked based on the specific application that is being used.
What are the three security zones firewall?
The three security zones in a firewall are the DMZ (demilitarized zone), the internal network, and the external network. The DMZ is a neutral zone that separates the internal and external networks and is used to host public-facing services such as web servers.
Can I have two firewalls on the same network?
Yes, it is possible to have two firewalls on the same network. This is known as a dual firewall configuration and can provide additional security by adding an extra layer of protection between the internal network and the external network.
What is a Layer 3 firewall rule?
A Layer 3 firewall rule is a rule that is applied at the network layer of the network stack. It examines the source and destination IP addresses of network packets to determine whether they should be allowed or blocked based on the network topology.
What is the biggest problem with a firewall?
The biggest problem with a firewall is that it can provide a false sense of security. While firewalls can provide some protection against cyber threats, they are not foolproof and can be bypassed if they are not properly configured or if there are vulnerabilities in the firewall software or hardware.
Do I need a firewall if I have a router?
A router can provide some basic protection against cyber threats by blocking incoming traffic from the internet. However, a router does not provide the same level of security as a firewall and may not be sufficient for organizations that need to protect sensitive data.
What is the most deployed firewall?
The most deployed firewall is the next-generation firewall. It combines advanced threat protection capabilities with traditional firewall functionality, making it an attractive option for organizations that need comprehensive network security.
What is the best firewall and why?
The best firewall for a particular organization depends on its specific needs and requirements. However, next-generation firewalls are generally considered to be the most effective at providing advanced threat protection.
Conclusion
There are 9 major types of firewalls and it is very difficult to decide which one you should be going for in order to maintain the security.
If you want a minimal performance impact, you should be going for simple packet filtering or a circuit-level gateway.
Suppose you need a great amount of protection. In that case, you should be using a proxy or next-generation firewall that will have a much bigger impact on your performance with continuous interferences.
It is all about the need of the hour, and according to that, you should be going for a firewall. No matter which one you go for, you will be able to maintain a great level of security regarding your information which might not be possible otherwise.
When you have a firewall, your network will become very difficult to track no matter how hard one tries to get it.