It is critical to stay updated on the newest trends and breakthroughs in cybersecurity if you work in the area or want to pursue a career in this vital field. Hence we present you with some of my favorite cyber security blogs to keep up with.
Depending on your immediate needs, you will find one or a few of these blogs very insightful. I subscribe to these and have found the resources a timely aid in my computing journey.
Without much ado, let’s get to it!
Best Cyber Security Blogs To Follow 👌👌
1. Schneier on Security
This highly readable collection includes some of the most informative and insightful coverage of the weaknesses and strengths of cybersecurity, as well as the price we pay — both literal and figurative — when protection fails.
Schneier on Security blog contains valuable suggestions from the world’s best computer security professionals. It is one of the most interesting cyber security blogs to keep up with the latest information.
This blog is a must-read for everyone who appreciates security at any level, technical, business, or personal. It discusses airlines, passports, ID cards, voting machines, cameras, Internet banking, passwords, computers, sporting events, and castles.
Bruce Schneier, the publisher, has been compared to a pop star in the security sector. He is known as a remarkably open and straightforward security critic and pundit. He is an internationally famous security professional.
He has published articles and discourses that have appeared in countless notable publications. Bruce Schneier has testified before Congress on cybersecurity.
He is the successful writer of eight books, including Secrets and Lies and Applied Cryptography; Wiley published, Beyond Fear, with Springer-Verlag as its publisher.
2. The Hacker News
With practically every company globally being on the internet in some form, actions must be made to guarantee their networks stay safe and secure, which is precisely what The Hacker News is all about.
Hacker News (THN) is a prominent, well-respected, and well-known cybersecurity news source with over 8 million monthly readers.
These readers include IT professionals, hackers, researchers, technologists, and hobbyists. This is clearly among the most popular cyber security blogs.
You will find the most up-to-date cybersecurity information and in-depth articles on present and future Infosec developments and how they affect the online world at Hacker News.
Paul Graham created THN in 2010 as a specialized cybersecurity and cybercrime news portal to educate everyone about using the internet safely. Y Combinator currently owns Hacker News.
In the years since, the blog has become one of the most critical data security channels, connecting a diverse group of people, including significant security academics, geeks, techies, corporations, CISOs, and hundreds of security experts.
In addition to online meetups, seminars, and gatherings, Hacker News hosts conferences, in-person meetups, and events that draw the most excellent IT experts and hackers from around the world.
The Hackers Conference is an annual gathering of motivated minds in cyberspace held in Delhi, India’s capital.
The Hackers Conference is a one-of-a-kind event where the most competent people in IT, hacking, and the digital community comes together to solve the most pressing cybersecurity issues.
3. Dark Reading
The site is among the most prevalent cybersecurity news sites on the internet. It has become one of the most reputable online communities for security experts like you.
Many other security experts and thought-leading security professionals, CISOs, and tech specialists are Dark Reading community members.
This is the place for enterprise security workers and decision-makers to keep up with the latest cyber threats, flaws, and technological developments.
Because of the caliber of professionals on this site, we recommend it as one of the top cyber security blogs.
It is where they talk about possible countermeasures to the most recent assaults and crucial technology and practices that could help safeguard their most critical data in the future.
It is where they gather to discuss fresh (and enormous) ideas with each other and with the Dark Reading editors, as well as get solutions to crucial IT security queries and fix their most important problems.
Threat Intelligence, Application Security, Attacks & Breaches, Careers and People, Endpoint, Cloud Security, IoT, Operations, Mobile, Perimeter, Risk, Physical Security, Analytics, and Vulnerabilities and Threats are among the 12 divisions of Dark Reading.com.
Editors and technical experts run each community, collaborating with security professionals, software developers, market analysts, and many other Dark Reading members to deliver timely, comprehensive, and insightful articles that spark lively debate.
Dark Reading’s mission is to encourage community participants to consider security in new ways by providing solid and unorthodox points of view supported by scientific reporting.
Their hands-on expertise and the technical understanding from years of digital forensics work make them an anchor point for the readers.
The team wants you to be a member of the community. Live chats, surveys, story discussions, radio broadcasts, newsletters, reader-generated discussion boards, and other interactive features are all free to participate in.
You will also be invited to live gatherings to further your discussions with the Dark reading crew in person.
Sign up for free to participate in the conversation and use all of the site’s features. Please get in touch with the editors if you want to learn more about what you can do to help.
Their team is continuously searching for market thought leaders who want to share their thoughts on IT protection and its role in the workplace.
4. Darkowl
Do you want to learn more from your browser’s convenience about monitoring, searching, and investigating information from historical and current darknet sites? Darkowl is one of the cyber security blogs to consider.
A group of data nerds with experience in dark web investigation and open-source data runs DarkOwl.
DarkOwl was created in 2016 and is the world’s premier source of DARKINT TM, darknet information, and the most extensive commercial darknet material database.
DarkOwl helps law enforcement, cybersecurity, and government organizations completely understand their security situation and detect and mitigate any breaches and infractions of the law. The blog provides several ways for you to get access to their data.
Their objective is to be the world’s premier darknet intelligence information supplier and give their clients the tools they need to use their data successfully and efficiently.
These clients can increase their cybersecurity defenses by giving them the tools they need to search the darknet securely.
When data is at risk, every second counts, companies can use our API, SaaS, or Data Feed to identify specific data and set up monitoring that warns them when their data is identified.
When information is breached, making informed yet timely decisions about mitigation and disclosure techniques is mainly determined by the severity of the stolen data and its time to identify the breach.
Firms can make quick, effective, and intelligent decisions by decreasing the timeframe to detection with DarkOwl Vision, putting them back in control.
5. Packet Storm Security
Ken Williams established the Packet Storm Security site, Kroll O’Gara in 1999 and then returned to the security world a little over a year later.
Mixter won $10,000 in a whitepaper competition to prevent distributed denial of services threats while at Kroll O’Gara. They now provide various professional services, and their website is cited in hundreds of books.
Individual Internet users, organizations, and governments must be aware of flaws that may damage their platforms in these times when a new significant breach happens regularly.
Packet Storm delivers information and resources 24 hours a day, seven days a week, to help prevent both private data and financial loss on a global scale.
Hence, if you seek cyber security blogs for current news, choosing Packet Storm wouldn’t be a bad idea.
Packet Storm publishes new information as soon as it becomes available via Twitter, RSS feeds, and Facebook. The website has been mentioned in hundreds of books and has previously been featured in the news.
Sun Tzu, an old Chinese military strategist, said: “I believe that if you know your enemy and yourselves, you would never be beaten in a hundred fights. When you do not know who your opponent is but know yourself, you have an equal chance of losing or winning.
You will be vanquished in every war if you are uninformed of your adversary and yourself.” This axiom pertains to today’s modern website’s battlefield, as has to all of humanity’s long and strife-filled history’s battlefields.
Security is everyone’s responsibility in today’s environment. Both parties share accountability for the firm’s safety, whether you are a chief engineering executive or an administrator.
If you are implementing third-party software in a PCI-compliant environment, looking up exploits and warnings may reveal a negative track record for flaws, causing you to reconsider your decision.
If you are contracting to a firm with many security breaches in the last five years, looking through their history news feeds will reveal their problems.
The whitepapers area can help you create a web app and learn about attack patterns, vectors, and mitigation approaches. If you are doing a vulnerability scan for a client, the devices and exploits sections will provide you with the most up-to-date information.
Since 1998, Packet Storm has been a staple of the Web, with over 190 countries visiting each month. The site is designed to offer everyone on the Web a one-of-a-kind service by throwing light on real-world security issues affecting them.
Network managers who need to maintain their networks up to date, security professionals who discover and publish new findings, and organizations and governments that need to comprehend current developments participate and contribute to the world’s security.
Packet Storm started a bug bounty program in 2013 to buy functional exploits and then offer them back to society for testing.
Later that year, they collaborated with a security specialist to help disclose a large-scale shadow account problem on Facebook. Following Facebook’s allegation that just 6 million individuals were affected, Packet Storm’s tests revealed incorrect figures.
6. Threatpost
Threatpost is a long-term, objective source of cyberspace information and analysis, covering anything from current events to threat analysis to malware and risk analysis to long-term trends.
Threatpost is your go-to source for current security news, discussions, and analysis worldwide.
This Woburn, Massachusetts-based publication reaches a core fan base of 1 million online visitors each month, comprising hundreds of thousands of business security and IT experts worldwide.
Security news, podcasts, videos, eBooks, roundtables, webinars, Q&As, insider columns, polls, feature reports, and more are all produced by Threatpost’s award-winning editorial board. The Editorial Team of Threatpost is made up of six people. This includes the following:
Tom Spring as Editor-in-Chief: Tom Spring spent three years in the editorial team at CRN magazine, where he reported breaking IT events and Dell, Microsoft products and services, Intel, and IBM.
Tara Seals as Senior Editor: Tara Seals has over 20 years of expertise in the communications and technology industry as a writer, editor, and analyst.
Lisa Vaas as Senior Editor: As a reporter, executive editor, podcaster, and public speaker, Lisa Vaas has created content about technology since 1995.
Becky Bracken as News Contributor and Webinar Editor: Becky is a tech reporter and editor with over 20 years of expertise in quantum computing, cybersecurity, quantum computing, telecommunications, artificial intelligence, net neutrality, artificial intelligence, and public policy.
Leading news publications, including The New York Times, MSNBC, The Wall Street Journal, National Public Radio, and USA Today, have cited Threatpost as a reliable information security source.
So you can feel confident in choosing the site as one of your go-to cyber security blogs.
7. SANS Internet Storm Center
Based on the successful identification, analysis, and general alerting of the public of the Li0n worm in 2001, the ISC was formed.
Scores of Internet users and businesses benefit from the ISC’s free monitoring and warning services, and the ISC is actively collaborating with Service Providers to combat the most aggressive attacks.
Remote monitoring sensors worldwide recorded a rise in the number of queries to port 53, which serves the Domain Name Service, on Mar 22, 2001.
So many more probes to port 53 began arriving for a few hours, starting from a few dozen to hundreds of hostile machines.
Numerous analysts, fully qualified as SANS GIAC accredited intrusion detection specialists, confirmed that a global security issue was ongoing within less than an hour of the first warning.
They instantly sent an alert to a global network of technically adept security professionals, requesting that they verify their systems to determine if they had been hacked.
Within three hours, a Dutch system administrator reported that several of his computers had been attacked, and he gave the researchers the first duplicate of the worm software.
The researchers figured out what the malware did and how it performed it, then created a computer program to determine which systems were infected. They ran the malware through many locations and alerted the FBI to the attack.
The researchers were able to issue a warning to 200,000 people in less than fourteen hours after the surge in port 53 activity was initially spotted, informing them of the operation in motion, telling them where to acquire the tool to check their workstations, and counseling them on how to prevent the worm.
The Li0n worm displayed what a community working together can accomplish in the face of widespread hostile attacks. Most significantly, it proved the importance of exchanging real-time intrusion prevention logs.
The assault was only visible in global and regional averages. The SANS Institute’s (CID) Consensus Incident Database program has been tracking global Internet activity since November 2000. The technologies, networks, and people that discovered the Li0n worm were all part of that initiative.
CID’s participation on that night of Mar 22 earned it a new moniker: the SANS Internet Storm Center.
The Internet Storm Center receives millions of intrusion prevention record data from devices in over 50 countries, spanning approximately 500,000 IP addresses each day.
It is continuously increasing to improve its ability to locate new storms earlier, identify offensive sites, and provide authoritative statistics on the types of assaults being waged against machines in various businesses and regions worldwide.
The Internet Storm Center is a free service that the online community can use.
The work is funded by the SANS Institute, which receives funding from students enrolled in SANS security educational programs.
Volunteer handlers offer their time to investigate and detect irregularities, and they keep a daily journal of their findings and comments on the Storm Center website.
SANS Internet Storm Center is one of the most prominent and useful cyber security blogs.
8. SecurityWeek
The objective of SecurityWeek is to deliver current news, info, opinions, analysis, and insights from the frontline of internet and business security. Regular posters who can devote themselves to a weekly or bi-monthly schedule have opportunities.
The blog welcomes you to provide a writing preview to help us assess if you would be a good fit and enthusiastic and have the expertise and capacity to write frequently.
SecurityWeek will be one of your go-to cyber security blogs if you seek current news.
SecurityWeek is on the lookout for Internet Security horror stories. Real-life scenarios that you, your organization, or your customers have faced. You either succeeded or failed. You have learned something important that you are now passing on to others.
Internet security specialists who work and live in the IT security community and deal with challenges daily write SecurityWeek pieces.
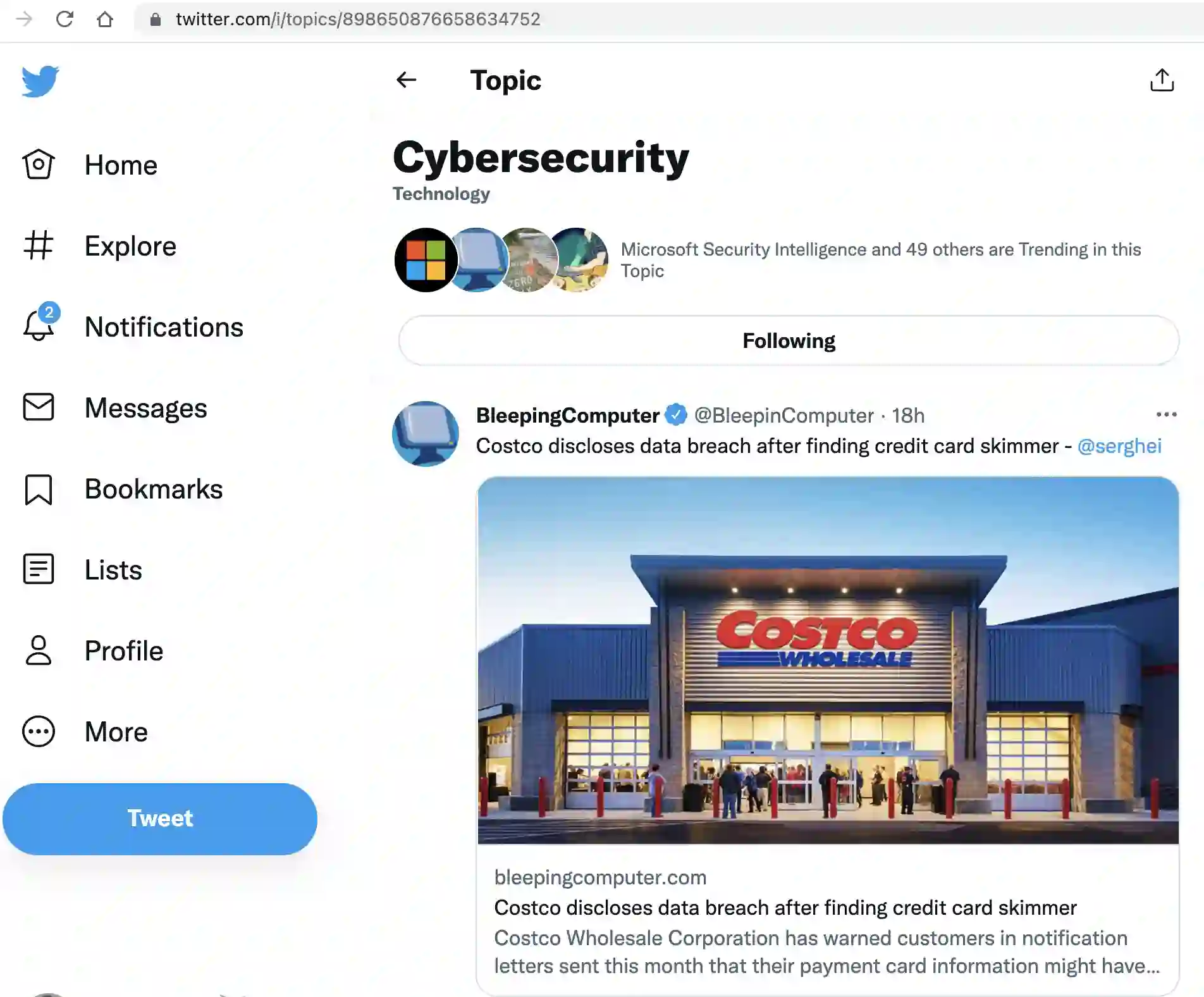
9. BleepingComputer
Lawrence Abrams founded Bleeping Computer® in 2004 as an internet security and tech news site. Each month, millions of people visit BleepingComputer.com to read about the newest security dangers, technology news, methods to be safe online, and how to get the most out of their devices.
This initiative began in 2016 as a collaboration involving the Netherlands Police’s National High Tech Crime Unit, Europol’s European Cybercrime Centre, and McAfee to combat ransomware.
Aside from news, the blog offers various free technical assistance services, downloads, and self-tutorial resources to help users fix computer problems.
Whether you are a beginner looking to understand the basics of computers or an advanced user afflicted by malware, BleepingComputer can help you solve your problem for free.
Finally, the blog aspires to transform your computer, which never accomplishes everything you want, into an efficient device you admire.
Bleeping Computer aims to deliver up-to-date and reliable information on the newest cyber threats and technological advancements so that you can secure and govern your devices, network, and data.
Bleeping Computer welcomes news reports and studies that you think their readers would find helpful as a part of that effort to help you control your data and gadgets.
For beginners, Bleeping Computer is among the cyber security blogs we recommend.
10. Graham Cluley
Graham Cluley is a cybersecurity blogger, analyst, podcaster, and public intellectual who has won numerous awards. His blog might be one of the smallest cyber security blogs discussed in this article, but it is fascinating.
Since the early nineties, while he was engaged as a programmer, Graham Cluley has been a popular figure in the internet security sector, having written the first-ever edition of Dr. Solomon’s Antivirus Toolkit for Microsoft Windows.
Graham Cluley has conducted computer security speeches for some of the top global corporations, collaborated with security agencies on hacking gang inquiries, and often appears on television and radio to discuss potential computer threats.
In 2011, Graham Cluley was named to the Cybersecurity Europe Hall of Fame. His specialties are computer security, social media, public speaking, media relations, blogging, and pedantry.
11. Gizmodo
Gizmodo is an online publication dedicated to design, tech, science, and sci-fi. Gizmodo also has a futuristic subsite called io9. G/O Media, a private equity corporation operated by Great Hill Partners, now owns Gizmodo.
Peter Rojas, who later started Weblogs, Inc.’s similar tech blog, Engadget, was the original editor of the site, which was started in 2002.
By the middle of 2004, Gizmodo and Gawker were pulling in around $6,500 each month in combined earnings.
VNU and Gawker Media developed a partnership in 2005 to republish Gizmodo throughout Europe. VNU translated the articles into French, Dutch, German, Italian, Spanish, and Portuguese and introduced local European-interest material.
Mediagene created Gizmodo Japan in 2006, which added Japanese material to the website.
Allure Media published Gizmodo Australia in April 2007, with more Australian material under authorization from Gawker Media. Gizmodo has become one of the most widespread cybersecurity blogs.
12. Project Zero
Project Zero was founded in 2014 by a group of Google security experts who explore zero-day flaws in the software and hardware systems that users worldwide rely on. It is undoubtedly one of big firms and organizations’ most significant blogs.
The website’s goal is to make it harder to find and use security flaws and significantly improve the security and safety of the internet for all.
Project Zero looks for flaws in widely used software such as web browsers, mobile operating systems, and open-source libraries. The site uses the findings of this study to repair critical security flaws, enhance our knowledge of how exploit-based assaults work, and promote long-term fundamental security measures.
After discovering a lot of holes in software, such as the grave “Heartbleed” weakness, Google decided to create a full-time team committed to detecting similar defects in all software used by its customers, not only Google products.
The new initiative was unveiled on Google’s security blog on Jul 15, 2014. One of Project Zero’s main breakthroughs when it first began was a tight 3-month vulnerability disclosure timeline and a publicly available bug tracker where the flaw disclosure procedure is documented.
While the concept for Project Zero dates back to 2010, its implementation fits into a broader pattern of Google’s counter-surveillance measures in the aftermath of Edward Snowden’s intelligence-gathering exposures in 2013.
Before joining Tesla Motors, Chris Evans, formerly the director of Google’s Chrome security department, led the team.
Cybersecurity experts Ben Hawkes, Ian Beer, and Tavis Ormandy are among the other famous members. Hawkes subsequently rose through the ranks to become the team’s manager.
The team aims to uncover defects and new assaults and explore and openly publish how such flaws might be manipulated in practice.
This is done to ensure that the defense knows about attacks; the crew maintains an extensive study blog with articles that outline specific attacks.
Bugs discovered by the Project Zero team are communicated to the manufacturer and publicly disclosed after a fix has been provided or after 90 days without a solution.
The three-month is Google’s method of adopting responsible disclosure. Software businesses are given 90 days to correct a vulnerability before telling the public, allowing users to take the required precautions to avoid assaults.
There have been instances where the vendor failed to provide a solution for found weaknesses within 90 days of being told, before the team’s public announcement, leaving users of exploited systems vulnerable.
One of the earliest Project Zero reports gaining traction was a weakness in the Safari browser that enabled hackers to take over the software. Apple thanked the team, notably Beer, for their work in a brief note.
Google discovered a software bug in Windows 8.1’s system called “NtApphelpCacheControl” on Sept 30, 2014, which permits a regular user to get administrator access.
Microsoft was aware of the problem right once, but it did not resolve it within 90 days; therefore, knowledge about the flaw was publicly disclosed on Dec 29, 2014. Microsoft responded by saying they were trying to fix the problem once the weakness was made public.
On Mar 9, 2015, a feature article on Google Project Zero’s site revealed how a previously identified hardware issue known as Row Hammer could be used to elevate rights for local users.
This article sparked a slew of follow-up studies in both the hardware and academic communities.
On Feb 19, 2017, Google uncovered a weakness in Cloudflare’s reverse routers that led its data centers to go past the end of a cushion and return memory containing sensitive data like authentication tokens, HTTP cookies, and HTTP POST contents.
Search engines stored some of this information. Cloudbleed was the name given to this issue by one of the Project Zero team members.
Project Zero’s Tavis Ormandy uncovered a flaw in the famous password company LastPass on Mar 27, 2017. LastPass reported that the issue had been resolved on Mar 31, 2017.
Meltdown and Spectre bugs impacting many modern CPUs were found mid-2017 and published in early January 2018. Project Zero was instrumental to their discovery.
Jann Horn identified the security hole independently of the other experts who disclosed it, and it was originally slated to be released on Jan 9, 2018. Still, the date was moved early due to increased speculation.
On Apr 18, Project Zero uncovered an issue in Apple iMessage that caused Springboard to “…crash and frequently resurrect, leading the UI not to be shown and the phone to fail to respond to commands.”
The iPhone’s Interface would entirely crash, rendering it unusable. Even after a hard reset, the problem would continue. On the Mac, the issue also disrupted iMessage, with varying outcomes. Before Project Zero was released, Apple rectified the flaw within 90 days.
Project Zero disclosed to Apple on Feb 1, 2019, that they had discovered a set of five independent and entire iPhone attack chains impacting iOS 10 across all iOS 12, with the capacity to infiltrate any user who browsed an affected site.
Project Zero estimated that a series of compromised sites were being utilized in arbitrary watering hole assaults on their visitors, with thousands of visitors every week.
According to Project Zero, the attacks suggested a group that had been hacking iPhone users in specific societies for about two years.
Apple resolved the exploits in iOS 12.1.4, released on Feb 7, 2019, and says the remedies were in the works when Project Zero disclosed them.
13. Twitter
I know you are thinking about why I put the name of Twitter on the cyber security blog list. Don’t worry, I am going to explain you.
Twitter is one of the best places to follow any topic of your interest; in this case, our topic is cyber security.
To follow the cyber security topic, either go to your profile and select the Topic option and search for “Cyber Security” and follow it or visit this link and follow the cybersecurity topic.
In the same way, you can follow other topics of interest on Twitter to get the latest information about the topic.
📚FAQ
What are the 5 types of cyber security?
Cybersecurity comes in a variety of forms, but some of the more popular ones are as follows:-
Network security: This protects a computer network from intruders, attacks, and other dangers.
Application security: This entails defending specific applications and the data they process against various dangers.
Endpoint security:- Protecting devices connected to a network, such as laptops, smartphones, and tablets, is known as endpoint security.
Data security:- Data security protects data against unauthorized use, access, disclosure, disruption, alteration, or destruction.
User security:– Protecting users and their accounts from illegal access and attacks is part of maintaining user security.
In general, the goal of cyber security is to guard against unwanted access to or compromise of networks, devices, and data.
How do I write a cyber security blog?
Here are some actions you can do to write a cyber security blog:-
Before beginning your blog, you must decide who you are writing for. Identify your target audience. You may use this better to adapt your content to their needs and interests.
Select a subject: Knowing your target audience will help you select a pertinent and engaging topic. You can look into the hottest issues in the cybersecurity sector and choose one that appeals to you.
Investigate your subject: It’s critical to do your research after selecting a topic to make sure you are knowledgeable about it. This will assist you in producing accurate and insightful blog content.
Create an outline:- Outlining the key points you want to make in your blog article before you begin writing can be useful. You can better organize your ideas and stay on topic if you do this.
Research your topic:- You may begin writing your blog article after creating an outline. To make your views more understandable to your audience, write in the clear, succinct language and back them up with examples and rationale.
Proofread and edit your message: After you’ve finished writing your blog article, it’s crucial to go back and thoroughly edit and proofread it to ensure there are no mistakes and that it flows well. You might also ask someone else to review it and offer their opinion.
Release your article: Your blog article can be published on your website or blog once it has been revised and proofread. You can also post it on social media and other platforms to promote it and reach a larger audience.
Who is number 1 in cyber security?
Since so many people and institutions are industry leaders, it is challenging to identify the top cyber security provider.
Top players in the cyber security market include corporations like Symantec, McAfee, and Kaspersky and governmental organizations like the National Security Agency (NSA) and the Federal Bureau of Investigation.
Where to read cybersecurity blogs?
There are many places where you can read cyber security blogs, including online publications and websites focusing on cyber security news and information.
Some popular websites where you can read cybersecurity blogs or cyber security news sites include:-
Dark Reading (https://www.darkreading.com/)
Security Boulevard (https://securityboulevard.com/)
Krebs on Security (https://krebsonsecurity.com/)
Naked Security (https://nakedsecurity.sophos.com/)
SecurityWeek (https://www.securityweek.com/)
Additionally, many cybersecurity companies and organizations have blogs where they share news, covering cybersecurity blog topics, updates, and information about their products and services.
You can also search for cyber security blogs on search engines like Google or Bing to find many articles and posts on the topic.
Final Thoughts
Cybersecurity may appear complicated, but it is one of the most hotly debated topics in the industry. As a result, keeping up with the current developments is critical for everyone working in cybersecurity or aspiring to work.
However, there is so much information in the cybersecurity arena that it is difficult to identify which stories are important to learn about cybersecurity and keep current.
We have provided you with in-depth content in this article to aid you in selecting the best cyber security blogs for gaining knowledge and developing authority in this topic.