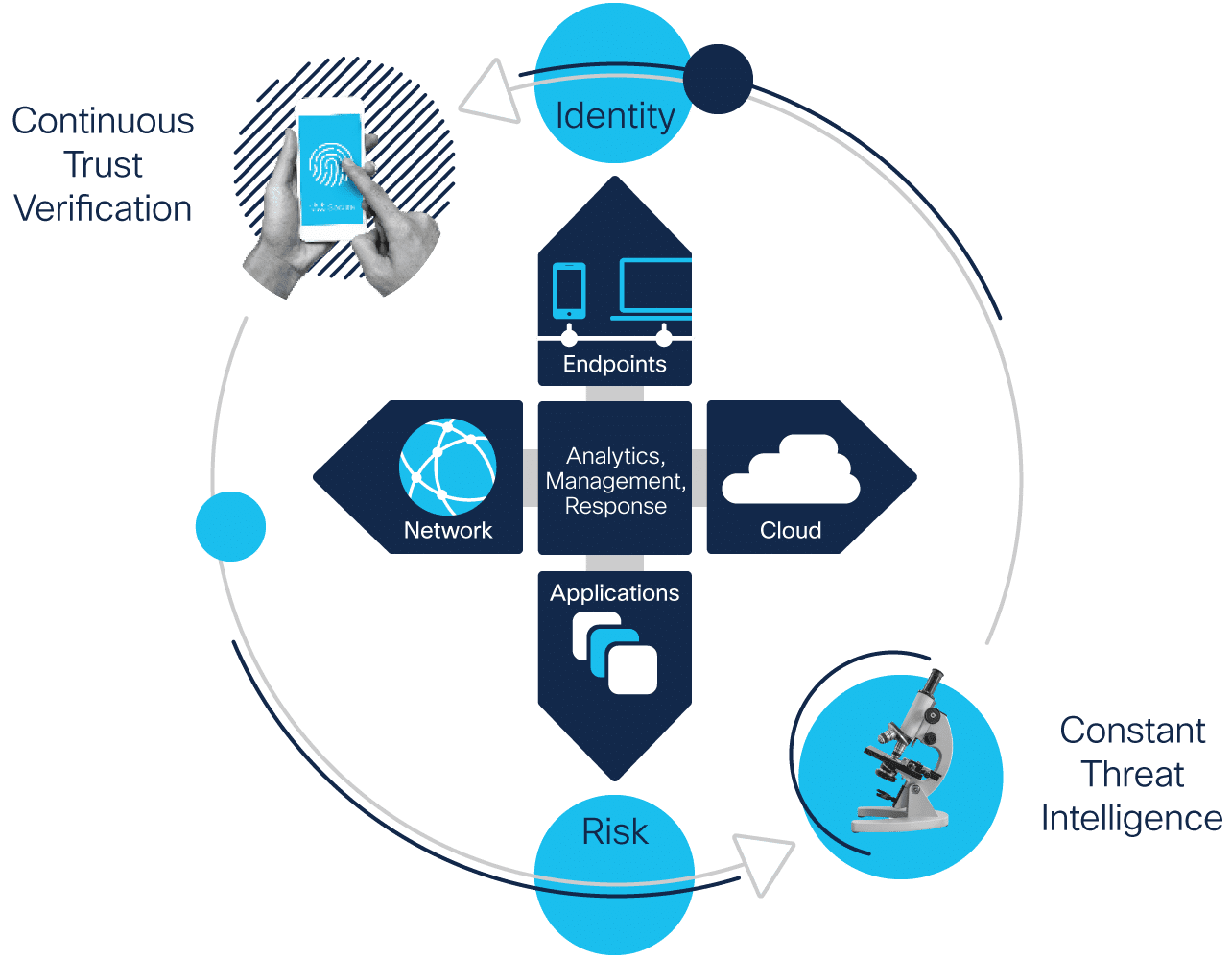
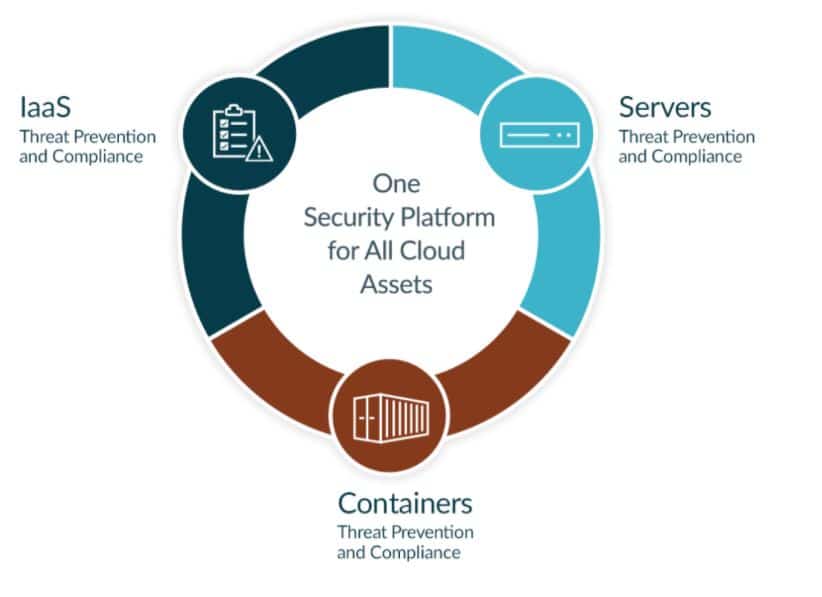
In the ever-expanding digital world, organizations that tend to store critical data on cloud servers need to leverage Cloud Security Solutions.
In recent years, cloud security has become a significant issue for various companies and organizations working on the web. In the last few years, multiple apps, businesses, and organizations have encountered privacy breaches.
Since cloud storage is economical and can be accessed from anywhere in the world, almost all organizations use cloud servers. Today, organizations store all sorts of data on their preferred cloud server, and hackers look for loopholes in their security.
Cloud security is necessary for every business on cloud servers to prevent possible attacks and data breaches.
Earlier all the data would be stored in servers with high-security measures to prevent data loss and unauthorized access from hackers.
Now, the organizations and apps are hosted on various cloud platforms, and they continuously need high-level security to keep files safe. Today, hackers are well-versed with multiple ways to escape the system security and steal data.
Companies and apps need multilayered security to avoid potential attacks on cloud services or networks. An organization may use firewalls, gateways, or cloud emails to protect hackers’ data and get leaked.
Cloud Security Solutions is a must for enhanced security and accurate predictions of possible attacks on an app, database, or gateway.
Though the data stays safe on servers, hackers worldwide keep looking for crucial data access to organizations. It’s wise for organizations to avoid using public networks and keeping a check on possible unauthorized access to accounts. Such safety measures may help organizations keep their data safe and secure on their cloud server.
There are various solutions for Cloud Security, and it includes access to different software, networking, data storage, and servers. Using cloud security keeps data stored on the web and minimizes the chances of losing the data. Moreover, cloud security is secure, reliable, and works on zero trust, which means users only access their files.
There’s a belief amongst many users that their data is safe on local storage devices, which is not true. The data kept in cloud storage is protected with the experts’ multilayered security using the best tools and technology. Moreover, the data kept in cloud storage isn’t prone to attacks from hackers using various malware.
For users, trusting a company providing cloud storage to store delicate data may be a great concern. Various independent organizations or third parties tend to audit platforms providing cloud storage for security and privacy protection.
Best Cloud Security Solutions For Businesses 👌
1. Cisco Cloud Security
Cisco Cloud Security Solutions are robust, and users can pick specific services that meet their needs. Unlike many other Cloud security providers, Cisco doesn’t bind its users to avail of all its services.
Services provided by Cisco cover almost all the aspects of cloud security, and there’s a service for all needs of users.
Cisco’s products include Cisco Umbrella, Cisco Cloudlock, Cisco Cloud Email Security, AppDynamics, and StealthWatch Cloud. Each product adds more security, safety, and makes for reliable data protection on shared or public cloud servers.
Cisco’s product comes with a free trial service that ensures users aren’t bound to use their Cloud Security Solutions.
Cloud Email of Cisco is quite impressive as it blocks out threats sent through emails and protects users’ data. The Cloud Email is safe, secure, and ensures privacy for the user at all costs. Moreover, the testing period for Cloud Email may go beyond two weeks for some users.
Pros of Cisco Cloud Security:-
1. Cisco provides users the chance to take a free trial of their products for about two weeks. Free trials give users the freedom to make their final decision after testing the services.
2. Cisco Umbrella is relatively easy to manage and has a simple user interface. The authorized users can also share access and control with selected individuals for managing the Cisco Umbrella.
3. Cisco Umbrella users don’t need to rely on additional hardware to protect their cloud servers’ data. Moreover, users also don’t need to spend endless hours updating any software to run the services.
4. Cisco Umbrella leverages DNS and IP layers of the network; it manages to block various malware, phishing, ransomware attacks. The DNS and IP layers make the umbrella a reliable Cloud Security tool users can use.
5. Cisco Umbrella detects malicious links, IP addresses, and domains and blocks them to protect the user data from attacks.
6. To claim a free trial of Products that Cisco provides, users don’t need to submit their credit card details.
7. Organizations working with workers beyond their location can rely on Cisco Cloud Security to protect their remote workers from online attacks. Cisco enables users to minimize malware from their remote worker’s devices.
Cons of Cisco Cloud Security:-
1. While reporting issues with the network or the servers and the security, Cisco Cloud doesn’t provide detailed reports. Incomplete or short reports may lead to trouble fixing or tracing the issues.
2. While the Cisco Cloud Security User interface is simple, it lacks the power to suggest things intuitively. Some users may prefer a slightly better or more intuitive UI.
2. Threat Stack Cloud Security Platform
Threat Stack Cloud Security Platform ensures that the user data stays safe from any sort of attack. The platform is quite famous for observing glitches in the user’s security and providing detailed information to users about the loopholes.
The platform can also help users conduct investigations to optimize the workflow and systems of the organization.
The Threat Stack Cloud Security Platform protects users’ cloud data and infrastructure, including various applications. The Platform’s security complexity makes it eligible for providing the best Cloud Security Solutions to its users.
The dynamic and automated nature of the platform’s security ensures quick adaptations as per the user’s needs.
The Threat Stack Cloud Security Platform doesn’t rely on traditional monitoring methods to protect users’ data from attacks. Today, the platform embraces technology and depends on observability for better safety and threat prediction.
The observability lets professionals adapt rather quickly to any changes in an organization’s application. Users opting for the Threat Stack, Cloud Security services can also detect risky behavior amongst their teammates.
Moreover, the platform can also help them detect any unauthorized entry to the systems or the network. The tracking and detection of risky behavior and unauthorized entry to systems use real-time analysis of behavior.
Pros of Threat Stack Cloud Security Platform:-
1. Whenever users make changes in their application or data on the cloud servers, Threat Stack Cloud Security Platform recognizes the change. The platform enhances user security by upscaling security and adapting to the new application or data changes.
2. The platform can help users monitor fellow users’ behavior on their team, check network security, and give controls. Moreover, users can also check the working process of sharing sensitive information and give validation.
3. The platform lets organizations foresee any possible risks from anywhere on the network. The Threat Stack Cloud Security Platform uses telemetry analytics to track risks and their context.
4. Users can also audit their cloud storage provided by AWS or Google for additional security of the user. The Threat stack gives users an overview of security and any possible threats to their cloud storage data.
Cons of Threat Stack Cloud Security Platform:-
1. The UI of the Threat Stack, Cloud Security platform, may misbehave at times, and users may find it hard to manage. Moreover, UI needs some great changes to make things smooth and change the overall user experience.
2. The pricing point of the Threat Stack Cloud Security Solutions might seem overly expensive to some users. The cost of some services provided is higher than that of their competitors.
3. Symantec Cloud Workload Protection
The Symantec Cloud Workload Protection extends support for almost every central cloud computing platform like AWS, Google, Azure, etc.
The Symantec Cloud Workload detects the increasing and decreasing resources of the user on the clouds and optimizes protection levels accordingly. Users need to install and grant permission to the tool, and it takes care of the data on cloud storage platforms.
Once Symantec Cloud Workload Protection is activated on cloud storage platforms, it begins working with three approaches. The first approach is to monitor the traffic flow and record patterns of traffic.
In the second approach, Symantec Cloud Security Solutions work to provide real-time feedback using recommendations from an engine to prevent attacks.
The third approach takes necessary actions to protect user data and privacy from attacks on the system and network. The other features of Symantec Cloud Workload Protection include zero-day threats, host-based IPS, and vulnerability protection.
Moreover, the developers can also use adapters for various Cloud Storage platforms to access them quickly and securely without risking privacy.
Since Symantec Cloud Workload Protection provides robust cloud security solutions, users can sit back and focus on their work.
The software takes care of the protection of user data and keeps attackers at bay. The user-friendly design of the software makes it easy to adapt and use for new users.
Pros of Symantec Cloud Workload Protection:-
1. While using Symantec Cloud Workload Protection, users don’t need to worry about any malware attacks on their systems, data, and networks.
The Cloud Security Solutions of Symantec are equipped with an anti-malware feature that provides real-time updates for any possible attacks.
2. The Cloud integration feature that Symantec security provides emphasizes creating a connection between the cloud service provider and the enterprise user. The integration protects the user from any chances of data loss and attacks on the system.
3. The reports about the issues with cloud computing or any software recommendations are easy to understand. Unlike many other Cloud Security Solutions providers, the reports of Symantec are not complicated.
4. The high security provided by Symantec Cloud Workload with tons of features doesn’t hamper the speed of the user’s computer.
5. The users can be sure that Symantec Cloud Workload Protection will protect their system from virus attacks, spyware, and Spam.
Cons of Symantec Cloud Workload Protection:-
1. Some users may be annoyed by multiple notifications that Symantec Cloud Workload Protection keeps sending. Sometimes, the notifications can be unnecessary and hamper the productivity of users.
2. Small and medium-sized businesses may not be able to afford the software due to its high pricing. Businesses struggling economically may have to look for cheaper options.
3. The Users seeking help from the support team of Symantec may be disappointed by the poor services provided.
4. CloudPassage Halo
CloudPassage Halo is an all-in-one provider of cloud security solutions that protect users’ Cloud Servers, Containers, and Infrastructure.
The cloud architects ensure that users don’t have to rely on multiple tools or products to manage their servers. Moreover, the cloud architect also makes it easier for users to secure their servers, containers, and laaS using the platform.
Created by professional DevOps, CloudPassage Halo is quite an unmatched tool when it comes to security, ease of management, and benefits.
Moreover, Halo Cloud Security Solutions provider doesn’t require heavy systems to run smoothly for securing users’ data. And to make things better for users, Halo works on automation to provide the best solutions.
The Cloud safety of Halo ensures that users’ infrastructure stays safe while developing new gateways and using new strategies.
Moreover, Halo tries its best to cut the user’s cost to move on digital platforms while maintaining high security. The pricing of the Halo Cloud Security services is based on the usage and needs of the users.
The simplicity of Halo makes it quite popular amongst users who don’t want complex Cloud Security Solutions. Moreover, Halo doesn’t compromise with user’s data protection.
Pros of CloudPassage Halo:-
1. Before buying the CloudPassage Halo, users can try the trial version for fifteen days without spending anything. The trial period gives users the freedom to first use and then decide if they want to continue with Halo.
2. CloudPassage Halo provides well-detailed reports that users may benefit from while passing through various audits. On the other hand, the dashboards are user friendly and make it easy to manage tasks.
3. CloudPassage Halo users could be anywhere in the world and still get connected with the support team at any hour. The platform offers great customer support twenty-four hours, seven days a week.
4. The distribution architecture of CloudPassage Halo is different from various other cloud security solutions providers. When buying the products, users don’t need to pay an additional amount as a security tax.
5. Halo scales effortlessly and automatically without the user’s intervention as the business or the users’ responsibility grows. Halo automatically begins interrogating, assessing, and monitoring any new servers when the user is expanding their cloud footprint.
Cons of CloudPassage Halo:-
1. The CloudPassage Halo doesn’t support any anti-virus for enhanced safety from URL-based attacks. Some users who can’t imagine Cloud Security Solutions without an anti-virus may have to look for other options.
2. Various features of CloudPassage Halo may not work on computers using Windows. Some features only work for Linux operating systems, and users may have to look for alternate ways to use those features.
5. PaloAlto Prisma
PaloAlto Prisma is a famous Cloud Security Solutions provider trusted by most of the fortune companies. PaloAlto Prisma provides solutions for all the cloud computing security needs of users, beginning from analytics, threat prevention, and maintaining compliance.
Moreover, users of PaloAlto Prisma can also use the platform to create cloud applications with robust security. Working in multi and hybrid cloud environments is risky as there are high chances of attacks and losing data.
However, PaloAlto Prisma makes working on hybrid and multi-cloud environments safer by providing full lifecycle security and full-stack protection. The robust safety for working on various cloud environments helps create applications without worrying about losing data or getting attacked.
Various fortune companies trust PaloAlto Prisma because the Prisma provides users unmatched security and sets the benchmark very high.
The trust of fortune companies in PaloAlto Prisma makes it reliable for various small and medium-sized organizations. Moreover, over a dozen compliance frameworks make the security for cloud-based applications even better.
To make things even better for the management and administrators, Prisma allows the administration to view reports with a single click. For enhanced cloud computing safety, PaloAlto Prisma utilizes machine learning to detect abnormal, threatful user activity.
Pros of PaloAlto Prisma:-
1. PaloAlto Prisma Cloud is capable of tracking stolen access keys, malicious user activity, and insider threats. The provider uses ML and tons of audits to detect possible threats.
2. To protect data loss from potential attacks on the user’s network, the PaloAlto Prisma monitors unusual activity on the networks. The network monitoring ensures that users can be alarmed about the port scans, sweep, and other threats.
3. Users get detailed insights into various activities on their servers, cloud storage, and user behavior. Moreover, PaloAlto Prisma automatically investigates multiple incidents. For automated response and response, the software uses reports from workload, networks, and user activity.
4. The customer assistance of PaloAlto Prisma stands out from that of its competitors. The premier support feature works best for urgent assistance from the team.
5. The PaloAlto Prisma Cloud Security Provider can be scaled effortlessly, and teams can add up to 3000 users at a time. The capacity of the software to support a massive number of users makes it great for big organizations.
Cons of PaloAlto Prisma:-
1. Some users may find the pricing of PaloAlto Prisma a bit too high than their budget. Though, it’s justified for the features and security standards that PaloAlto Prisma provides.
2. Users who may need encryption features as a part of their Cloud Security Solutions may be disappointed here. Prisma lacks encryption-based security for clouds.
6. Fortinet Cloud Security
Fortinet is a reliable and trustworthy Cloud Security Solutions provider that app developers can use to protect their user data.
Fortinet helps users develop a secure connection between the cloud servers and the data center. The users get complete control and robust security of their various cloud infrastructures and applications.
The web application security of Fortinet is designed especially for cloud computing users to provide them robust safety. The web application security works as armor for developers and protects their data from all sorts of risks and attacks.
Fortinet’s regulatory compliance is improved and better for various applications, focusing on the need for API security.
The Firewalls provided by Fortinet are beyond amazing as they ensure the users don’t fall prey to threats while browsing. The firewall makes it almost impossible for malware or hackers to get access to users’ systems.
Moreover, when Fortinet detects a threat, the software automatically addresses and fixes the faults that may arise.
Pros of Fortinet:-
1. Users can be best assured that their emails are secure and will not fall into the wrong hands. Fortinet Fabric provides transparency and control to the user to protect their emails from zero-day threats.
2. Users can set up Fortinet without requiring a lot of technical knowledge. Moreover, the users can also easily manage the software as it works on automation to fix most detected issues.
3. Fortinet can run smoothly on various operating systems, including the macOS. Moreover, users don’t also need to have high-end computers to use Fortinet Cloud Security.
4. The Technical support team of Fortinet is highly responsive and available for users globally twenty-four by seven. Users don’t need to wait for endless hours to get their issues resolved.
5. There aren’t any bugs that may hamper the speed or stability of the Fortinet Cloud Security.
6. Fortinet secures all the networks of the users without fail throughout the day. The secure network feature of Fortinet works across locations and with different IP addresses.
Cons of Fortinet:-
1. The reports provided by Fortinet Cloud Security are quite confusing and need some work to make them better. Sometimes users may not be able to understand certain points in the report.
2. Some users may find it difficult to scale their user count on Fortinet for protecting users in different locations. However, the technical support team should be able to resolve the issue. If the users are still not able to scale, they may have to look for other options.
3. Users can’t retrieve the previous data of the software, making it quite difficult for enterprises to match and detect problems.
7. CipherCloud
The CipherCloud works across sectors to provide cloud security to the users, safeguarding the public and private cloud services. Moreover, CipherCloud offers various security options through one license and without putting user security at stake.
The product can be customized as per the user’s needs, and the technical support for the product is quite promising.
Setting up the CipherCloud Cloud Security Solutions is a straightforward process and requires significantly fewer user efforts. Moreover, the support team works hard to simplify complicated steps of installation for users in no time.
The security provided by CipherCloud keeps things transparent and the user data safe with encryption on various points on the server.
The best part about CipherCloud Security Solutions is, it provides updates on various security-related issues in real-time. Whenever the software detects any possible attacks on the user’s data or cloud infrastructure, the software sends alerts.
The real-time updates let users be sure about the safety of their data stored in the cloud storage and their software’s functioning.
Moreover, CipherCloud also lets users check for any possible threats to their data or system through manual risk analysis. The manual analysis helps users understand how the software is securing their data and potential risks the users may face.
Pros of CipherCloud:-
1. CipherCloud has a robust risk detection feature that assesses various clouds for any possible safety breaches. Once a cloud becomes a suspect, the CipherCloud Cloud Security Solutions prevents users from visiting these platforms.
2. CipherCloud deploys encryption on multiple levels in the server and networks to provide enhanced safety to users. Encryption-based security is hard to crack for attackers and can be managed effortlessly.
3. Users can rely on CipherCloud Security Solutions for the safety of their cloud data. The CipherCloud keeps data from deleting or getting leaked through attacks on cloud storage.
4. Users who wish to check what CipherCloud can do for their cloud safety can avail free demo of the service. The demo doesn’t require users to use their credit cards.
Cons of CipherCloud:-
1. The product admins often may not be able to remove bugs as there’s not ample information available to remove the same. Debugging increases the admin’s reliability on the support team of CipherCloud.
2. CipherCloud charges a good amount of money for all the services that it provides to the users. Enterprises or organizations on a tight budget may want to consider cheaper options available.
8. Trend Micro Hybrid Cloud Security Solution
The Trend Micro Hybrid Cloud Security provides robust solutions for all cloud security-related needs of users. The Trend Micro Hybrid Cloud Security supports cloud platforms like AWS, Microsoft Azure, Google Cloud, and more.
The cloud migration of Trend Micro is reliable as it automatically discovers and protects various cloud environments.
Whenever the software is migrating clouds, it keeps the network security intact and avoids any attacks on the network. The secure network makes the cloud expansion effortless and quick without any risks of losing data.
Some enterprises are prone to phishing attacks, and Trend Micro Hybrid Cloud Security keeps the data of all its users safe.
The Trend Micro Hybrid Cloud Security can also encrypt files of users once they grant necessary permissions. The file encryption feature of Trend HCS protects delicate information from getting misused.
The encryption is robust, and attackers may struggle hard and still fail while attempting to read encrypted files.
Users may use Trend Micro not only to secure their applications but, they can also to secure their data. The users also get a dedicated firewall for robust safety against ransomware and malware attacks.
Moreover, Trend Micro also extends its security to various operating systems like Linux, macOS, and Windows.
Pros of Trend Micro Hybrid Cloud Security Solution:-
1. The Trend Micro Hybrid Cloud Security is flexible when it comes to providing services to the users. The users get to choose what tools they want and which platforms they wish to include in their plan. Based on the users’ choices, the software then deploys APIs and key integrations.
2. The application security provided by Trend Micro ensures that users know about possible attacks on their cloud system in advance. Application security also gives real-time protection from attackers and malware.
3. The software automatically evaluates the standard of security based on the user’s cloud architecture. The automatic evaluation helps users understand what they need to do better to meet the standards of AWS.
4. Users can also check the features of Trend Micro Cloud One without spending money. The free trial makes it easier for users to check multiple services and then choose what suits them best.
5. Users can also conduct a special analysis called root cause analysis on Linux and Windows to detect the impact of attacks.
Cons of Trend Micro Hybrid Cloud Security Solution:-
1. The Virtual Private Network, aka VPN feature of the Trend Micro Hybrid Cloud, fails to do its task perfectly. It fails to understand the complex server configuration.
2. The speed might disappoint some users of the Hybrid Cloud Security Solution. Some users may also experience a downfall in the performance of their computers.
Conclusion
Each Cloud Security Solutions Provider offers various tools and services at very different prices. Some service providers may give users the freedom to make plans as per their needs. At the same time, some others provide bundles at a specific price range.
One may not want to opt for a Cloud Security Solution that doesn’t do what the users expected from its services. It’s best that users thoroughly understand what is offered and what’s not by a Cloud Security Provider before making their decisions.