Let’s first start to know whose alternative we are searching for and what it means. Web browsing is one of the most common things we, as normal person is, do nowadays, and Google is one of the most used and known web browsers we use for browsing almost daily.
But we all know that using Google does not allow you to hide your identity and let you be anonymous. Still, one special web browser allows you to browse while remaining anonymous, and the name is Tor (The onion router) Browser.
Is Tor browsing legal or illegal? 🤷♂️
We always worry about illegal practicing, so asking whether using Tor is legal is a very legitimate question.
Let’s start clearing your hesitation. Well, browsing anonymously is illegal and used to save privacy and free use without surveillance.
Tor is used to browse the Clear web, and as the Tor Project said, “neither the network nor the browser is illegal” therefore, we can use Tor with assurance, and it is not seen as a crime to use it.
Why the need for Tor alternatives?
At the time, Tor was most used for anonymous web browsing, but after the interference of the FBI, technicians started searching for Tor alternatives.
Using Tor for anonymity is good, but allowing ISPs to have an eye over your task is not cool.
A person can use many available options in the market instead of opting for Tor.
Best Tor Alternatives For Anonymous Browsing
Well, only one option is not enough for people like us, so we present you with a vast list of Tor Alternatives so you can select from multiple choices and not just be stuck on a single choice.
If you want to browse anonymously, here are some options you can choose as a Tor alternate or do anonymous browsing.
1. Epic Privacy Browser – Alternatives to TOR browser
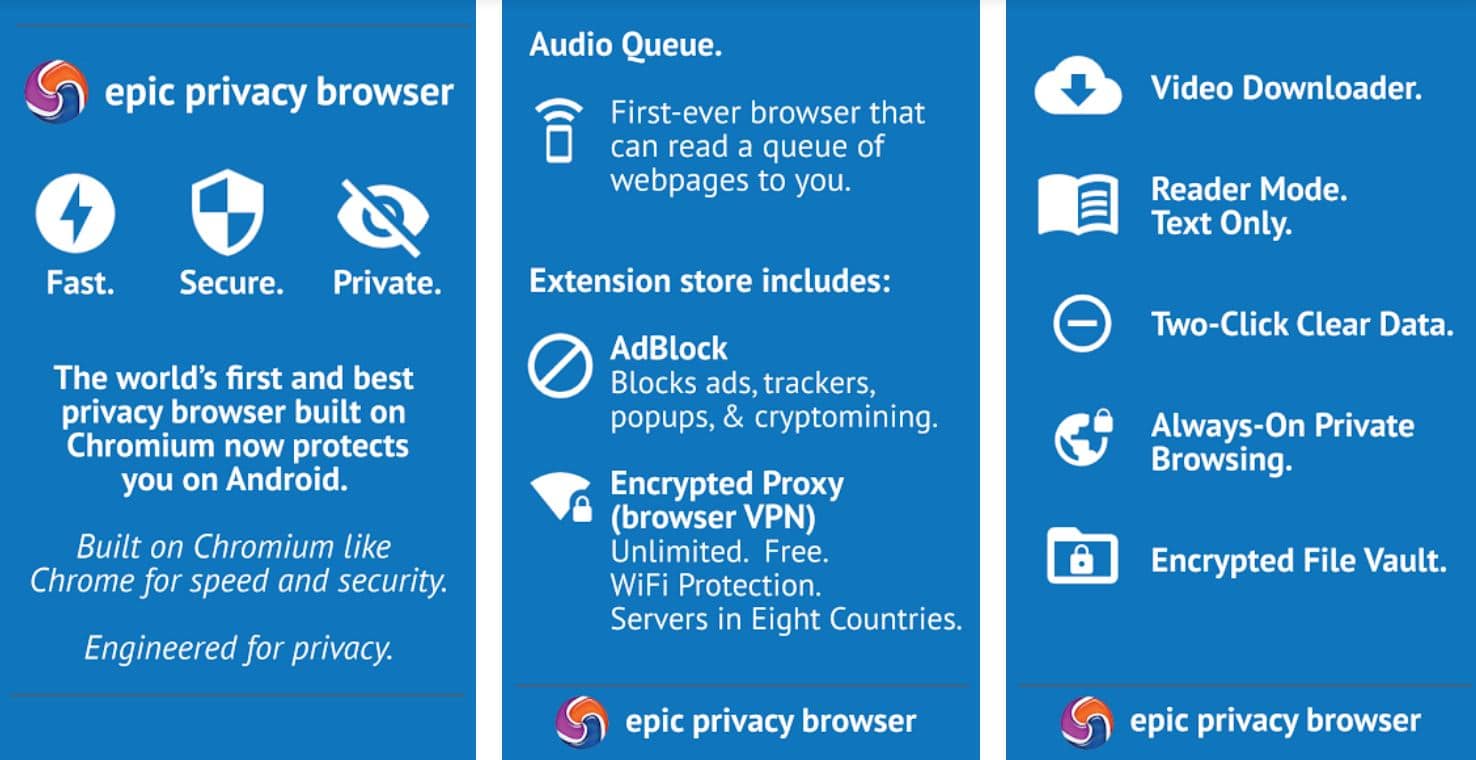
Epic Privacy Browser is the first name in our Tor alternatives list. The name defines some of the properties it offers its users.
It is a web browser that allows you to browse anonymously in the simplest manner, thus functioning in the same tasks as Tor.
Epic Privacy is one of the alternatives to Tor because its simple infrastructure is considered user-friendly. It provides variable speed consistency and gives users complete privacy while browsing.
It protects your IP address from WebRTC by its encrypted proxy and protects against data leakage. Internet Service Providers and Public networks can not access your data as EPIC does not allow them to locate your browsing.
It also allows users to block any data tracker from tracking browsing data and offers services like image canvas data.
Epic Privacy Browser is the only Tor alternative that allows you to block fingerprint scripts. Epic Privacy Browser has a special built-in that allows users to protect the data from tracking cookies, scripts, agents, ad networks, and any other dangerous third party.
When looking for Tor alternatives, the Epic Privacy Browser is the best option for any internet user.
2. Whonix
The second place in our ‘Tor alternatives’ list is taken by another best option that functions pretty well on Linux, and that Tor alternate is Whonix (Download Here). It lets the user have complete privacy over their browsing history.
Whonix works on Whonx workstation, which functions on a private framework. It runs on two different virtual systems interfaces. The two system interfaces connect with the web through NAT and a virtual LAN.
Just like the Epic Privacy Browser, Whonix also offers to wipe your IP address while web surfing, thus becoming one of the best Tor alternatives that an internet user will be benefitted from.
One of the many advantages that Whonix provides is the layers of security hence conforming the best data protection to its customers and functioning it on VM.
Hence apart from Tor and Tor’s first alternative, Epic Privacy Browser, customers can also opt for Whonix as a Tor alternative because of its features.
3. Brave Browser – Best alternatives to tor
The third place for Tor alternative goes to the most recently developed web browser as compared to other Tor alternatives, Brave Browser.
It is a web browser invented by the co-founder of the Mozilla project, Brendan Eich.
Brave Browser is one of the open-source small web browsers that function on Chromium, and one of the things they are proud of is its high security in protecting users’ privacy.
Brave Browser allows its customers to block any tracking website’s activities due to its security privacy, thus making sure its users’ identity remains anonymous over the internet while web browsing.
The third Tor alternative allows you to block any tracking websites and any advertisement search from sites, thus giving you more privacy.
A person on Android, iOS, and Windows can easily access this small compatible cross-platform Tor alternative.
Brave Browser also gives a return gift to its customer in the form of “Brave Payment.” It is a kind of system where publishers are rewarded as compensation for blocking advertisements.
We all know being partners with one of the widely used and famous search engines can also help in improving your anonymous search, so Brave Browser’s partnership provides that to you.
All the above features can help you to decide whether you want to select this Tor alternative or the first two alternates.
4. Virtual Private Network (VPN)
When searching for Tor alternatives, how can we not add one of the best web browsers offering the best deals to its customers and that Tor alternative is a Virtual Private Network?
Virtual Private Network allows their users to emphasize being anonymous and offer the best deal to its users by providing some special features like High grade and kill switch encryption.
VPN allows its customers to have full-on privacy and promote anonymous web searching, but VPN’s downfall is not accessing the deep web. If a user wants to access the deep web, they have to search for another Web browser that allows easy access to the deep web.
When we try something new, we pull a background check on it, and in the same way, we should know about each advantage and downfall of VPN, so let’s get to know what it can provide other than very secure and anonymous web browsing.
Express VPN and Nord VPN are the most widely used VPN providers. It allows you to browse anonymously and help maintain anonymity by swiping off your IP address over the internet. It protects the IP address from harmful hands, such as hackers and ISPs.
It also provides its users with fast speed when downloading or streaming. It plays tricks on ISPs and hackers by changing the reallocation of the customer, thus enhancing the security it provides and allowing users to have complete access to the internet as they can access any websites, channels, and censored content from anywhere on this globe.
All the above features can help clear any doubts that can stop or allow you to use this web browser as Tor alternates.
5. TOX
Tox is one of the Tor alternatives that not only allow its users to have complete privacy over their searching data but also allow its customer to save their friendly chatting from any evil eye.
Tox allows users to have end-to-end encryption as it has a protocol that enforces peer-to-peer messaging and video calls.
We can not say that Tox is the best suitable Tor alternate, but it provides some other advanced options such as a private encoded IM, video calls, and conferencing that is pretty easy to do.
Tox may not be what you are looking for, but it provides communication safety that no other Tor alternate may not provide to its customer, so the fifth Tor alternate is Tox.
6. Ipredia OS
Are any Linux users here? If yes, IprediaOS is one of the best alternatives any Linux user can have as a Tor alternate.
It offers anonymous web browsing and lets the user have safe communication due to different layers that protect any apps that do not provide identity security.
Ipredia OS is one of the Tor alternates that allows Linux users to access the deep web that is not available in most of the Linux-accessible web browsers and is one of the powerful operating systems which encrypts all the users’ network traffic levels to regulate anonymity.
In its service, Ipredua OS provides its users with an I2P router, an anonymous email client, an IRC client, and an anonymous BitTorrent client.
IprediaOS is one of the best deals users can get as Tor alternates.
7. I2P
The next Tor alternates’ title is I2P, the Invisible Internet Project. The Invisible Internet Project is a completely anonymous web browser that allows you to continue your chat without any doubt of data leakage, providing you with a peer-to-peer connection to its users.
It also provides its customers a free non-tracking web browser that does not allow ISPs and malicious users to track their browsing data.
The Invisible Internet Project provides its customers with end-to-end encryption. It is a fully encrypted private network developed to secure the user’s identity and provide protection for users; activity, location, data, and identity.
The sent messages go through 4 different layers of encryption, which secures the communication. It sends messages in encrypted form and encrypts the endpoints to configure safe communication.
The main aim behind I2p ( Invisible Internet Project) is to maintain a safe shell around communication, thus blocking any malicious attacks which attract a general audience consisting of mostly journalists and economic people who want to take preventive measures in economic amounts.
Therefore, I2P may be your next economical choice as a tor alternatives for anonymous web browsing and communication.
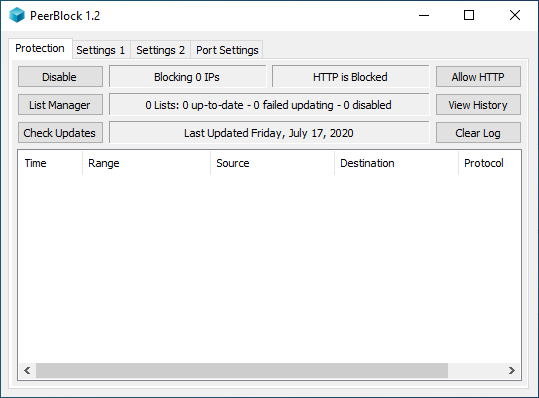
8. PeerBlock
When you are looking to isolate yourself and trying to maintain some special number of people in your life, then our next Tor alternate, PeerBlock is the best option to do so.
It prevents tracking and allows you to maintain the number of people connected to you on the web.
Everything has hidden faults, and so does PeerBlock, as it is incapable of blocking every tracking ISPs and hacker from tracking and blocking them.
Apart from this fault, PeerBlock is still one of the most used Tor alternates users use for anonymous web browsing and communication. Any economic or wealthy person can use it as it is free.
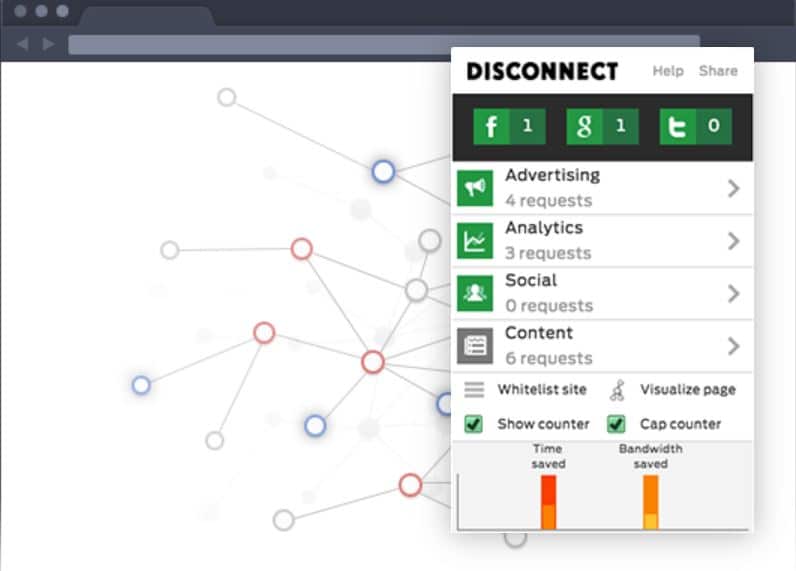
9. Disconnect
Yet another Tor alternate, Disconnect is a private web browser that searches all the websites containing your informational data and detaches you from them, such as Facebook, Google, Twitter, etc.
A user on Windows, Android, and iOS can access Disconnect on different offers and membership plans.
The advantage of Disconnect is that it shows all the tracking requests from the websites you blocked in the green color sign, whereas the upcoming unblocked trackers are shown in the grey color.
The color-indicating features allow users to verify upcoming and blocked trafficking requests rather than decipher where to find the blocked requests.
The features mentioned above enable us bloggers to add Disconnect to the list of Tor alternates.
Not everything is perfect, so Disconnect also has its imperfection in that it cannot track all the tracking requests, as some apps don’t work if their tracking requests are blocked, such as YouTube and Flickr, or even show some of the broken pages.
Due to this, these websites are suggested not to work with as it gets unblocked by default.
10. Freenet
The 10th position of Tor alternate goes to Freenet, and just like I2P (the Invisible Internet Project), it is a peer-to-peer platform for those who want to save their freedom of speech as many websites steal it from you without your knowledge.
Freenet is one of the leading Tor alternates that many internet users are opting for nowadays because of Freenet regulating principle of UI design, thus keeping all the informational data safe.
The web browser says, “ Freenet is a peer-to-peer platform for censorship-resistant communication and publishing. Freenet uses P2P (peer-to-peer) for communication and data storage but uses a completely different protocol for user interaction and network structure.
It provides a set of security that is DrakNet and OpenNet. These pair of security work differently from each other as OpenNote allows users to connect with other internet users. In contrast, DarkNet only allows its customers to connect with a person they have already connected and exchanged the key with.
If looking for a more preventive web browser, then Freenet is one of the best ones in this tor alternatives’ list as it does not have any central server which can be hacked in.
The central serverless web server does not allow any information to be leaked as it is very hard to hack in. It encrypts the end part also to ensure furthermore the data’s safety and less prone to any exploitation.
Therefore the tenth place in the list of Tor Alternates goes to Freenet.
11. Yandex Browser
Safety comes first, so the next Tor alternates provide you with the best offers regarding security, and that is Yandex Browser.
When surfing through any website, it immediately scans the internet, thus providing you security against any malware attacks on the website.
One of the major advantages users can take from Yandex Browser is its safety measurement by blocking any malicious website and securing passwords, personal details, and any online payment transaction information.
It also keeps your location private from tracking third parties such as ISPs and unemployed and employed hackers.
It allows its users to have complete anonymity as it swipes off their location and IP address, and it also encrypts the domain name system traffic due to its usage of DNSCrypt. To do so, the browser setting should enable domain name encryption.
According to all the features we as a user are getting, explain the place of Yandex Browser as Tor alternates.
12. Tails
When searching for the best Tor alternative, how can we not include Tails name in the list? Tails are one of the finest Tor alternates on the market and are accessible on any device, either by using a USB stick or any other DVD.
Tails have pre-built configured apps that allow you to access many apps, such as image editors, IM clients, office suites, and sound editors.
It lets users have an anonymous experience and avoid censorship when using Tail as Tor alternates.
It does not leave any of your surfing trails on the device you accessed it on. In all of these features, it also encrypts files, emails, and any messages using cryptographic tools, thus providing safe communication. Tails are used widely and are seen as the best tor alternate.
13. Freepto
The good-to-go web browser is Freepto which works as a Tor alternate and is especially in the market for Linux users, just like Whonix.
It does not let any third party like ISPs and hackers track your browsing data by giving them a hard time tracing your activity, just like Tor, thus becoming a good Tor alternate.
It is easy to go web browser that pretty much makes you bullet train in a matter of speed. It lets you keep your identity anonymous while surfing and send the tracker running for the money in case of tracing your work. It also maintains high-security levels by encryption and such kind of software.
Freepto is one of the best Tor alternates that allows you to keep your freedom of speech and helps you avoid the government’s eyes (it does not mean doing any evil or criminal thing) as well easily accessible on any device, just like Tails. It can be used from the USB stick, and the data is automatically encrypted.
Freepto is one of the Tor alternates that provides you best security and compatibility.
14. Psiphon Browser
The next tor alternate is the Psiphon browser which takes 14th place in the list of tor alternatives. It is easily accessible, and any normal person with minimum knowledge can access it.
It allows users to have multi-screening and server switching, which many tor alternatives may not provide.
Psiphon browser is based on VPN and SSH for establishing more customers, even from the most excluded areas around the globe, and provides you with complete security.
It makes a shield around you to protect you from any third-party intrusion like ISPs and any authoritative body such as Government and no not from the FBI ( do not think about committing a felony).
Psiphon hides your IP address so no one can access it and is very much free; thus no requirement of going bankrupt for it. Anyone who wants an economic tor alternative deal can use the Psiphon browser.
A person using Android or iOS can access the Psiphon browser in their device as it grants its users free access and promises security.
15. Firefox Focus
One of the newest discoveries of the Mozilla Foundation and corporation is Firefox Focus, a Tor alternative. A person on iOS and Android can utilize Firefox Focus, but the only difference is the search engine. Android users have a Blink engine, whereas iOS users have a Gecko engine.
Firefox Focus does not allow any evil eye to seek your informational data and protects your data from bigger authoritative bodies. One of the best things is its aesthetics and graphics.
One of the major drawbacks is that it is not accessible on Firefox Klar, but its software telemetry allows users to know their usage boundary as it is enabled by default.
Firefox Focus has special features that block social and stop ad tracking. It also provides you with a fast speed and leaves you with a good anonymity experience.
Android users get fewer hi-fis offers than iOS users as they know the number of ad intrusions blocked on the previously browsed websites.
Firefox Focus is one of the best tor alternatives that any internet users want to have in their hands.
16. Globus Privacy Browser
The sixteenth place for a tor alternative goes to Globus as it is one web browser that provides you the same service as Tor. Just like Psiphon Browser, Globus is also based on VPN servers.
It provides data leakage with the help of VPN servers and makes your traffic invisible, thus preventing any ISPs and hackers from tracking your traffic.
It does not allow any mindless person to enter your device and prevents looting your personal information and browsing information.
It also prevents malware from breaching your security, allowing you to block the websites and offering to unblock those websites.
It is compatible with almost any operating system, provides premium anonymity and security online, and makes the users capable of selecting the VPN server’s location.
If you are Looking for the best Tor alternative, then, Globus is the best Tor alternative deal to grab.
✅FAQ
Is Tor better than VPN?
For the following reasons, Tor outperforms a VPN:
Using a VPN to access the internet:- It’s nearly impossible to identify the original user of a Tor connection. Therefore, viewing a website without leaving any identifying information on your computer or the server that hosts it is safe.
Accessing the dark web:- The black web can be accessed using Tor (a.k.a. the darknet). Most dark web comprises unlisted websites that can only be accessed via a Tor connection.
Although it’s frequently connected to illegal conduct, such as black markets, there are many lawful uses for it as well.
Untraceable communication:– Those who prefer to remain anonymous, including journalists and their sources, activists, dissidents, and crime victims, can use Tor to securely communicate without being found out or leaving a paper trail of evidence.
Which browser is untraceable?
Tor Browser: By routing your communication via at least three nodes in the Tor network, Tor conceals your name, preferences, and other personal information.
Each Tor node (server) your data passes through encrypts it as it travels. This renders you incredibly anonymous until you insert your info elsewhere. In addition, the Tor Browser uses NoScript to hide your previous activity from the websites you visit.
Tor doesn’t only avoid logging your online activities; it also removes any cookies you may have loaded after each session.
As a result, Tor is the anonymous browser of choice for journalists and activists working in challenging environments because of its high anonymity and privacy capabilities. Regular upgrades also increase the security of the system.
Is Tor better than brave?
The obvious answer is both. Use Tor when you need the most privacy and security possible and Brave for regular browsing.
Swift and trustworthy are Brave. Although it is significantly less private and secure than Tor, it is still significantly safer and more anonymous than most browsers.
Is Tor no longer secure?
You can browse anonymously by using the Tor browser. However, we highly advise against relying solely on Tor for online security.
Numerous examples have demonstrated how improper usage of Tor can lead to serious privacy breaches or even problems with your online safety. Consider malware, thieves, and hackers.
The best way to secure oneself is using the Tor browser, a reliable virtual private network (VPN), and antivirus software.
Can the FBI track Tor?
If you use Tor to support illegal conduct, the FBI can track your activities to an exit node and obtain a court order to see the node’s logs.
Even if this doesn’t work, they can still intercept your communication at a middle server and insert a rootkit to gain access to your computer.
Can police track Tor?
First and foremost, avoid taking any actions that may make you need to flee from the authorities.
They may perform a forensic investigation on your computer to find out where you went on Tor. This is not a problem if you use Tails. They may also install spyware on your computer to track your movements.
They can even take control of any website, including a Tor website, and employ malicious code to discover your identity (typically through Java Script).
If not, neither your ISP nor the police can tell what websites you’re accessing when you connect to Tor unless the latter are running vulnerabilities on their websites.
Will my ISP know if I use Tor?
Some ISPs may be throttling or blocking Tor traffic due to its use in criminal activities. Your ISP cannot read your traffic or determine which website you are viewing because of onion routing.
Your ISP will be aware that you are utilizing Tor, nevertheless. This is because Tor nodes’ IP addresses are known to the general public. Tor Bridges offer a remedy for this issue.
Although it is not included in the main Tor directory, a bridge is still a Tor node. So your ISP won’t be able to block all bridges. ISPs, however, have a fix for this. To ascertain whether Tor is being used, they examine packets.
Let’s make use of Pluggable Transports to alleviate this. Unfortunately, as a result, the packets are obscured and do not resemble Tor communication.
Why shouldn’t you use a VPN with Tor?
The VPN provider can observe your activities and whereabouts when using a VPN.
However, with Tor, nobody can spy on your activity, not even Tor node operators. Therefore, you cannot use a VPN to access Tor’s hidden services.
Does Tor hide your IP?
The Tor Browser reroutes web traffic across several routers known as nodes to conceal your IP address and browsing behavior.
Whistleblowers, journalists, and others who want to safeguard their online privacy use Tor because it masks browsing activity and disables tracking.
Do I need a VPN as well as Tor?
The Tor Browser reroutes web traffic across several routers known as nodes to conceal your IP address and browsing behavior.
Whistleblowers, journalists, and others who want to safeguard their online privacy use Tor because it masks browsing activity and disables tracking.
Should I use Tor for everything?
Tor improves your online privacy but won’t shield you from all internet threats. While using Tor to browse the internet is far safer than doing so without any security measures, Tor is not completely secure.
Traffic that travels through Tor nodes must be encrypted before accessing the public internet. One of the main issues with Tor is in this area.
The person in charge of the “exit node” may monitor your traffic and snoop on private information. Users can be spied on by bad actors, oppressive governments, and spies operating their nodes.
Is DuckDuckGo a Tor Browser?
Even though they share a few characteristics, Tor and DuckDuckGo are unrelated.
Search engine DuckDuckGo is focused on privacy; therefore, it has that in common with Tor. According to their documentation, DuckDuckGo does not monitor you for advertising purposes when you conduct searches on their website.
In contrast, Tor functions as both a network and a browser. The Tor network is a collection of nodes and relays run by volunteers that reroute users’ web traffic around the globe to maintain their anonymity.
A fork of Firefox that utilizes the Tor Network and has been customized for privacy is called the Tor Browser.
Which Web browser is safest?
Firefox, Google Chrome, Chromium, Brave and Tor, etc., are considered the safest browsers and offer users extra security while browsing.
Is Onion Tor safe?
The onion routing mechanism, which encrypts your data and conceals your IP address, is one of the reasons why the Tor Browser is usually regarded as safe and secure.
However, Tor does have significant weaknesses, and like with any browser, users of Tor are still susceptible to online dangers like malware and phishing fraud.
Does downloading Tor put you on a list?
Your use of Tor and interactions with known criminals may put you on a watchlist, depending on the laws in your area.
Is there a browser safer than Tor?
Tor’s security level is high, but it is not foolproof. Other browsers prioritize security, such as Brave and Mozilla Firefox.
These browsers have built-in measures to block ads and prevent tracking, which can help protect your privacy.
However, if your main concern is anonymity, Tor remains one of the best options. Its decentralized network and multiple layers of encryption make it difficult to track your online activity or identify your IP address.
Remember that no browser can guarantee complete anonymity or security, so taking additional measures to protect your privacy while browsing is important.
Why doesn’t Tor work anymore?
Tor may no longer work as expected due to various reasons, such as network disruptions or technical issues.
Nevertheless, it’s worth noting that Tor is generally reliable in ensuring online privacy and anonymity.
If Tor is malfunctioning, it could be due to network congestion or attacks that might cause it to slow down or become unavailable. Alternatively, the issue could be with your computer or network settings.
To fix the problem, attempt restarting Tor or your computer and check your network settings. You can also try using a different device or browser to see if the problem persists.
If the issue persists, you can find online resources or seek assistance from the Tor community.
What apps are similar to the Onion browser?
There are apps similar to Onion browser that prioritize online anonymity and privacy. Here are some examples:-
Orfox – a mobile web browser for Android devices that is based on the same source code as Tor. It provides similar anonymity and privacy features as the desktop version.
Brave – a privacy-focused web browser that offers built-in ad-blocking and anti-tracking measures to safeguard online privacy. It has a Tor-powered private browsing mode and uses encryption to secure browsing activity.
Firefox Focus – a mobile web browser that prioritizes privacy and security. It blocks ads and tracking cookies and deletes browsing history automatically.
I2P – an anonymous network that uses encryption and routing to protect the online activity, similar to Tor. It has a built-in web browser and access to websites hosted on the I2P network.
Can Tor be traced?
Tor offers online anonymity and privacy while browsing the internet. However, no technology is perfect, and privacy and security could be compromised due to potential vulnerabilities.
Tracing Tor usage is possible under certain circumstances, such as an attacker controlling both entry and exit nodes of the Tor network. Users’ identities may also be revealed if they log into personal accounts using Tor.
Using Tor doesn’t guarantee complete online anonymity or security. Safe browsing habits and additional measures, like virtual private network (VPN) usage, avoiding logging into personal accounts while using Tor, and being cautious of unknown sources for file downloads or link clicks, can help protect privacy and security.
Do I need a VPN if I use Tor?
Adding a virtual private network (VPN) can increase security while using Tor for anonymous and private internet browsing.
A VPN encrypts and routes internet traffic through a server before entering the Tor network. This prevents internet service providers (ISPs) from monitoring activity or tracking Tor usage. A VPN can also protect malicious exit nodes and other attacks on the Tor network.
However, using a VPN with Tor can cause latency and reduce internet speed. Choosing a reputable VPN provider that does not compromise user privacy is crucial.
Whether a VPN is necessary with Tor depends on individual needs and desired privacy and security levels.
A VPN can provide extra protection for high-risk activities like whistleblowing or political activism. For everyday use, Tor alone should suffice.
Is Tor blocked in the US?
Tor is not blocked in the US. It’s a legal tool that anyone, including US citizens and residents, can use.
However, organizations such as schools, libraries, and government agencies may block Tor on their networks for policy enforcement or security reasons.
Using Tor does not exempt users from applicable laws or regulations, and some activities conducted through Tor may still be illegal. While Tor provides anonymity and privacy, it does not guarantee complete security or protection against all online threats.
If accessing Tor is difficult, the issue may be due to technical problems or network disruptions.
Trying a different device or network can help determine if the problem persists. For further assistance, the Tor support team can be contacted.
Can Tor bypass blocked websites?
Tor may bypass blocked websites, depending on the blocking method used. Tor is a privacy tool that routes internet traffic through servers, making monitoring or tracking online activity difficult.
This could allow users to access blocked websites by an internet service provider (ISP) or network administrator.
However, some ISPs and network administrators use advanced methods like deep packet inspection or domain name system (DNS) filtering to block websites. These methods may detect and block Tor traffic, making it hard to bypass website blocks.
Additionally, accessing blocked websites through Tor may be illegal or violate terms of service agreements based on jurisdiction and context.
Using Tor legally and responsibly is important while knowing its potential risks and limitations.
Does Onion Browser hide IP?
Onion Browser is a Tor-based web browser that provides anonymity and privacy while browsing the internet.
Onion Browser routes internet traffic through servers, making it difficult to track online activity or identify the user’s IP address.
While using Onion Browser, the user’s IP address is hidden from websites and anyone monitoring internet activity. However, Tor has potential vulnerabilities that could compromise anonymity and privacy.
Onion Browser offers anonymity and privacy but does not guarantee complete security or protection from all online threats. Practicing safe browsing habits and additional measures to protect privacy and security online is recommended.
Which browser is untraceable?
No browser can guarantee complete anonymity, but certain browsers provide stronger privacy than others.
Tor is a privacy-focused web browser that uses a server network to route internet traffic and provide anonymity while browsing the web. Tor has vulnerabilities that may compromise privacy and security.
Other privacy-focused browsers include Brave, which blocks website trackers and ads by default, and Mozilla Firefox, which offers privacy features such as tracking protection and encrypted DNS.
Using a virtual private network (VPN) alongside a web browser can provide added privacy and security while browsing the internet.
Choosing a browser depends on individual privacy and security needs and circumstances. Researching and selecting a browser that meets those needs and practicing safe browsing habits and additional measures to safeguard online privacy and security are crucial.
Is Tor a DuckDuckGo?
Tor and DuckDuckGo differ from each other. Tor is a web browser that provides anonymity and privacy by routing internet traffic through a server network, preventing the monitoring of online activity.
On the other hand, DuckDuckGo is a search engine that prioritizes user privacy by not tracking or storing user data and delivering encrypted search results.
Tor and DuckDuckGo prioritize user privacy differently. Tor provides anonymity and privacy by routing internet traffic through a server network, while DuckDuckGo prioritizes user privacy by not collecting or storing user data.
DuckDuckGo can be used as a search engine with the Tor browser to enhance online privacy and anonymity.
Is Tor better than a VPN?
Tor and VPNs are privacy and security tools with distinct strengths and weaknesses.
Tor offers anonymity and privacy by routing internet traffic through a server network, impeding the monitoring of online activity. Tor is free but slow, and some websites may block Tor users.
VPNs encrypt internet traffic and route it through a secure server, safeguarding privacy and security. VPNs can be faster than Tor and provide access to restricted content, but they can be costly and vulnerable to data breaches.
The choice between Tor and VPNs depends on personal needs. Tor prioritizes anonymity and privacy despite slower speeds.
VPNs prioritize faster speeds and features, albeit at a cost. Combining Tor and VPNs can enhance online privacy and security.
How do Tor users get caught?
Although Tor provides anonymity and privacy, it’s not foolproof, and there are ways that users can be identified and caught.
One method is “traffic correlation analysis,” where an attacker matches internet traffic patterns to identify the Tor traffic source. However, this method is not always successful.
Another method is “endpoint compromise,” where an attacker gains control of the user’s device and monitors their activity, even when using Tor.
It’s essential to note that Tor doesn’t protect against all online threats, such as malware and phishing attacks, which can compromise privacy and security.
To minimize the risk of getting caught while using Tor, practice good online security habits, keep software and security tools up to date, and avoid illegal activities or accessing illegal content.
It’s also crucial to understand the potential vulnerabilities of Tor and take additional measures, such as using a VPN or Tails operating system, to enhance online privacy and security.