Reverse engineering tools are indispensable technological instruments, enabling the meticulous analysis and comprehension of intricate systems.
These reverse engineering tools, at their core, encompass software applications or frameworks that facilitate the dissection, decompilation, and analysis of existing software, hardware, or systems.
Reverse engineering entails the process of unraveling the inner workings of a product or system to grasp its design, functionality, and underlying algorithms. Professionals can delve into proprietary software, decipher enigmatic file formats, and gain profound insights into undocumented systems by employing these tools.
The importance of reverse engineering tools cannot be overstated. They are pivotal in conducting vulnerability analysis, malware assessment, software interoperability evaluations, and compatibility appraisals.
Through reverse engineering, professionals can discern security vulnerabilities, gauge the robustness of a system, and strategize effective mitigation techniques. Moreover, reverse engineering tools foster innovation and propagate knowledge sharing.
They empower developers to examine triumphantly designed software and hardware solutions, extracting lessons and employing those insights to craft novel and enhanced products.
In an ever-evolving technological landscape, reverse engineering tools empower researchers, analysts, and developers to unlock the enigmas of intricate systems.
Their utilization leads to a profound comprehension of existing technologies, unveiling vulnerabilities and fueling innovation across diverse domains.
Understanding Reverse Engineering
In the realm of technology, reverse engineering is a multifaceted process that involves unraveling the inner workings of a product, system, or software to gain a deep understanding of its design, functionality, and underlying principles. Experts employ this essential technique to analyze and comprehend complex systems.
Reverse engineering entails systematically dissecting a product or system, examining its components, and comprehending how they interact. This process often involves utilizing various tools and techniques to decipher proprietary code, reconstruct algorithms, and uncover hidden functionalities.
Reverse engineering serves various purposes, including understanding legacy systems, overcoming compatibility issues, or uncovering potential security vulnerabilities.
By engaging in this process, experts can gain valuable insights into the workings of existing technologies, paving the way for improvements, innovation, and problem-solving.
Reverse engineering can be challenging, requiring a combination of technical expertise, analytical skills, and a curious mindset. It involves scrutinizing intricate code structures, reverse compiling binaries, and reconstructing high-level representations from low-level machine code.
In conclusion, understanding the intricacies of reverse engineering enables professionals to unlock the mysteries of complex systems, unravel proprietary technologies, and drive advancements in various domains.
By employing this technique, experts can uncover hidden knowledge, address compatibility issues, enhance security measures, and push the boundaries of innovation.
Best Reverse Engineering Tools To Master the Art of Software Dissection
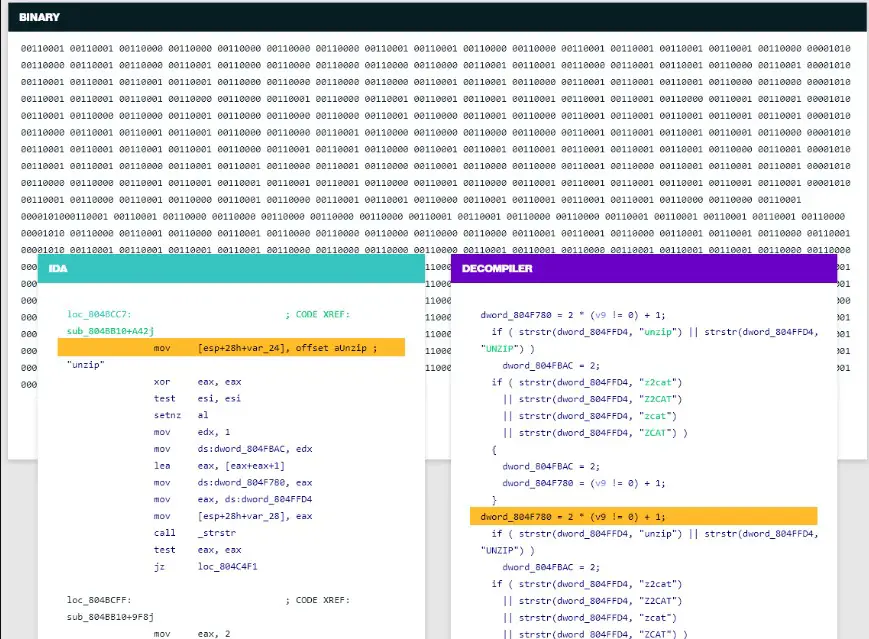
1. IDA Pro
When it comes to the realm of reverse engineering, IDA Pro stands as one of the best tools available to professionals in the field.
Offering a comprehensive suite of features and an intuitive user interface, IDA Pro empowers analysts, researchers, and security experts to delve deep into the intricate internals of software and hardware systems.
IDA Pro provides a rich and robust set of functionalities for reverse engineering tasks. Its advanced disassembler allows users to analyze binary code efficiently, uncovering the system’s hidden logic and true essence.
Its interactive graph view visually represents code flow, aiding in understanding complex control structures and identifying vulnerabilities.
One of the standout features of IDA Pro is its extensibility. The tool supports the development of plugins and scripts, allowing users to customize and automate their reverse-engineering workflows. This flexibility ensures that IDA Pro can adapt to various use cases and accommodate specific needs.
The IDA Pro community is a testament to its widespread adoption and continued development. The vibrant community offers many resources, including tutorials, plugins, and support forums, fostering collaboration and knowledge sharing among reverse engineering enthusiasts.
In conclusion, IDA Pro has become a go-to tool for reverse engineering endeavors. Its robust feature set, user-friendly interface, and extensibility make it a top choice for professionals seeking to unlock the secrets hidden within software and hardware systems.
With IDA Pro, the possibilities for exploration, analysis, and innovation in reverse engineering are boundless.
Features:-
- Advanced disassembler for efficient analysis of binary code
- Interactive graph view for visual representation of code flow
- Extensibility through support for plugin and script development
- User-friendly interface for intuitive navigation and interaction
- Robust set of functionalities for comprehensive reverse engineering tasks
- Active community providing resources, tutorials, and support forums
- Capabilities to uncover hidden logic and vulnerabilities within systems
- Customization options to tailor the tool to specific needs
- Automation support for streamlining reverse engineering workflows
- Continuous development and updates to stay up-to-date with evolving technologies.
Pros:-
- Powerful and advanced disassembler for thorough analysis of binary code.
- Intuitive and user-friendly interface for ease of navigation and interaction.
- Extensibility through plugin and script development, allowing customization and automation.
- Interactive graph view provides a visual representation of code flow, aiding in understanding complex control structures.
- Robust feature set and comprehensive functionalities cater to various reverse engineering needs.
- Active community support with resources, tutorials, and forums for collaboration and knowledge sharing.
- Regular updates and continuous development to keep up with evolving technologies.
- Capabilities to uncover hidden logic, vulnerabilities, and insights within software and hardware systems.
- Trusted and widely used by professionals in the field, ensuring reliability and credibility.
Cons:-
- The High licensing cost makes it less accessible for individuals or small organizations.
- Steeper learning curve for beginners due to the complexity of reverse engineering concepts.
- Limited compatibility with certain platforms or architectures, potentially restricting its usage in specific scenarios.
- Requires a considerable amount of system resources, leading to higher hardware requirements.
- Some advanced features may require additional plugins or expertise, adding complexity to the workflow.
- Lack of built-in support for certain file formats or uncommon architectures, requiring workarounds or additional tools.
- Limited customer support options, potentially leading to longer response times for technical assistance.
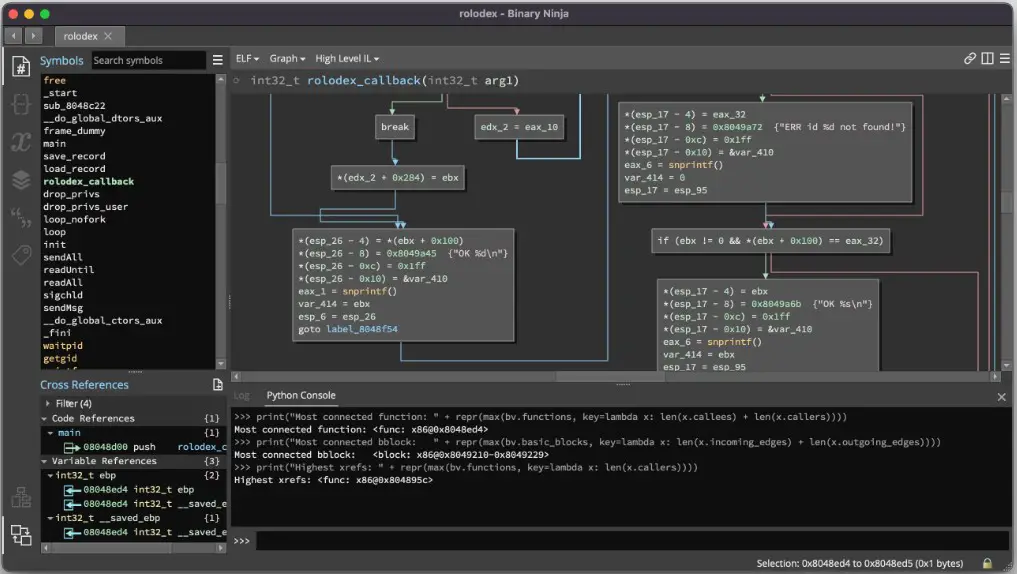
2. Binary Ninja
Binary Ninja is a formidable tool in reverse engineering and binary analysis.
With its innovative features and cutting-edge capabilities, Binary Ninja empowers security researchers, malware analysts, and software engineers to dissect and understand the intricate inner workings of binary code.
At its core, Binary Ninja is a sophisticated and powerful platform designed to unravel the complexities of binary files.
Its advanced disassembly and decompilation capabilities enable users to navigate through the low-level assembly instructions and comprehend the high-level logic and functionality of the code.
One of the distinguishing features of Binary Ninja is its user-friendly interface. Its clean and intuitive design allows users to navigate, annotate, and analyze binary code effortlessly.
The platform offers a rich set of graph views, allowing for visual representations of control flow and data flow, aiding in understanding complex code structures.
Furthermore, Binary Ninja’s extensibility through plugins and extensive API support enables users to customize and automate their analysis workflows.
This flexibility allows for custom tools, additional functionality, and integration with other software.
In conclusion, Binary Ninja emerges as a powerful ally for reverse engineers, offering advanced disassembly, decompilation, and analysis features.
Its user-friendly interface, extensive graph views, and extensibility make it a favored choice for professionals delving into the intricacies of binary code.
With Binary Ninja, binary analysis opens up, enabling deep insights, vulnerability discovery, and innovative advancements in software and security.
Features:-
- Advanced disassembly and decompilation capabilities for a thorough analysis of binary code
- User-friendly interface designed for intuitive navigation and analysis
- Rich set of graph views, including control flow and data flow, for a visual representation of complex code structures
- Extensibility through plugins and extensive API support, allowing customization and automation of analysis workflows
- Collaborative features for team-based reverse engineering projects
- Support for various architectures and file formats, enhancing compatibility and versatility
- Interactive and customizable visualization options for code analysis and exploration
- Integrated scripting capabilities for advanced automation and custom tool development
- Continuous updates and improvements, ensuring compatibility with evolving technologies and security challenges
- Active community support, providing resources, tutorials, and a platform for knowledge sharing and collaboration.
Pros:-
- Advanced disassembly and decompilation capabilities for in-depth analysis of binary code.
- User-friendly interface designed for intuitive navigation and ease of use.
- Rich graph views provide visual representations of code flow and structures.
- Extensibility through plugins and extensive API support, enabling customization and automation.
- Collaboration features facilitate team-based reverse engineering projects.
- Support for various architectures and file formats, enhancing versatility.
- Interactive and customizable visualization options for code analysis and exploration.
- Integrated scripting capabilities for advanced automation and custom tool development.
- Continuous updates and improvements to stay current with evolving technologies and security challenges.
- Active community support, providing resources, tutorials, and collaboration opportunities.
Cons:-
- Relatively high cost compared to some other reverse engineering tools.
- The steeper learning curve for beginners due to the complexity of binary analysis concepts.
- Limited documentation and resources for certain advanced features.
- Less extensive community than other tools, potentially limiting support and resources.
- Occasional stability issues or compatibility challenges with specific binary files or environments.
- Not as widely known or adopted as some other prominent reverse engineering tools.
- Resource-intensive, requiring higher hardware specifications for optimal performance.
- Limited support for certain specialized architectures or file formats, potentially requiring additional tools or workarounds.
- The potential need for additional plugins or customization to fully meet specific analysis requirements.
3. Ghidra
Ghidra is a free reverse engineering tool that has garnered significant attention and acclaim in the cybersecurity and software analysis communities.
Developed by the National Security Agency (NSA) and released as an open-source platform, Ghidra offers a robust set of features and capabilities for reverse engineering tasks.
At its core, Ghidra is designed to aid professionals in comprehending and analyzing binary code, enabling them to unravel the intricate workings of software and uncover valuable insights.
Its advanced disassembly and decompilation capabilities empower users to explore and understand low-level assembly instructions and reconstruct high-level code representations.
One of the standout features of Ghidra is its user-friendly and customizable interface. It provides graphical views that visually represent code flow, control structures, and data dependencies, facilitating the analysis of complex programs.
Being a free tool, Ghidra offers accessibility to a wide range of users, allowing them to leverage its powerful capabilities without costly licenses.
Additionally, Ghidra’s open-source nature fosters a collaborative and supportive community where users can contribute to plugins, share knowledge, and help enhance the tool’s functionalities.
In conclusion, Ghidra’s emergence as a free reverse engineering tool has democratized the field by providing powerful analysis capabilities to a broader audience.
Its advanced features, user-friendly interface, and active community support make it an invaluable asset for professionals involved in reverse engineering tasks, enabling them to delve deep into binary code and unlock the secrets hidden within.
Features:-
- Advanced disassembly and decompilation capabilities for in-depth analysis of binary code.
- User-friendly and customizable interface for intuitive navigation and enhanced user experience.
- Graphical views and visual representations of code flow, control structures, and data dependencies.
- Support for various processor architectures, allowing analysis of diverse software and systems.
- A collaborative and supportive community, fostering knowledge sharing and plugin development.
- Integrated scripting capabilities for automation and customization of analysis workflows.
- Interactive and customizable views for efficient code navigation and analysis.
- Ability to handle large-scale projects and handle complex codebases.
- Regular updates and improvements to enhance functionality and address security concerns.
- Free and open-source nature eliminates the need for expensive licenses and promotes accessibility for a wider range of users.
Pros:-
- Advanced disassembly and decompilation capabilities for a thorough analysis of binary code.
- A User-friendly and customizable interface enhance user experience and productivity.
- Graphical views provide visual representations of code flow and structures, aiding comprehension.
- Support for various processor architectures enables the analysis of diverse software and systems.
- A collaborative community fosters knowledge sharing and plugin development, expanding functionality.
- Integrated scripting capabilities allow for automation and customization of analysis workflows.
- Interactive and customizable views facilitate efficient code navigation and analysis.
- Regular updates and improvements ensure the tool stays current with evolving technologies.
- Its free and open-source nature makes it accessible to many users.
Cons:-
- The steep learning curve for beginners is due to the complexity of reverse engineering concepts.
- Resource-intensive, requiring a robust system to handle large-scale projects and complex codebases.
- Potential stability issues or compatibility challenges with certain binary files or environments.
- Limited official support compared to commercial tools, relying heavily on community resources.
- Not as widely adopted as some other prominent reverse engineering tools, resulting in a smaller ecosystem of plugins and community support.
In conclusion, Ghidra’s free and advanced features make it a compelling choice for reverse engineering tasks.
While it may have a learning curve and potential limitations, its accessibility, functionality, and active community contribute to its popularity among professionals in the field.
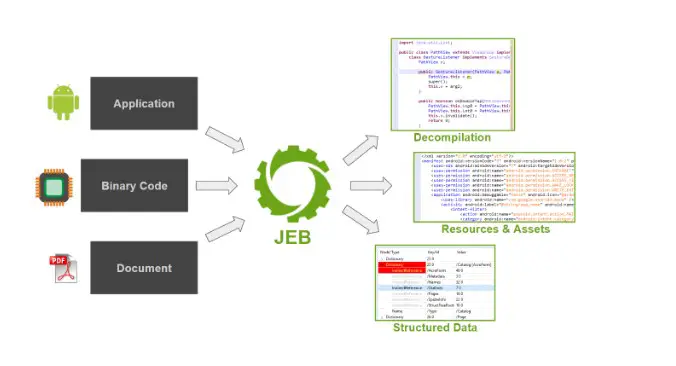
4. JEB Decompiler
When it comes to dissecting and comprehending the inner workings of complex software systems, JEB Decompiler stands as a formidable tool in the realm of reverse engineering.
Developed by PNF Software, this cutting-edge decompilation software unveils the underlying secrets hidden within compiled executables.
With its advanced decompilation engine, JEB Decompiler delves into the intricate layers of binary code, skillfully transforming low-level machine instructions into human-readable source code.
Its remarkable precision and efficiency enable reverse engineers, cybersecurity analysts, and malware researchers to unravel the most cryptic software artifacts.
Boasting support for a diverse range of binary formats, including native code, Java applications, and Android APKs, JEB Decompiler demonstrates unparalleled versatility.
It enables users to navigate complex codebases effortlessly, offering insights into classes, methods, variables, and control flow.
The tool’s intuitive user interface facilitates a seamless and intuitive experience, empowering users to explore and comprehend the complex architecture of compiled executables.
Moreover, its extensibility through a robust plugin system allows developers to tailor its functionality to their needs, enhancing the overall reverse engineering workflow.
With JEB Decompiler, users can harness the power of automated analysis and scripting, utilizing languages such as Python and Java to streamline their reverse engineering tasks.
This enables the creation of custom analysis modules and the integration of external tools for a comprehensive and efficient reverse engineering process.
In summary, JEB Decompiler emerges as an indispensable ally for those seeking to unravel the intricacies of software systems.
With its powerful decompilation engine, intuitive interface, and extensibility, JEB Decompiler offers a transformative experience, unlocking the secrets hidden within compiled executables and empowering reverse engineers with profound insights into the depths of code.
Features:-
Advanced Decompilation Engine: JEB Decompiler employs a powerful decompilation engine that accurately converts low-level machine instructions into human-readable source code.
Versatility with Binary Formats: It supports binary formats, including native code, Java applications, and Android APKs, enabling analysis across diverse software artifacts.
Intuitive User Interface: JEB Decompiler offers an intuitive user interface that facilitates seamless navigation through complex codebases, making it easier to explore classes, methods, variables, and control flow.
Extensibility through Plugins: The tool’s plugin system allows developers to customize and extend its functionality, enabling the integration of external tools and creating custom analysis modules.
Automation and Scripting: JEB Decompiler supports popular scripting languages like Python and Java, empowering users to automate tasks, streamline workflows, and enhance productivity.
Precise Code Analysis: It provides detailed insights into code structures, facilitating a comprehensive understanding of software systems, even in the presence of obfuscation techniques.
Malware Analysis Capabilities: JEB Decompiler is a valuable asset for malware analysts, offering deep visibility into malicious code, and enabling threat identification and mitigation.
Code Reusability: The decompiled source code generated by JEB Decompiler can be used for code review, understanding legacy systems, and aiding in software maintenance and enhancement.
Support and Updates: The JEB Decompiler team offers regular updates and supports users, ensuring a reliable and up-to-date reverse engineering experience.
Cross-Platform Compatibility: JEB Decompiler is designed to work seamlessly on multiple platforms, including Windows, Linux, and macOS.
These features collectively make JEB Decompiler an essential tool for reverse engineers, malware analysts, and cybersecurity professionals seeking to unravel the intricacies of compiled executables.
Pros:-
Accurate Decompilation: JEB Decompiler boasts a powerful engine that produces highly accurate decompiled source code, allowing for a thorough understanding of the analyzed software.
Versatility: With support for various binary formats, including native code, Java applications, and Android APKs, JEB Decompiler offers versatility in reverse engineering different types of software artifacts.
Intuitive User Interface: The tool provides an intuitive and user-friendly interface, making navigating complex codebases and exploring code structures easier.
Extensibility: JEB Decompiler offers a plugin system that allows users to extend its functionality, enabling customization and integration with external tools to enhance the reverse engineering workflow.
Automation and Scripting: The support for scripting languages like Python and Java enables users to automate repetitive tasks and create custom analysis modules, increasing productivity.
Malware Analysis Capabilities: JEB Decompiler proves valuable in the field of malware analysis, providing deep insights into malicious code and aiding in identifying and mitigating threats.
Cons:-
Cost: JEB Decompiler is a commercial tool, and its pricing structure may pose a barrier for individual users or those on a limited budget.
Learning Curve: While the user interface is intuitive, mastering the full capabilities of JEB Decompiler may require a learning curve, especially for beginners or those new to reverse engineering.
Limited Community Support: Compared to some other reverse engineering tools, JEB Decompiler may have a smaller user community, which could result in less readily available online resources and community support.
Despite these potential limitations, JEB Decompiler’s accuracy, versatility, intuitive interface, extensibility, and malware analysis capabilities make it a strong choice for reverse engineers, cybersecurity professionals, and malware analysts looking for a comprehensive tool to dissect and comprehend compiled executables.
5. Hopper Disassembler
Hopper Disassembler is a powerful and versatile tool that has become a staple in code analysis and reverse engineering.
It’s innovative features and comprehensive capabilities empower researchers, security experts, and software engineers to delve deep into the intricate world of compiled binaries and gain valuable insights into their underlying code structures.
At its core, Hopper Disassembler boasts an advanced disassembly engine that allows for efficient analysis and reconstruction of executable files.
It provides a human-readable representation of the disassembled code, offering a detailed understanding of the inner workings of the binary.
The tool’s user interface is designed to be interactive and intuitive, offering dynamic and visual representations of the disassembled code.
Supporting multiple platforms and architectures, Hopper Disassembler accommodates the analysis of software across diverse environments.
What sets Hopper Disassembler apart is its extensibility through a robust plugin system. Users can enhance and customize the tool’s functionalities, tailoring it to their specific requirements.
Additionally, it offers powerful analysis capabilities, including dynamic analysis and scriptable debugging, enabling deeper insights and aiding in discovering vulnerabilities.
In conclusion, Hopper Disassembler has become invaluable in code analysis and reverse engineering.
Its advanced disassembly engine, user-friendly interface, and extensibility equip professionals with the means to unravel the intricacies of compiled code and gain profound insights into complex binaries.
Features:-
- Advanced disassembly engine for efficient analysis and reconstruction of executable files.
- Human-readable representation of the disassembled code for a comprehensive understanding of the binary.
- Interactive and intuitive user interface with dynamic and visual representations of the code.
- Support for multiple platforms and architectures, accommodating diverse software environments.
- Extensibility through a robust plugin system, allowing customization and enhancement of functionalities.
- Powerful analysis capabilities, including dynamic analysis and scriptable debugging.
- Comprehensive and detailed information about code structures, functions, and variables.
- Integrated graph views for visualizing code flow and relationships.
- Binary patching and modification capabilities for experimentation and customization.
- Regular updates and improvements to stay current with evolving technologies and security challenges.
Pros:-
- Advanced disassembly engine enables efficient analysis of executable files.
- Human-readable representation of the disassembled code aids in understanding complex binaries.
- An interactive and intuitive user interface enhances user experience and navigation.
- Support for multiple platforms and architectures increases versatility.
- Extensibility through a plugin system allows customization and enhancement of functionalities.
- Powerful analysis capabilities, including dynamic analysis and scriptable debugging.
- Comprehensive information about code structures, functions, and variables.
- Integrated graph views provide visual representations of code flow and relationships.
- Binary patching and modification capabilities offer flexibility for experimentation and customization.
- Regular updates and improvements ensure the tool remains up-to-date with emerging technologies.
Cons:-
- Steeper learning curve for beginners due to the complexity of reverse engineering concepts.
- Limited official support compared to some other commercial tools.
- Occasional stability issues or compatibility challenges with specific binaries or environments.
- Lack of extensive documentation and resources for certain advanced features.
- Not as widely known or adopted as some other prominent disassemblers.
- Resource-intensive, requiring higher hardware specifications for optimal performance.
- Limited community support compared to more established tools.
In conclusion, Hopper Disassembler’s advanced features, user-friendly interface, and powerful analysis capabilities make it a valuable asset for code analysis and reverse engineering professionals.
While it may have a learning curve and potential limitations, it’s comprehensive functionalities and regular updates contribute to its effectiveness in tackling complex binaries.
6. Radare2
Radare2 is a versatile and powerful open-source framework that has garnered attention in binary analysis and reverse engineering.
With its innovative features and extensive capabilities, Radare2 empowers security researchers, malware analysts, and software engineers to dissect and comprehend the intricacies of binary code.
At its core, Radare2 provides a comprehensive suite of tools for disassembling, debugging, analyzing, and patching binaries.
Its modular architecture allows flexibility and extensibility, making it adaptable to various analysis scenarios.
One of the standout features of Radare2 is its command-line interface (CLI), which provides a powerful and scriptable environment for performing complex analysis tasks.
This allows users to automate and customize their analysis workflows to suit their needs.
With support for multiple architectures and file formats, Radare2 offers versatility in analyzing binaries across different platforms and environments.
Its graphical user interface (GUI), known as Cutter, provides a more user-friendly option for those who prefer a visual approach to code analysis.
Furthermore, Radare2’s active and supportive community ensures continuous improvement and development of the framework.
With a wealth of documentation, tutorials, and plugins contributed by the community, users can leverage their collective knowledge and resources to enhance their analysis capabilities.
In conclusion, Radare2’s versatility, modularity, and active community support make it a powerful tool in binary analysis and reverse engineering.
Its command-line interface, support for multiple architectures, and extensibility contribute to its effectiveness in unraveling the secrets hidden within binary code.
Features:-
- A comprehensive suite of tools for disassembling, debugging, analyzing, and patching binaries.
- Modular architecture for flexibility and extensibility.
- Powerful command-line interface (CLI) for performing complex analysis tasks and automation.
- Support for multiple architectures and file formats, enhancing versatility.
- Graphical user interface (GUI) known as Cutter for a user-friendly visual approach to code analysis.
- Active and supportive community with extensive documentation, tutorials, and plugins.
- Scriptable environment for customization and automation of analysis workflows.
- Advanced features for binary analysis, including code visualization and graph generation.
- Built-in debugging capabilities for identifying and resolving issues within binaries.
- Continuous improvement and development through community contributions and updates.
Pros:-
- A comprehensive suite of tools for various aspects of binary analysis and reverse engineering.
- Modular architecture allows for flexibility and extensibility, accommodating diverse analysis scenarios.
- Powerful command-line interface (CLI) provides extensive capabilities and scriptability for complex tasks.
- Support for multiple architectures and file formats increases versatility and compatibility.
- The graphical user interface (GUI) option with Cutter provides a user-friendly visual approach to code analysis.
- Active and supportive community contributes to continuous improvement with documentation, tutorials, and plugins.
- A scriptable environment enables customization and automation of analysis workflows.
- Advanced features like code visualization and graph generation enhance the analysis experience.
- Built-in debugging capabilities assist in identifying and resolving issues within binaries.
- The open-source nature encourages collaboration, transparency, and accessibility.
Cons:-
- A steep learning curve, especially for beginners, due to the complexity of the tool and its command-line interface.
- Lack of polished user interface experience compared to some commercial alternatives.
- Potential stability issues or compatibility challenges with certain binaries or platforms.
- Limited official support compared to commercial tools.
- Documentation and resources may not be as comprehensive or readily available for advanced features.
- GUI option (Cutter) may not provide the same level of functionality as the command-line interface.
- Resource-intensive, requiring adequate hardware specifications for optimal performance.
- Limited integrations with other tools or frameworks compared to more established alternatives.
In conclusion, Radare2 offers a powerful and versatile framework for binary analysis and reverse engineering.
While it may have a steep learning curve and potential limitations, its comprehensive feature set, extensibility, and active community support make it a valuable tool for professionals in the field.
7. Immunity Debugger
Immunity Debugger stands as a versatile and powerful tool in the realm of software analysis and vulnerability discovery.
With its innovative features and extensive capabilities, Immunity Debugger empowers security researchers, malware analysts, and software engineers to delve deep into the inner workings of programs and uncover critical insights.
At its core, Immunity Debugger facilitates dynamic software analysis by allowing users to step through code execution, observe program state, and identify potential vulnerabilities.
Its advanced debugging features enable the examination of memory, registers, and stack frames, providing valuable insights into the runtime behavior of the target program.
One of the standout features of Immunity Debugger is its built-in exploit development environment. This feature allows users to craft and test exploits, aiding in vulnerability analysis and penetration testing efforts.
Additionally, Immunity Debugger supports scripting through Python, enabling users to automate tasks, customize analysis workflows, and extend the tool’s capabilities.
What sets Immunity Debugger apart is its active and vibrant community, which contributes to developing plugins and scripts that enhance the tool’s functionalities and offer additional analysis capabilities.
In conclusion, Immunity Debugger is an invaluable software analysis asset.
Its advanced debugging features, exploit development environment, scripting support, and active community equips professionals with the means to uncover vulnerabilities, understand program behavior, and enhance software security.
Features:-
- Advanced debugging features for in-depth analysis of software execution.
- Ability to step through code, and examine memory, registers, and stack frames.
- Built-in exploit development environment for vulnerability analysis and penetration testing.
- Scripting support through Python for task automation and customization.
- Active community contributing plugins and scripts to enhance functionality.
- Dynamic analysis capabilities for runtime behavior observation.
- Memory manipulation and breakpoint management features for targeted analysis.
- Network traffic analysis and packet capture capabilities for network-based vulnerabilities.
- Extensive documentation and resources for ease of use and learning.
- Regular updates and improvements to stay current with emerging technologies and security challenges.
Pros:-
- Advanced debugging features enable in-depth analysis of software execution.
- Built-in exploit development environment aids in vulnerability analysis and penetration testing.
- Scripting support allows for the automation and customization of analysis workflows.
- The active community contributes to plugins and scripts to enhance functionality and expand capabilities.
- Dynamic analysis capabilities provide insights into runtime behavior and program state.
- Memory manipulation and breakpoint management features facilitate targeted analysis.
- Network traffic analysis and packet capture capabilities help uncover network-based vulnerabilities.
- Extensive documentation and resources are available for learning and support.
- Regular updates and improvements ensure the tool stays up-to-date with evolving technologies and security challenges.
Cons:-
- A steeper learning curve, especially for beginners, due to the complexity of software analysis concepts.
- Lack of polished user interface experience compared to some commercial alternatives.
- Potential stability issues or compatibility challenges with certain software or operating systems.
- Limited official support compared to commercial tools.
- Scripting capabilities may require knowledge of Python programming language.
- Resource-intensive, requiring adequate hardware specifications for optimal performance.
- Less widespread adoption compared to some other prominent software analysis tools.
In conclusion, Immunity Debugger offers advanced debugging and analysis features, a built-in exploit development environment, scripting support, and an active community.
While it may have a learning curve and potential limitations, it’s comprehensive functionalities and regular updates contribute to its effectiveness in software analysis and vulnerability discovery.
8. Angr
Angr is a powerful and innovative framework that has revolutionized the field of binary analysis and symbolic execution.
With its unique features and capabilities, Angr empowers security researchers, reverse engineers, and software analysts to tackle complex binaries and unlock hidden secrets.
At its core, Angr leverages symbolic execution, a technique that explores all possible program paths and generates symbolic representations of program inputs.
Analysts can reason about the program’s behavior and discover vulnerabilities or unintended behaviors.
One of the standout features of Angr is its ability to perform constraint solving, which enables the resolution of symbolic expressions and the determination of concrete input values that trigger specific code paths.
With advanced program analysis techniques such as taint analysis, control flow analysis, and data flow analysis, Angr provides a comprehensive framework for understanding binary code and its interactions.
Additionally, Angr supports automation through scripting and provides various plugins to extend its functionalities and adapt it to various analysis scenarios.
In conclusion, Angr is a powerful framework that embraces symbolic execution to provide a deeper understanding of binary code.
Its advanced program analysis techniques, constraint-solving capabilities, and extensibility through plugins make it an invaluable tool for unraveling complex binaries and uncovering vulnerabilities that may be lurking within them.
Features:-
- Symbolic execution-based framework for powerful binary analysis.
- Advanced program analysis techniques, including taint analysis, control flow analysis, and data flow analysis.
- Constraint solving capabilities to resolve symbolic expressions and determine concrete input values.
- Support for automation through scripting, allowing for customized analysis workflows.
- Extensibility through a wide range of plugins, enhancing functionality and adaptability.
- Exploration of all possible program paths to reason about program behavior.
- Detection of vulnerabilities, unintended behaviors, and hidden features within binaries.
- Comprehensive support for various architectures and file formats.
- Integration with other tools and frameworks for a seamless analysis experience.
- Active community support, providing resources, tutorials, and collaboration opportunities.
Pros:-
- Symbolic execution-based framework enables powerful and deep binary analysis.
- Advanced program analysis techniques offer insights into program behavior, vulnerabilities, and hidden features.
- Constraint solving capabilities assist in resolving symbolic expressions and determining concrete input values.
- Automation support through scripting allows for customized and streamlined analysis workflows.
- Extensibility through a wide range of plugins enhances functionality and adaptability to specific needs.
- Exploration of all possible program paths helps in reasoning about complex code structures.
- Comprehensive support for various architectures and file formats increases versatility.
- Integration capabilities with other tools and frameworks enhance the analysis ecosystem.
- Active community support provides resources, tutorials, and collaboration opportunities.
Cons:-
- Steeper learning curve, requiring familiarity with symbolic execution concepts and techniques.
- Potential performance limitations due to the computational complexity of symbolic execution.
- Limited official documentation and support compared to more established tools.
- Challenges with complex or large-scale binaries, potentially resulting in longer analysis times.
- Difficulty in handling certain types of code obfuscation or anti-analysis techniques.
- Resource-intensive, requiring significant computational resources for optimal performance.
- Limited visualization capabilities compared to some other binary analysis tools.
In conclusion, Angr offers a powerful symbolic execution-based framework for binary analysis.
While it may have a learning curve and potential limitations, its advanced analysis techniques, constraint solving capabilities, and active community support make it a valuable tool for professionals in the field.
9. OllyDbg
OllyDbg stands as a prominent and influential debugger in the realm of software analysis and reverse engineering.
With its powerful features and comprehensive capabilities, OllyDbg empowers security researchers, malware analysts, and software engineers to dissect and understand the inner workings of programs.
At its core, OllyDbg is a dynamic debugger that analyzes and manipulates running programs.
Its interactive and real-time debugging capabilities enable users to step through code, inspect registers and memory, and track program flow.
One of the standout features of OllyDbg is its plugin support, which extends its functionality and enhances its capabilities.
Users can customize the debugger, add new features, and automate repetitive tasks through a wide range of community-developed plugins.
With its graphical user interface (GUI), OllyDbg provides a user-friendly and intuitive environment for code analysis.
The GUI offers features such as code and memory views, breakpoints, and disassembly windows, facilitating navigation and analysis of binary code.
Furthermore, OllyDbg supports scripting through its own scripting language, enabling users to automate debugging tasks and customize analysis workflows.
In conclusion, OllyDbg is a powerful debugger that aids professionals in software analysis.
With its dynamic debugging capabilities, plugin support, user-friendly interface, and scripting capabilities, it equips users with the means to dissect, analyze, and understand the intricacies of programs.
Features:-
- Dynamic debugger for real-time analysis and manipulation of running programs.
- Interactive stepping through code, inspecting registers and memory, and tracking program flow.
- Plugin support for extending functionality and enhancing capabilities.
- Customization options to add new features and automate repetitive tasks.
- Graphical user interface (GUI) for intuitive and user-friendly code analysis.
- Code and memory views, breakpoints, and disassembly windows for efficient navigation and analysis.
- Scripting support for automation of debugging tasks and customization of analysis workflows.
- Comprehensive set of debugging features, including conditional breakpoints, watchpoints, and call stack tracing.
- Support for various executable file formats, making it versatile for different software environments.
- Active community support, providing plugins, tutorials, and resources for knowledge sharing and collaboration.
Pros:-
- Dynamic debugger for real-time analysis and manipulation of running programs.
- Interactive stepping through code, inspecting registers and memory, and tracking program flow.
- Plugin support for extending functionality and enhancing capabilities.
- Customization options to add new features and automate repetitive tasks.
- User-friendly graphical user interface (GUI) for intuitive code analysis.
- Code and memory views, breakpoints, and disassembly windows for efficient navigation and analysis.
- Scripting support for automation of debugging tasks and customization of analysis workflows.
- Comprehensive set of debugging features, including conditional breakpoints, watchpoints, and call stack tracing.
- Versatility with support for various executable file formats.
- Active community support, providing plugins, tutorials, and resources for knowledge sharing and collaboration.
Cons:-
- Steeper learning curve, especially for beginners due to the complexity of debugging concepts.
- Potential stability issues or compatibility challenges with certain software or operating systems.
- Limited official documentation and support compared to some commercial tools.
- Limited visualization capabilities compared to some other debugging tools.
- Resource-intensive, requiring adequate hardware specifications for optimal performance.
- Not as widely known or adopted as some other prominent debugging tools.
- Lack of extensive scripting capabilities compared to some other tools.
- Limited integration options with other tools or frameworks.
In conclusion, OllyDbg offers a powerful dynamic debugging environment with a user-friendly interface and plugin support.
While it may have a learning curve and potential limitations, its comprehensive debugging features and active community support make it a valuable tool for software analysis and reverse engineering professionals.
10. x64dbg
x64dbg is a powerful and feature-rich debugger that has gained significant popularity in software analysis and reverse engineering.
With its comprehensive capabilities and innovative features, x64dbg empowers security researchers, malware analysts, and software engineers to delve deep into the intricacies of programs and uncover critical insights.
At its core, x64dbg is designed to provide advanced debugging capabilities for 64-bit executables.
Its dynamic analysis features allow users to step through code, examine registers and memory, and track program execution with precision.
One of the standout features of x64dbg is its graphical user interface (GUI), which offers an intuitive and user-friendly environment for code analysis.
The GUI provides features such as code and memory views, breakpoints, and disassembly windows, facilitating efficient navigation and analysis of binary code.
With its plugin support, x64dbg enables users to extend its functionality and customize the debugger to suit their needs.
The vibrant community surrounding x64dbg contributes a wide range of plugins, enhancing the capabilities and expanding the analysis options available.
Furthermore, x64dbg supports scripting through its integrated scripting engine, allowing users to automate tasks, create custom analysis scripts, and enhance their debugging workflows.
In conclusion, x64dbg is a powerful debugger that equips professionals in the field of software analysis with advanced capabilities.
Its dynamic analysis features, user-friendly GUI, plugin support, and scripting capabilities make it an invaluable tool for dissecting, analyzing, and understanding the inner workings of programs.
Features:-
- Advanced debugging capabilities for 64-bit executables.
- Dynamic analysis features for stepping through code and examining registers and memory.
- Graphical user interface (GUI) for an intuitive and user-friendly code analysis environment.
- Code and memory views, breakpoints, and disassembly windows for efficient navigation and analysis.
- Plugin support to extend functionality and customize the debugger.
- Active community contributing a wide range of plugins to enhance capabilities.
- Integrated scripting engine for task automation and custom analysis scripts.
- Support for various executable file formats, increasing versatility.
- Comprehensive set of debugging features, including conditional breakpoints and watchpoints.
- Regular updates and improvements to ensure compatibility with evolving technologies and security challenges.
Pros:-
- Advanced debugging capabilities specifically tailored for 64-bit executables.
- Dynamic analysis features enable precise examination of code, registers, and memory.
- User-friendly graphical user interface (GUI) enhances the code analysis experience.
- Code and memory views, breakpoints, and disassembly windows facilitate efficient navigation and analysis.
- Plugin support allows for customization and extension of the debugger’s functionality.
- Active community contributing a wide range of plugins to enhance capabilities and expand analysis options.
- Integrated scripting engine enables automation of tasks and customization of analysis workflows.
- Versatile support for various executable file formats.
- Comprehensive set of debugging features, including conditional breakpoints and watchpoints.
- Regular updates and improvements to address compatibility and security concerns.
Cons:-
- Steep learning curve, particularly for beginners unfamiliar with debugging concepts.
- Potential stability issues or compatibility challenges with certain software or operating systems.
- Limited official documentation and support compared to some commercial tools.
- Visualizations may not be as extensive or refined as other debugging tools.
- Resource-intensive, requiring sufficient hardware specifications for optimal performance.
- Relatively lesser known or adopted compared to some other prominent debugging tools.
- Limited integration options with other tools or frameworks.
In conclusion, x64dbg offers advanced debugging capabilities for 64-bit executables.
While it may have a learning curve and potential limitations, its comprehensive features, user-friendly interface, plugin support, and active community make it a valuable tool for software analysis and reverse engineering professionals.
📗FAQ’s
What are the tools used for reverse engineering?
One of the most popular tools for reverse engineering is IDA Pro. Known for its powerful disassembly engine and comprehensive analysis capabilities, it allows reverse engineers to navigate through complex binaries and gain a deep understanding of the code.
Another notable tool is Ghidra, an open-source reverse engineering framework developed by the National Security Agency (NSA). It provides disassembly, decompilation, and scripting features, making it a versatile choice for analyzing binaries.
OllyDbg and x64dbg offer advanced debugging features for dynamic analysis, allowing analysts to step through code, inspect registers, and track program execution in real time.
In addition, Radare2, Hopper Disassembler, and Binary Ninja are among the tools widely used in the reverse engineering community, each offering its unique set of features and capabilities.
Other supporting tools like debuggers, decompilers, and memory analysis play crucial roles in reverse engineering.
In conclusion, reverse engineering tools enable analysts to delve deep into binaries, understand their inner workings, and discover valuable insights.
The choice of tools depends on the specific analysis requirements, with each tool offering its strengths and capabilities in different aspects of the reverse engineering process.
Here’s a table showcasing some of the best reverse engineering tools based on user reviews.
| Tool Name | Description | Price | User Rating (out of 5) |
|---|---|---|---|
| IDA Pro | Advanced disassembler and debugger | $2,199/year | 4.7 |
| Ghidra | Open-source software reverse engineering suite | Free | 4.5 |
| Radare2 | UNIX-like reverse engineering framework | Free | 4.3 |
| Binary Ninja | Reverse engineering platform with advanced UI | $499/year | 4.6 |
| Hopper Disassembler | Mac OS X and Linux disassembler and debugger | $89-$299 | 4.4 |
| OllyDbg | 32-bit assembler-level analyzing debugger | Free | 4.2 |
| Immunity Debugger | Powerful Windows debugger and reverse engineer | Free | 4.3 |
| x64dbg | Open-source x86/x64 debugger with plugin support | Free | 4.1 |
| JEB Decompiler | Android app decompiler and reverse engineering | $2,999/year | 4.5 |
| Angr | Platform-agnostic binary analysis framework | Free | 4.3 |
Why is Reverse Engineering Illegal?
Reverse engineering is a process that involves analyzing and understanding the inner workings of a product or software by deconstructing it.
While this practice is widely used for legitimate purposes such as interoperability, security analysis, and software development, there are certain scenarios where reverse engineering can be considered illegal.
The legality of reverse engineering depends on various factors, including the jurisdiction, the nature of the subject being analyzed, and the purpose behind the activity.
In many cases, the act of reverse engineering itself is not inherently illegal. However, it can violate intellectual property rights or infringe upon contractual agreements, leading to legal repercussions.
One primary reason reverse engineering may be illegal is when it involves unauthorized access or circumvention of protective measures such as encryption, access controls, or digital rights management (DRM) mechanisms.
These measures are put in place to safeguard intellectual property and trade secrets, and bypassing them can be seen as a violation of the law.
Furthermore, suppose reverse engineering is conducted with the intent to create counterfeit products, replicate patented inventions, or engage in industrial espionage.
In that case, it can be deemed an infringement of intellectual property rights, patents, or trade secrets, leading to legal consequences.
It’s crucial to emphasize that the legal landscape surrounding reverse engineering is complex and varies across jurisdictions.
In some instances, exceptions and limitations, such as fair use or interoperability exemptions, may exist, allowing for lawful reverse engineering activities under specific circumstances.
To navigate the legal intricacies of reverse engineering, it is advisable to consult with legal professionals who specialize in intellectual property law and have a deep understanding of the jurisdiction in question.
This ensures compliance with the law while harnessing the benefits of reverse engineering for legitimate purposes.
In summary, while reverse engineering is not inherently illegal, its legality depends on various factors and can be subject to intellectual property rights, contractual agreements, and protective measures.
It is essential to navigate the legal complexities carefully and seek legal guidance to ensure compliance and avoid legal repercussions when engaging in reverse engineering activities.
What are the Tools for Reverse Engineering in Linux?
When it comes to the fascinating realm of reverse engineering in the Linux environment, a diverse array of powerful tools empowers analysts and security researchers.
These tools offer a comprehensive set of capabilities for dissecting, and understanding compiled executables, uncovering vulnerabilities, and unraveling the inner workings of software systems.
Radare2 stands out as a versatile and feature-rich framework for reverse engineering. Its command-line interface and modular architecture provide a powerful environment for low-level analysis, binary manipulation, and code visualization.
For those seeking a robust disassembler and debugger, Ghidra comes to the forefront. Developed by the National Security Agency (NSA), this tool offers various features, including decompilation, scripting, and collaborative reverse engineering capabilities.
IDA Pro is another revered tool widely used in the reverse engineering community. Its interactive and multi-processor disassembler and its extensive plugin ecosystem enable advanced analysis and exploitation of binaries.
Binary Ninja deserves mention as a user-friendly yet powerful tool for reverse engineering. It boasts a modern and intuitive interface and advanced analysis capabilities, making it a favorite among beginners and seasoned analysts.
Additionally, Angr is a platform-agnostic binary analysis framework that aids in symbolic execution, binary lifting, and vulnerability discovery, enhancing the reverse engineering workflow.
These tools for reverse engineering in the Linux ecosystem serve as a testament to the vibrant and dynamic nature of the field.
Whether one seeks disassembly, decompilation, debugging, or vulnerability analysis, this arsenal of tools equips researchers with the means to delve into the depths of compiled executables, uncovering hidden secrets and unraveling the complexities of software systems.
The Four Steps of Reverse Engineering
Reverse engineering is typically conducted through a series of well-defined steps.
These steps include (1) observation and documentation, where the product or system is observed, and relevant information is documented.
(2) Analysis and disassembly involve breaking down the product or system into its constituent parts and analyzing their characteristics.
(3) Reversing the design entails reconstructing the product or system’s design based on the information gathered.
Finally, (4) testing and verification ensure that the reverse-engineered product or system functions as intended.
A Famous Example of Reverse Engineering
One famous example of reverse engineering is the IBM PC BIOS (Basic Input/Output System).
In the early 1980s, Phoenix Technologies reverse-engineered the IBM PC BIOS, allowing them to create a compatible version that could be used on non-IBM computers.
This breakthrough significantly expanded the personal computer market by enabling the development of IBM-compatible systems.
Is Reverse Engineering Illegal in the US?
Reverse engineering is generally legal in the United States, provided it does not infringe upon intellectual property rights or other legal protections.
However, certain acts related to reverse engineering, such as the circumvention of technological protection measures, may be restricted under the Digital Millennium Copyright Act (DMCA).
Understanding and complying with applicable laws and regulations is crucial when engaging in reverse engineering activities.
Why Do Hackers Use Reverse Engineering?
Hackers often employ reverse engineering as a powerful tool in their arsenal. By dissecting software, firmware, or hardware, hackers can uncover vulnerabilities and weaknesses that can be exploited for unauthorized access or malicious purposes.
Reverse engineering allows hackers to understand how a system works, identify potential entry points, and develop exploits or modifications to achieve their goals.
Disadvantages of Reverse Engineering
While reverse engineering can provide valuable insights, it also has its drawbacks.
Some disadvantages include the potential violation of intellectual property rights, the possibility of legal repercussions, the time and effort required for analysis and reconstruction, and the uncertainty of achieving an accurate replica or understanding of the original design.
The Most Famous Reverse Engineering
One of the most notable instances of reverse engineering is the Apple iPhone.
In 2007, shortly after the iPhone’s release, hackers successfully reverse-engineered the device’s operating system, enabling the installation of unauthorized applications.
This breakthrough opened the doors to a thriving ecosystem of third-party apps and customization options, contributing to the iPhone’s immense popularity and revolutionizing the smartphone industry.
Real-Time Example of Reverse Engineering
A real-time example of reverse engineering can be found in the automotive industry. When a competing car manufacturer aims to understand the design and technology of a successful vehicle, they may resort to reverse engineering.
By carefully dissecting and analyzing the vehicle, they can gain insights into engineering solutions, manufacturing techniques, and advanced features, allowing them to improve their designs and stay competitive.
Conclusion
In conclusion, reverse engineering is fortified by an extensive arsenal of powerful tools that enable analysts, researchers, and cybersecurity professionals to unravel the intricacies of compiled executables.
The list of reverse engineering tools showcases diverse capabilities and functionalities, catering to different aspects of the reverse engineering process.
From the advanced disassembler and debugger IDA Pro to the open-source and versatile framework Radare2, each tool brings its unique strengths and features to the table.
The collaborative capabilities of Ghidra, the user-friendly interface of Binary Ninja, and the platform-agnostic framework Angr contribute to the richness of the available tools.
These tools facilitate code analysis, binary manipulation, vulnerability discovery, and software comprehension.
Whether it’s delving into low-level machine instructions, exploring control flow, or uncovering hidden secrets, the tools for reverse engineering provide researchers with invaluable insights and understanding.
It’s important to note that selecting the right tool depends on individual needs, preferences, and the context of the reverse engineering project.
The tools mentioned in the list represent a snapshot of the current landscape, but staying updated with the latest advancements and emerging tools is always advisable.
Ultimately, the wide range of reverse engineering tools empowers professionals to navigate the complexities of compiled executables, unraveling the mysteries and making significant contributions to software security, vulnerability analysis, and malware research.